Hill ASC Inc., operating as Hill Associates and based in Rockville, Maryland, has agreed to a multimillion-dollar settlement with the…
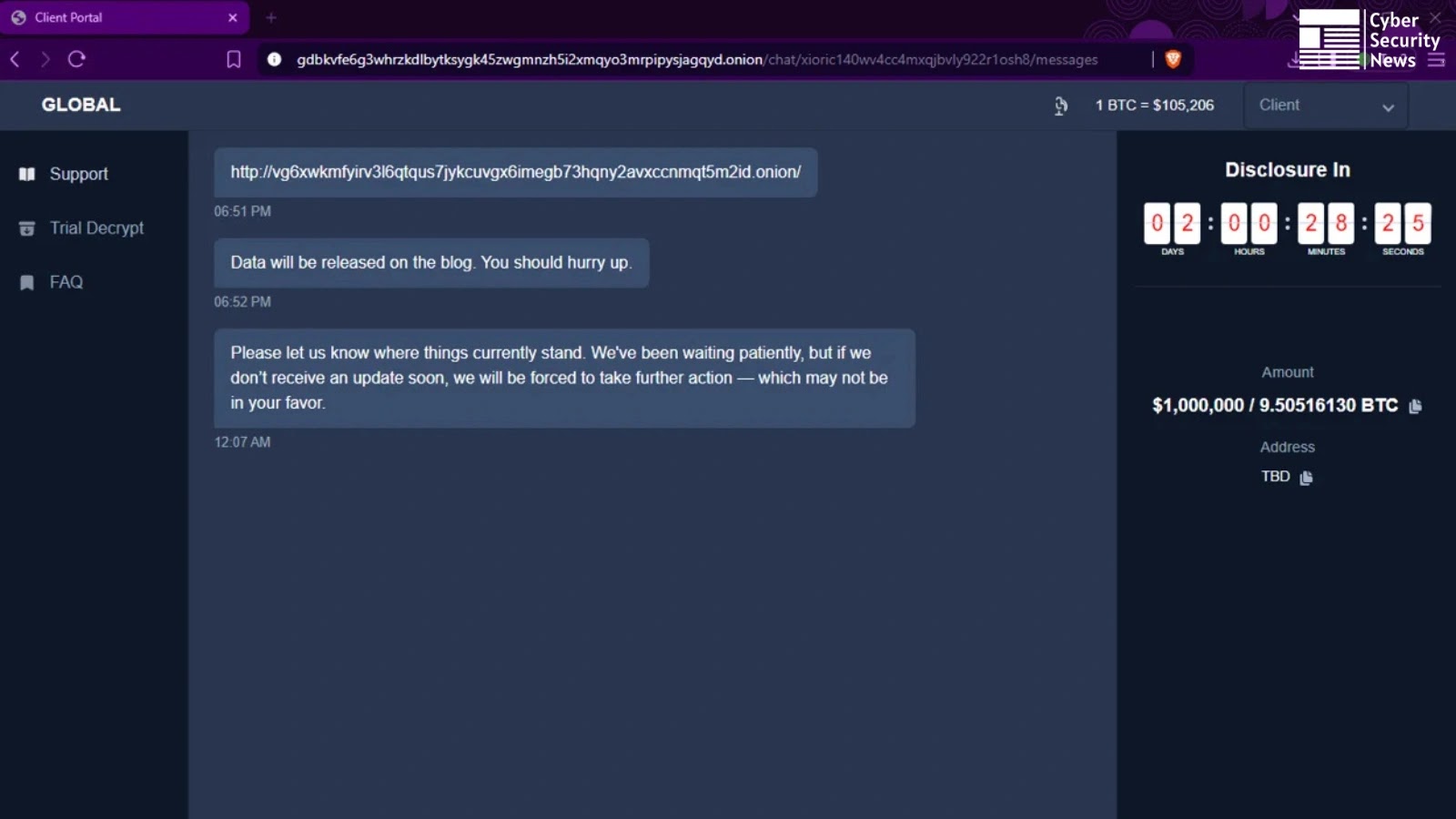
A sophisticated new ransomware-as-a-service operation has emerged with advanced AI-powered negotiation capabilities and mobile management features, targeting organizations across healthcare,…
DShield honeypots have reported previously unheard-of log quantities in a startling increase in cyber reconnaissance activity, with some subnets producing…
Artificial intelligence (AI) is now a part of everyday life, from customer service chatbots, to autocomplete in Word documents. Use…
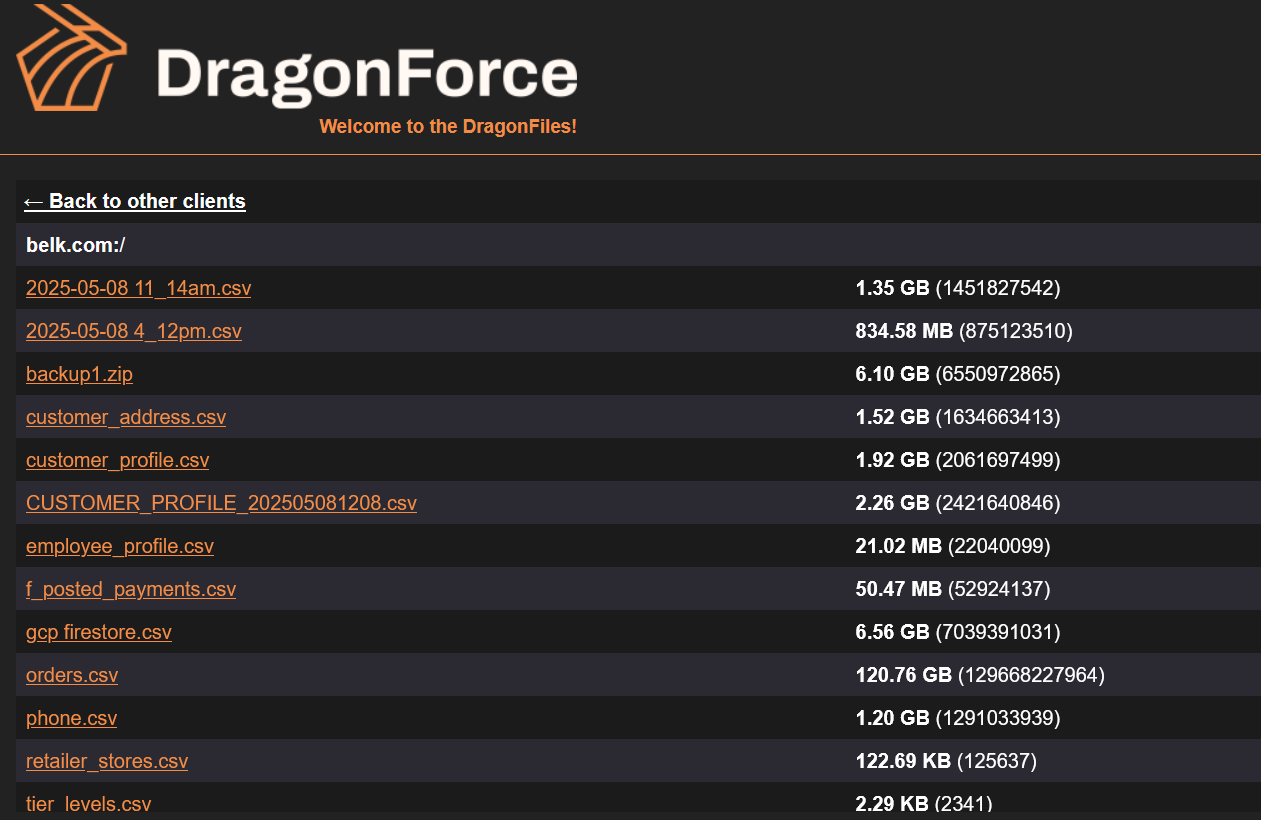
Belk hit by May cyberattack: DragonForce stole 150GB of data Pierluigi Paganini July 15, 2025 Ransomware group DragonForce claims it…
A new variant of the Konfety Android malware emerged with a malformed ZIP structure along with other obfuscation methods that…
GitGuardian, the leader in automated secrets detection and remediation, today announced the launch of its Model Context Protocol (MCP) Server, a…
The Octalyn Forensic Toolkit, which is openly accessible on GitHub, has been revealed as a powerful credential stealer that poses…
UK pet owners are being hit with convincing scam emails demanding microchip registration renewals, and the source of the problem…
UEFI firmware running on 100+ Gigabyte motherboard models is affected by memory corruption vulnerabilities that may allow attackers to install…
Cybersecurity researchers have charted the evolution of a widely used remote access trojan called AsyncRAT, which was first released on…
A survey of IT asset managers (ITAM) and software asset managers (SAM) in organisations that use Java has revealed that…