An international law enforcement action dismantled a Romanian ransomware gang known as ‘Diskstation,’ which encrypted the systems of several companies…
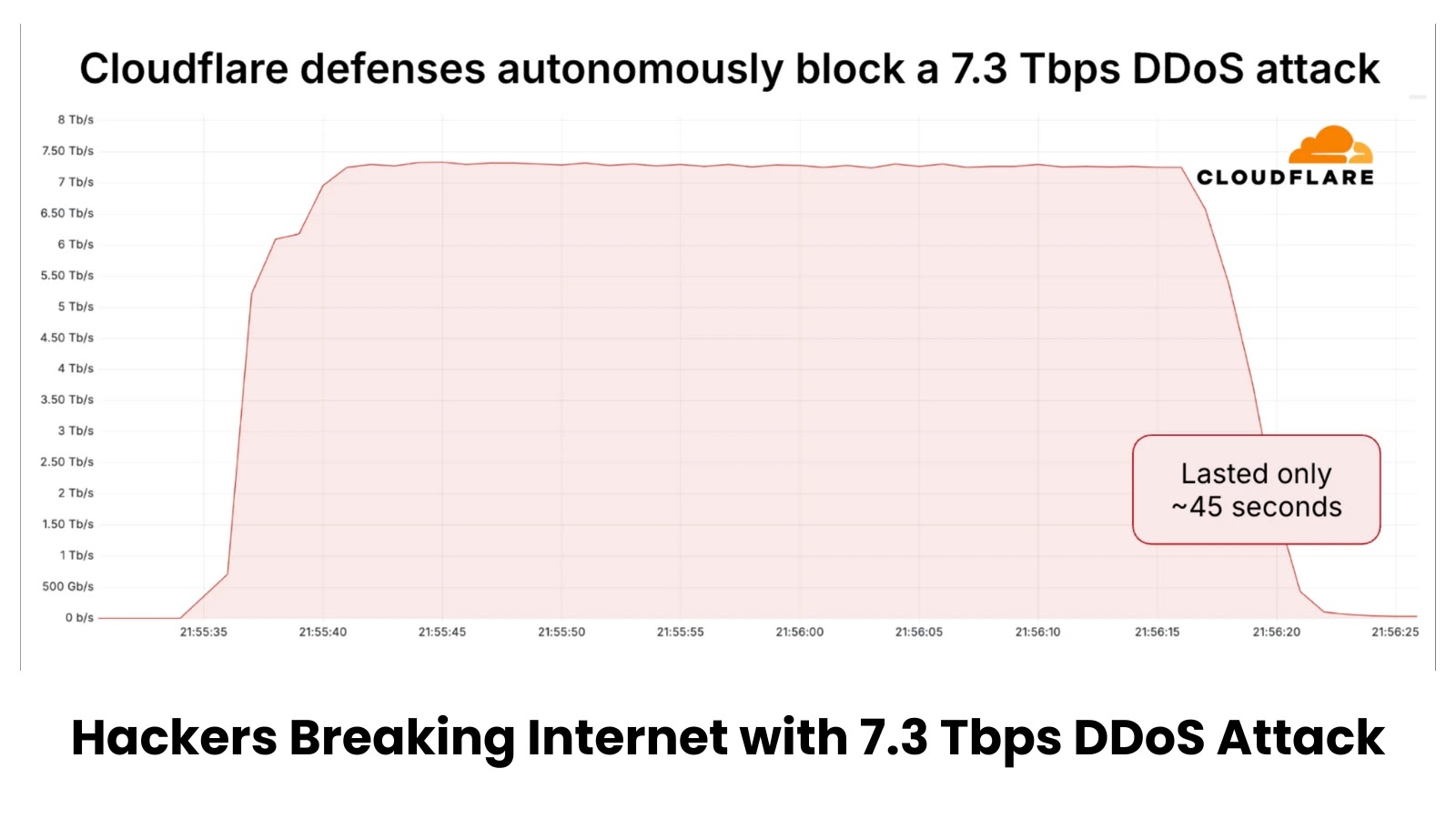
The cybersecurity landscape has witnessed a paradigm shift in 2025, with Distributed Denial of Service (DDoS) attacks reaching unprecedented levels…
Iran’s Islamic Revolutionary Guard Corps (IRGC) has increased its asymmetric cyber operations in response to recent U.S. attacks on Iranian…
Listen to the article 3 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
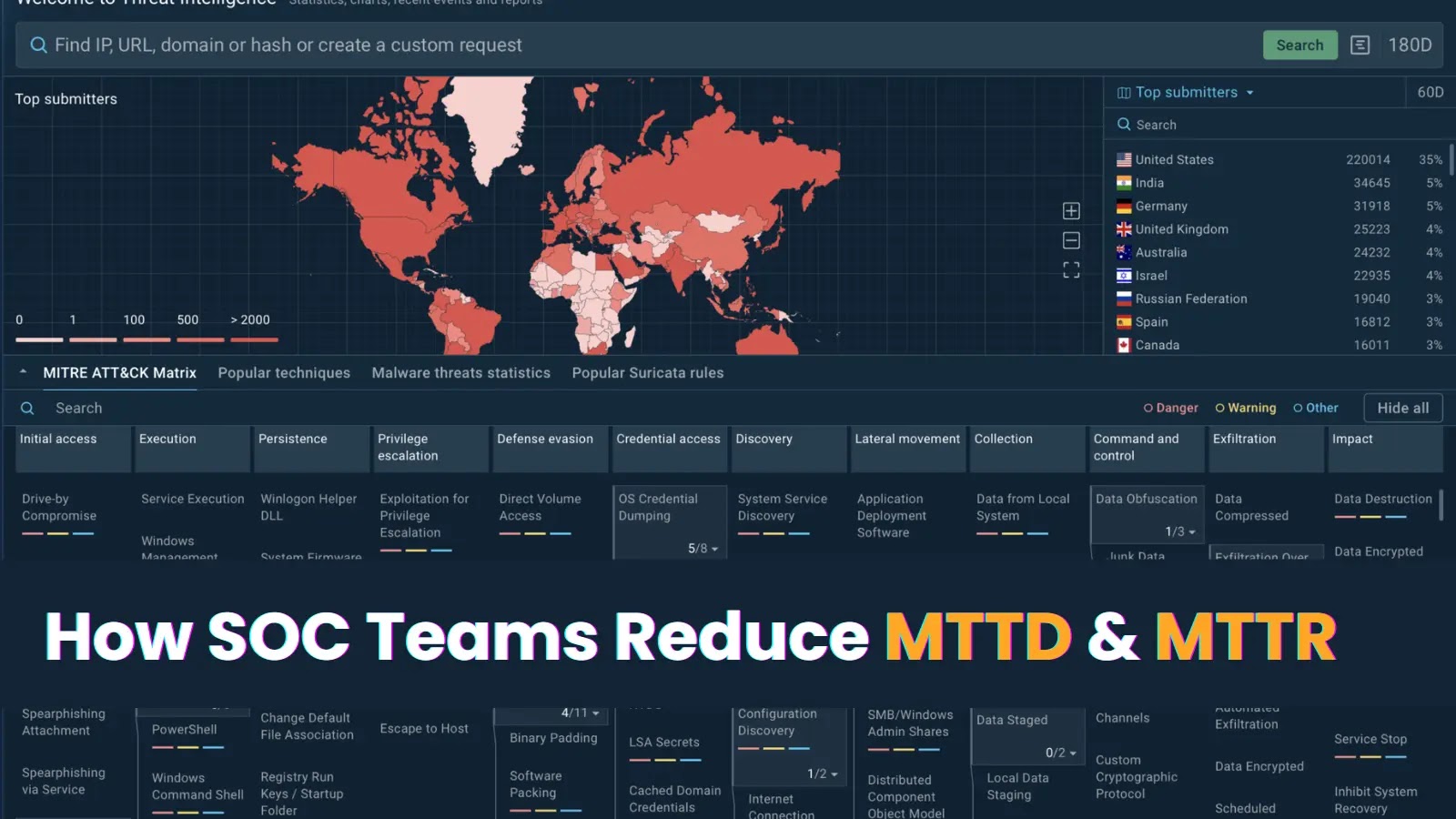
Security Operations Centers (SOCs) face a fundamental challenge: distinguishing genuine threats from false positives while maintaining rapid response times. The…
Albemarle County, Virginia, discovered irregularities in its IT infrastructure under a sophisticated ransomware attack. The breach was quickly recognized by…
Cybersecurity researchers have shed light on a new ransomware-as-a-service (RaaS) operation called GLOBAL GROUP that has targeted a wide range…
Dive Brief: A global malware attack could infect approximately one-quarter of the world’s computer systems, according to a new report…
Cybersecurity researchers have identified a sophisticated international fraud campaign that leverages impersonated news websites from major outlets including CNN, BBC,…
Microsoft has detailed how its Security Copilot, an AI-powered tool, is transforming security and IT operations by embedding generative AI…
The UK’s National Cyber Security Centre (NCSC) has lifted the lid on a Vulnerability Research Initiative (VRI) programme designed to…
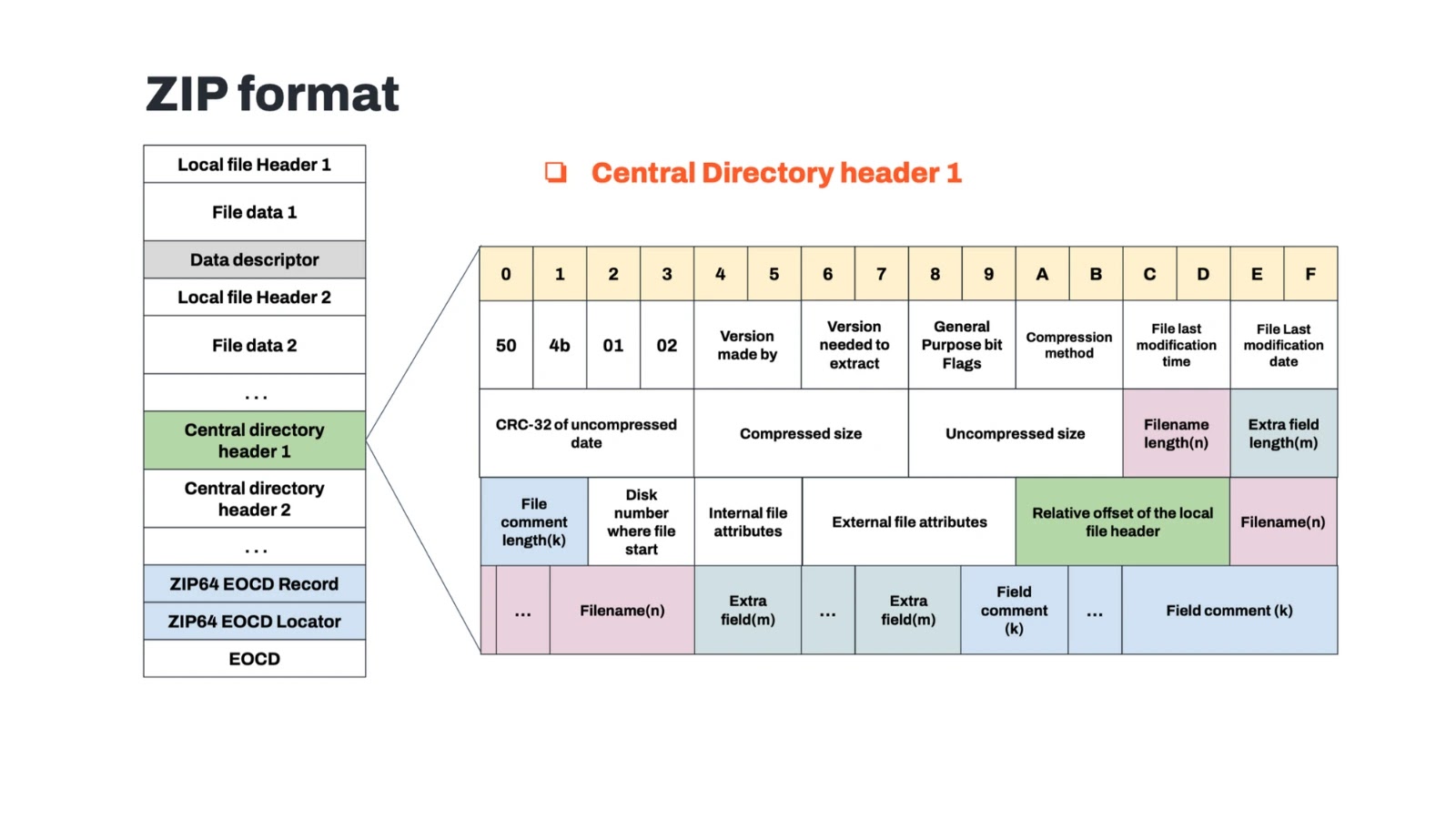
Sophisticated Android malware variant exploits ZIP-level manipulation and dynamic code loading to evade detection while conducting ad fraud operations targeting…