The Taiwanese semiconductor industry has become the target of spear-phishing campaigns undertaken by three Chinese state-sponsored threat actors. “Targets of…
A critical vulnerability in Cisco’s Unified Intelligence Center (CUIC) web-based management interface has been classified with high severity, allowing authenticated…
A severe remote code execution (RCE) vulnerability has been discovered in Microsoft SharePoint that allows attackers to execute arbitrary code…
UNC6148 deploys Overstep malware on SonicWall devices, possibly for ransomware operations Pierluigi Paganini July 17, 2025 UNC6148 targets SonicWall devices…
SonicWall’s end-of-life SMA 100 series appliances are again on the front line after investigators unearthed a covert campaign that couples…
Cybersecurity researchers have identified an emerging attack campaign where threat actors are weaponizing Scalable Vector Graphics (SVG) files to deliver…
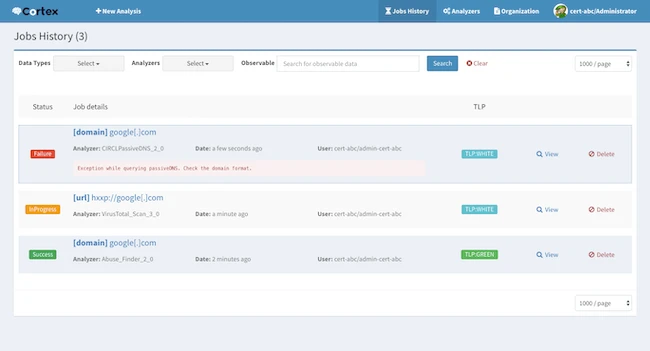
When it comes to spotting threats, security teams need tools that can pull data from all over and make it…
A trio of newly disclosed CVE-2025-6230, CVE-2025-6231 and CVE-2025-6232 underscores how a single trusted OEM utility can become a springboard…
Google’s Threat Intelligence Group (GTIG) has uncovered a sophisticated cyberattack campaign targeting end-of-life SonicWall Secure Mobile Access (SMA) 100 series…
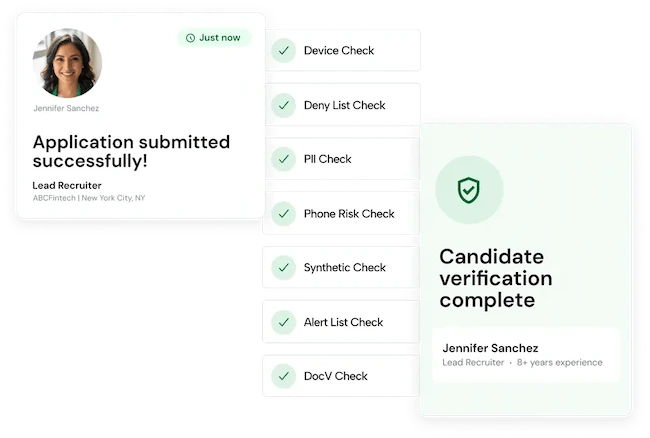
Socure launched Workforce Verification solution to address the growing threat of employee fraud. Socure’s Workforce Verification adapts its enterprise-grade identity…
Co-op has confirmed that the personal details of all 6.5 million of its members were stolen in a cyberattack earlier…
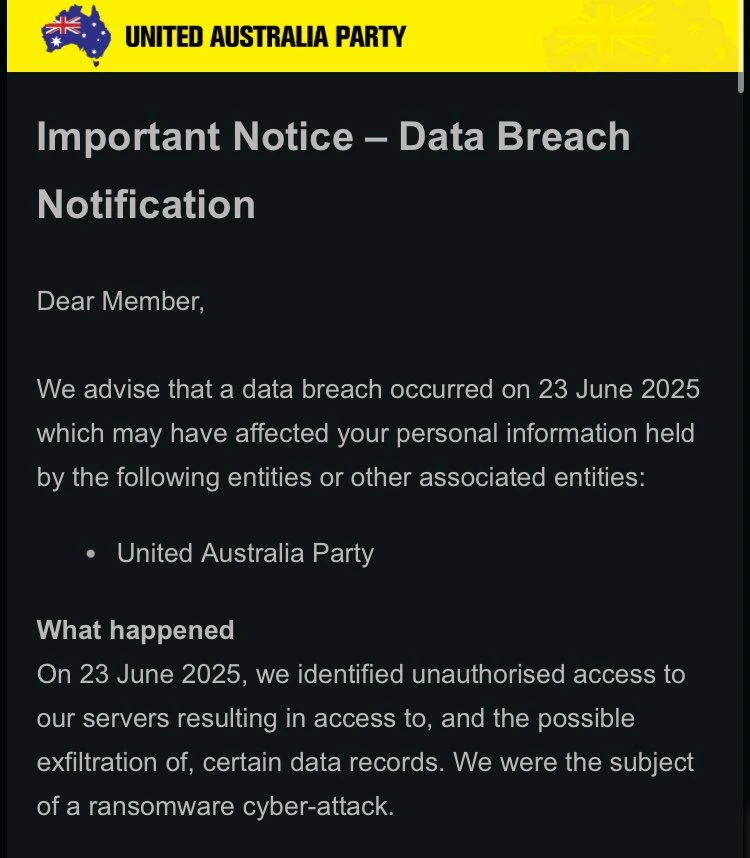
The United Australia Party (UAP), led by mining magnate Clive Palmer, has confirmed that it fell victim to a cyberattack…