A European trade body is facing criticism for striking a deal with Microsoft that allows its members to host and…
Listen to the article 2 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
The Japanese police have released a Phobos and 8-Base ransomware decryptor that lets victims recover their files for free, with…
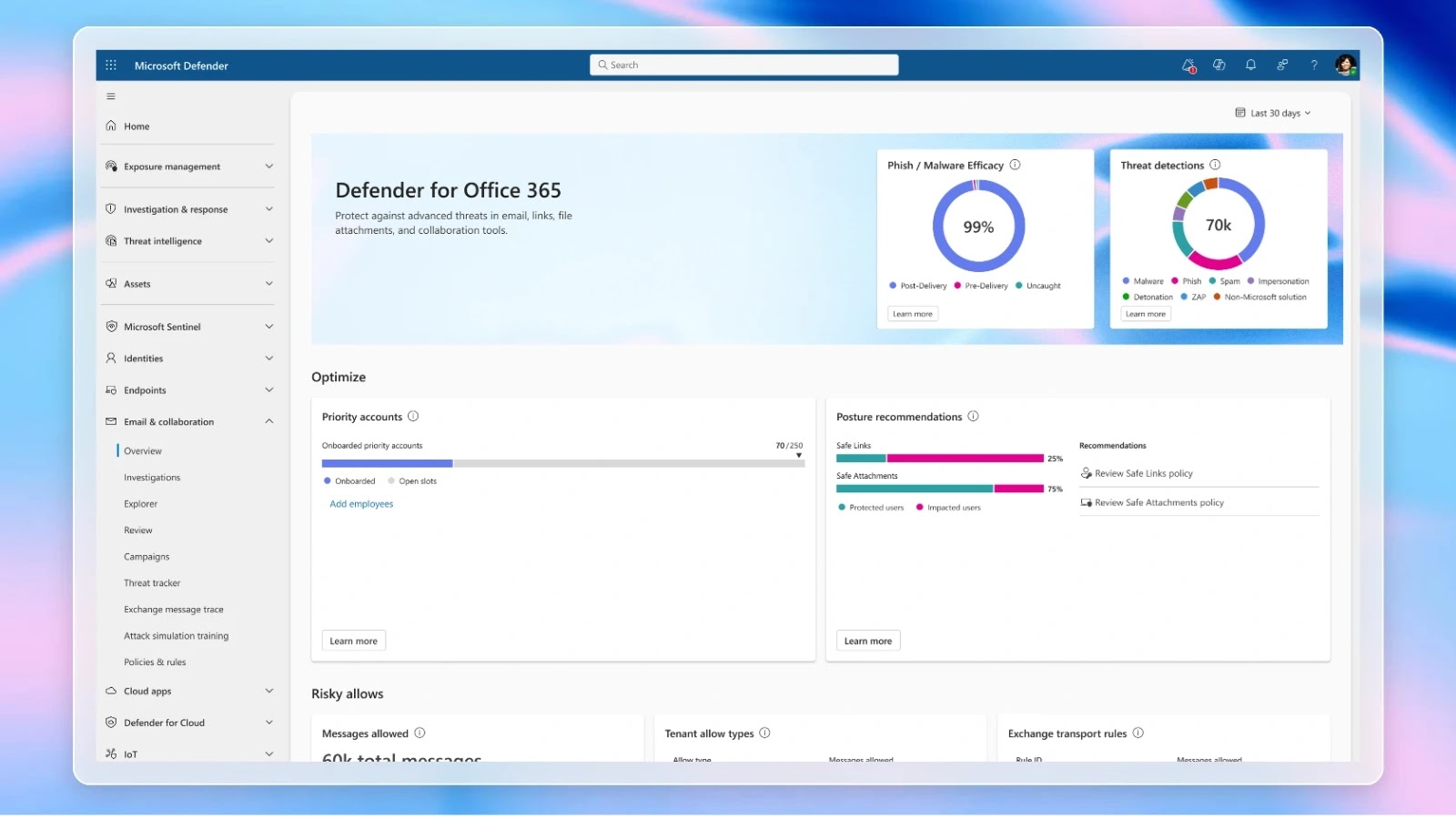
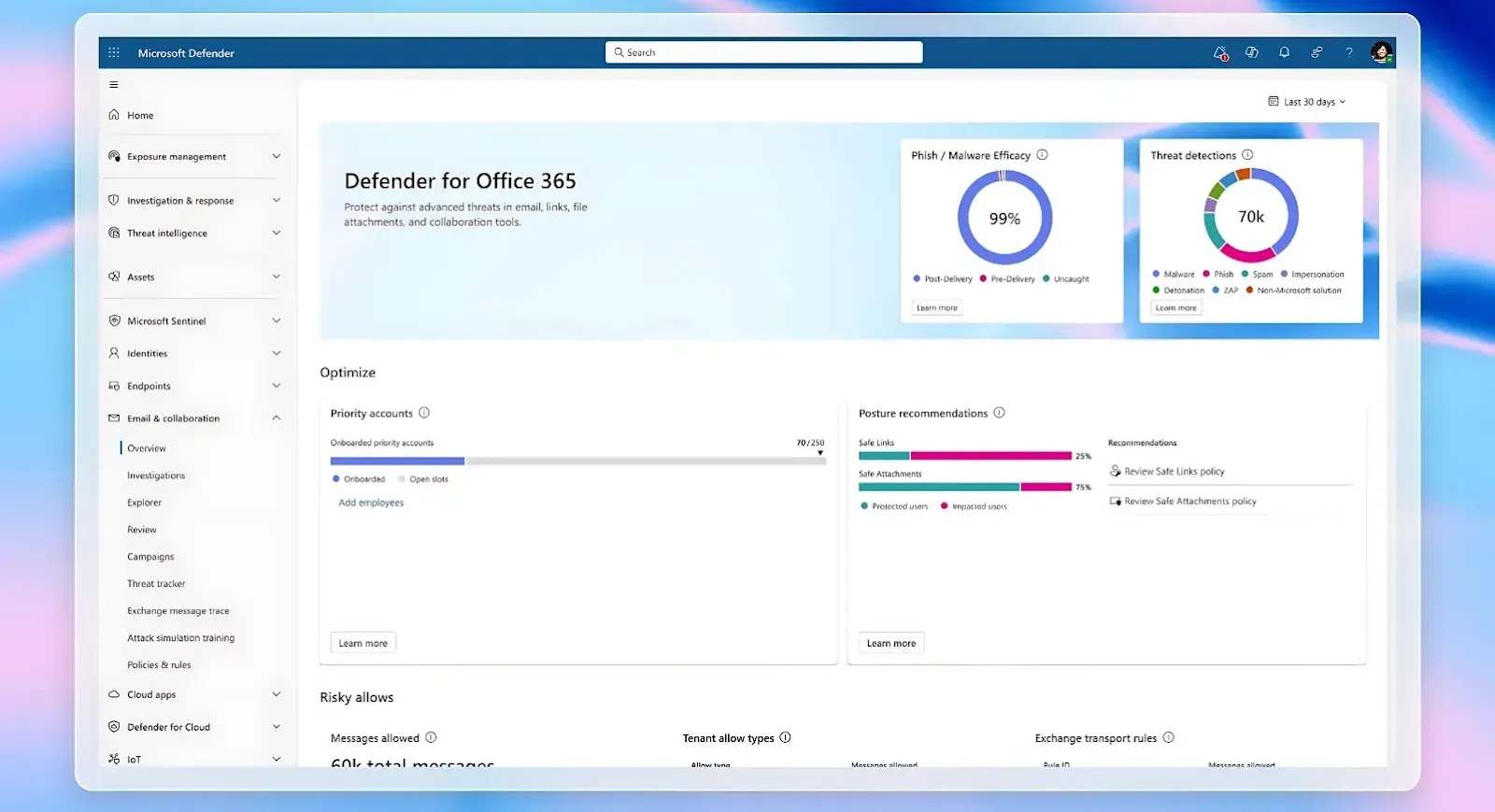
Microsoft today announced the rollout of a revamped customer dashboard in Microsoft Defender for Office 365, designed to deliver unprecedented…
Topsec and Venustech were two firms alleged to have assisted these efforts. Topsec employed a number of former Honkers, including…
Microsoft has announced significant transparency improvements for its email security platform, introducing a new customer-facing dashboard that provides detailed visibility…
In a rare and urgent late-night address, a senior Singapore official confirmed that the country is currently facing a sophisticated…
Researchers are seeing exploitation attempts for the CVE-2025-48927 vulnerability in the TeleMessage SGNL app, which allows retrieving usernames, passwords, and…
Three critical vulnerabilities in the Sophos Intercept X for Windows product family could allow local attackers to achieve arbitrary code…
Grafana Labs has released critical security patches addressing two significant vulnerabilities that could enable attackers to redirect users to malicious…
The UK government is on a mission to loosen the grip that legacy IT suppliers have on public sector IT…
As the U.S. government contemplates additional sanctions on Moscow, the United Kingdom went ahead and levied its own Friday against…