On the same day xAI announced that its new Grok 4 tool will now be available to the federal government,…
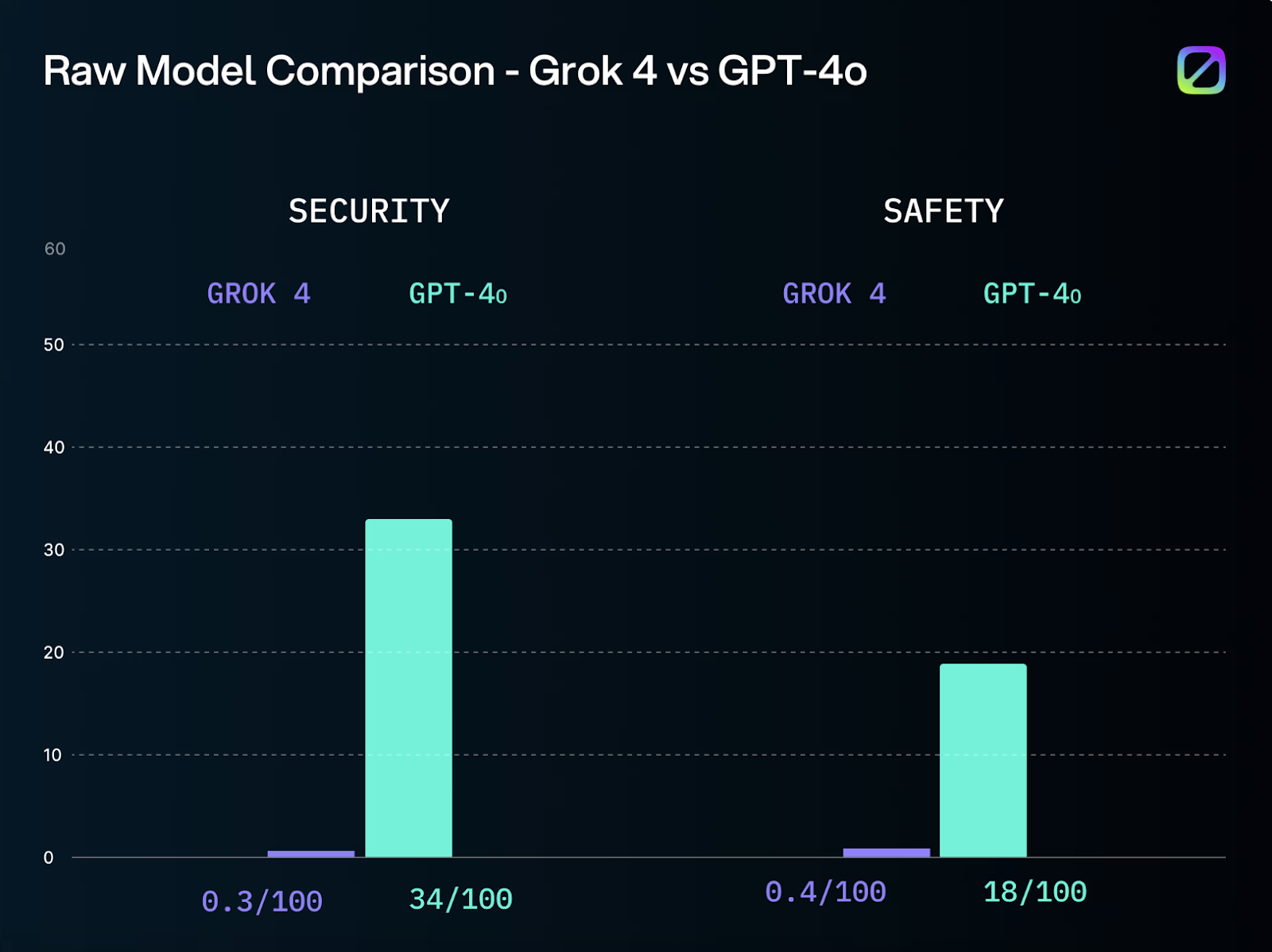
Elon Musk’s Grok-4 AI was compromised within 48 hours. Discover how NeuralTrust researchers combined “Echo Chamber” and “Crescendo” techniques to…
Jul 14, 2025The Hacker NewsSecrets Management / SaaS Security While phishing and ransomware dominate headlines, another critical risk quietly persists…
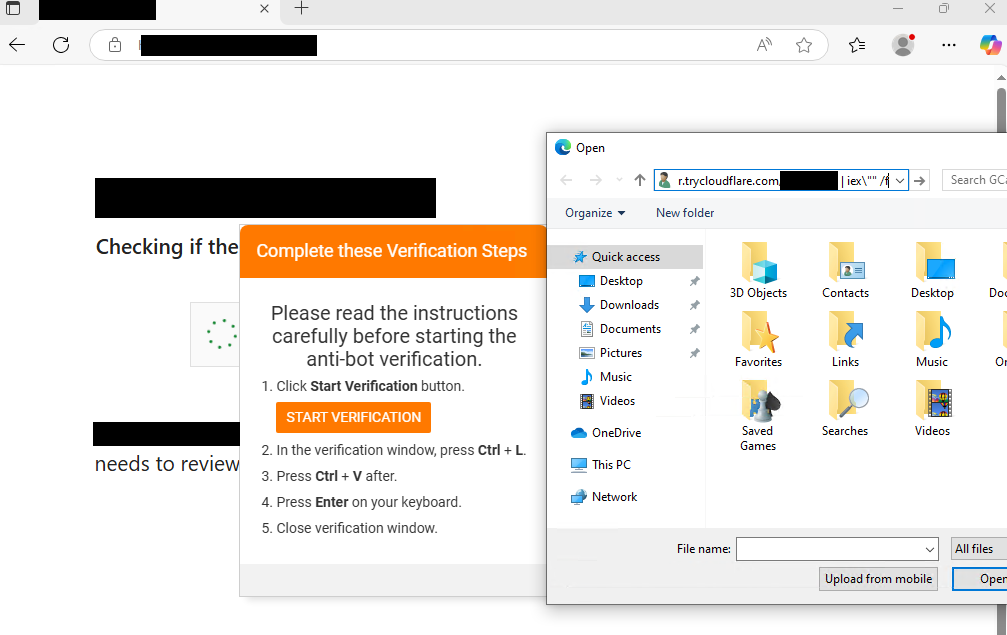
Hackers have adopted the new technique called ‘FileFix’ in Interlock ransomware attacks to drop a remote access trojan (RAT) on targeted…
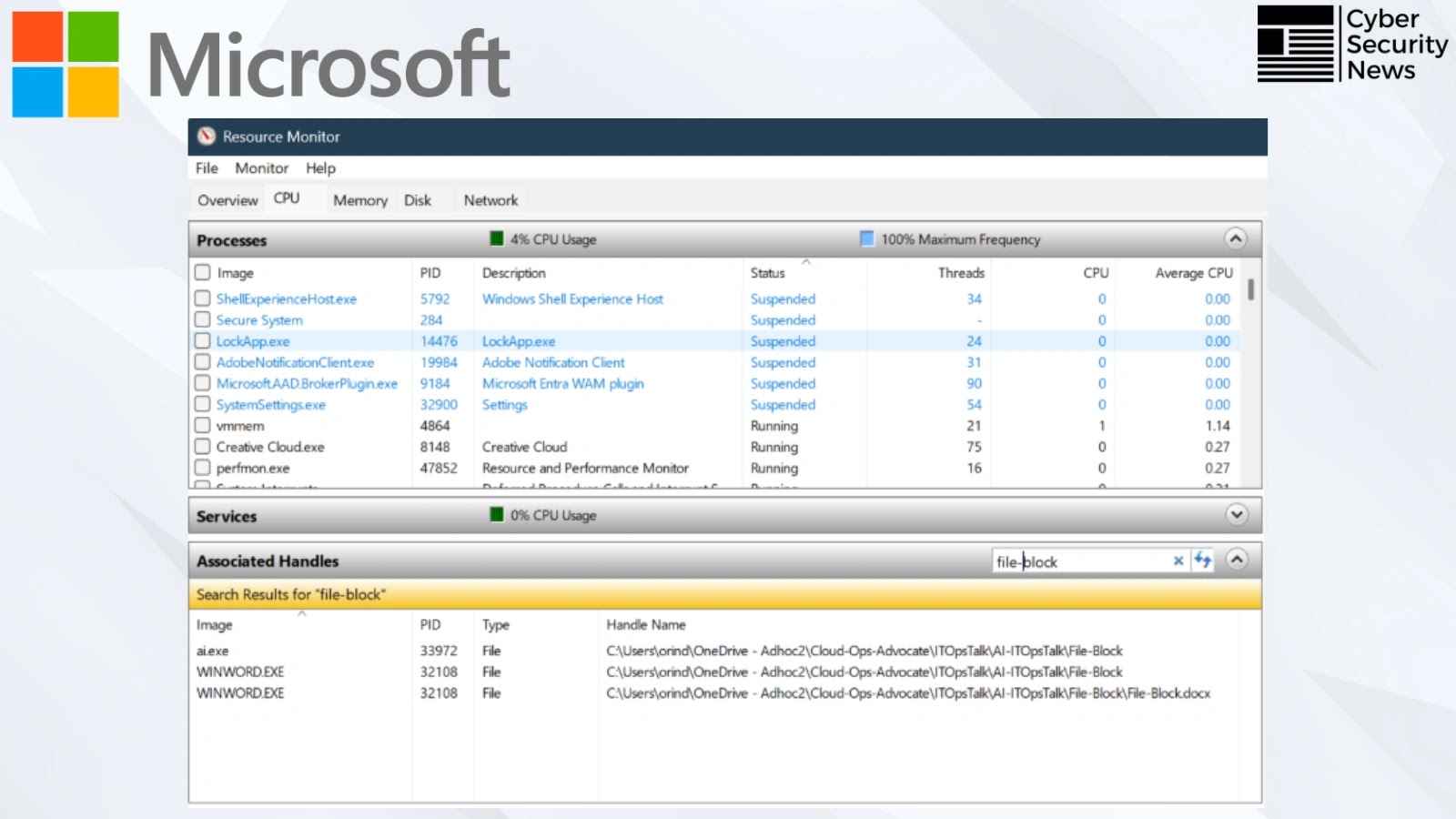
Microsoft has provided comprehensive guidance for resolving the common Windows error “The process cannot access the file because it is…
MITRE has introduced AADAPT (Adversarial Actions in Digital Asset Payment Technologies), a new cybersecurity framework designed to tackle vulnerabilities in…
Interlock ransomware group deploys new PHP-based RAT via FileFix Pierluigi Paganini July 14, 2025 Interlock ransomware group deploys new PHP-based…
Critical security vulnerabilities have been discovered in Gigabyte UEFI firmware that could allow attackers to execute arbitrary code in System…
Luxury fashion house Louis Vuitton is investigating a data breach that exposed customer information tied to its UK operations. The…
A fake extension for the Cursor AI IDE code editor infected devices with remote access tools and infostealers, which, in…
Security researchers have confirmed active exploitation of a critical vulnerability in Wing FTP Server, just one day after technical details…
Online privacy, security, and performance today are more important than ever. For professionals and businesses working online, it’s essential to…