Jul 21, 2025Ravie LakshmananSpyware / Mobile Security Cybersecurity researchers have unearthed new Android spyware artifacts that are likely affiliated with…
Organisations running on-premise instances of Microsoft’s SharePoint collaboration and document management platform should update without delay after multiple reports of…
September 4, 2009 — After much spirited debate I have come to the conclusion that the argument presented below is…
Cybersecurity leaders are tasked with protecting their organizations from external and, sometimes, internal threats. But if CISOs and other technology…
A sophisticated new ransomware strain named KAWA4096 has emerged in the cybersecurity landscape, showcasing advanced evasion techniques and borrowing design…
Trustwave SpiderLabs has played a crucial role in monitoring new ransomware variants in the incredibly unstable ransomware threat landscape of…
Ok, just a few random thoughts; I’ll do a real post later on this once things are fleshed out more….
Microsoft on Saturday warned that hackers are exploiting a critical vulnerability in SharePoint, dubbed ToolShell, to launch attacks against on-premises…
A critical security vulnerability in Laravel’s Livewire framework has been discovered that could expose millions of web applications to remote…
Threat actors are increasingly adopting AI-powered cloaking services to obfuscate phishing domains, counterfeit e-commerce sites, and malware distribution endpoints from…
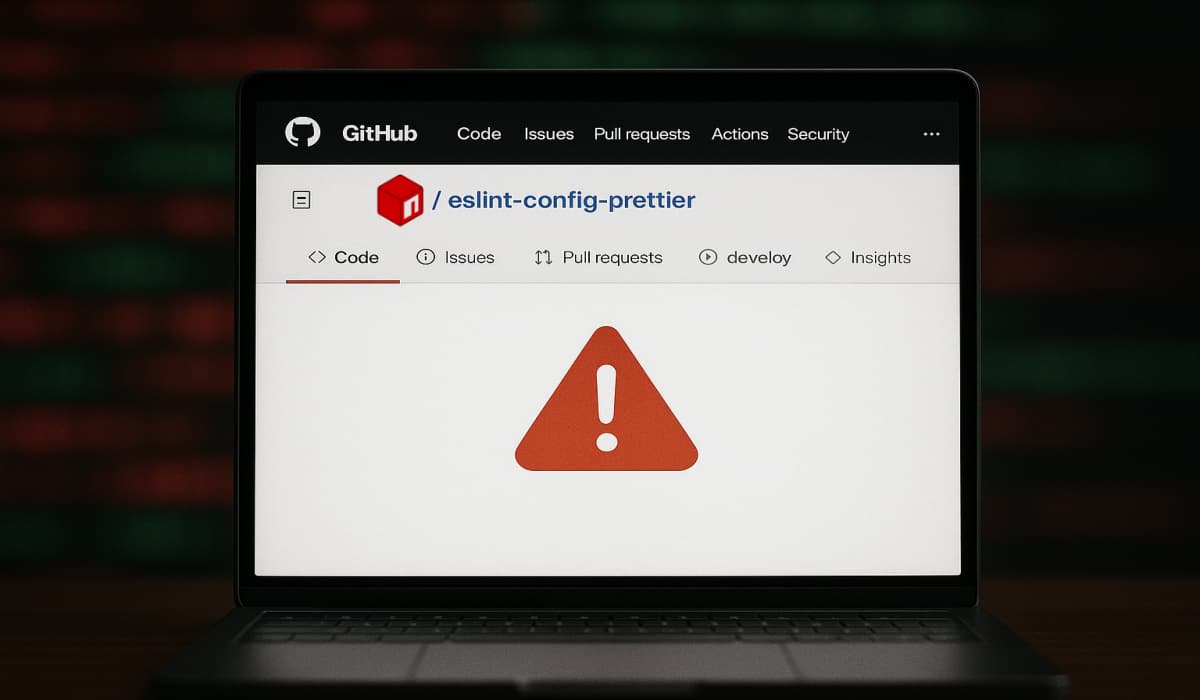
A phishing campaign targeting JavaScript developers has led to the compromise of several popular npm packages, including eslint-config-prettier. The breach…
Last year, security company KnowBe4 helped spark a wave of interest in fraudulent workers when it revealed extensive details of…