The cybersecurity community continues to grapple with the lingering effects of the XZ Utils backdoor, a sophisticated supply chain attack…
Microsoft has disclosed three critical security vulnerabilities in its Office suite that could enable attackers to execute malicious code remotely…
Fake Minecraft clone Eaglercraft 1.12 Offline spreads NjRat spyware stealing passwords, spying via webcam and microphone, warns Point Wild security…
A sophisticated cybercriminal operation disguised as a Ukrainian Web3 development team has been targeting job seekers through weaponized NPM packages,…
Microsoft has disclosed critical security vulnerabilities in Exchange Server that could enable attackers to conduct network-based spoofing attacks and tamper…
When it comes to transcribing videos, technical jargon can pose several challenges. However, with the right approach, you can make…
Aug 13, 2025The Hacker NewsArtificial Intelligence / Identity Security The AI revolution isn’t coming. It’s already here. From copilots that…
Microsoft released security patches addressing a significant vulnerability in Windows Remote Desktop Services that could allow unauthorized attackers to launch…
Fortinet has released patches for a critical OS command injection vulnerability (CVE-2025-25256) in FortiSIEM, after practical exploit code surfaced in…
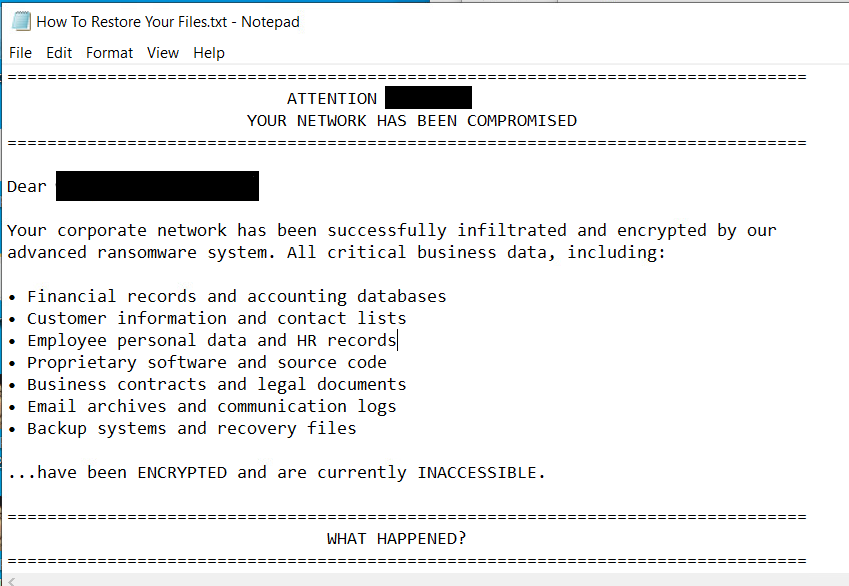
Charon Ransomware targets Middle East with APT attack methods Pierluigi Paganini August 13, 2025 New Charon ransomware targets Middle East…
If you are unaware of what’s running in your environment, you can’t patch, monitor, or secure it. The simple fact…
A sophisticated cybercriminal operation disguised as a Ukrainian Web3 development team has been targeting job seekers through weaponized NPM packages,…