With two proof-of-concept (PoC) exploits made public late last week, CVE-2025-25257 – a critical SQL command injection vulnerability in Fortinet’s…
Global Louis Vuitton data breach impacts UK, South Korea, and Turkey Pierluigi Paganini July 14, 2025 Louis Vuitton data breach…
A sophisticated zero-click attack methodology called RenderShock that exploits passive file preview and indexing behaviors in modern operating systems to…
Critical security vulnerabilities in Gigabyte motherboard firmware have been disclosed that allow attackers to execute arbitrary code in System Management…
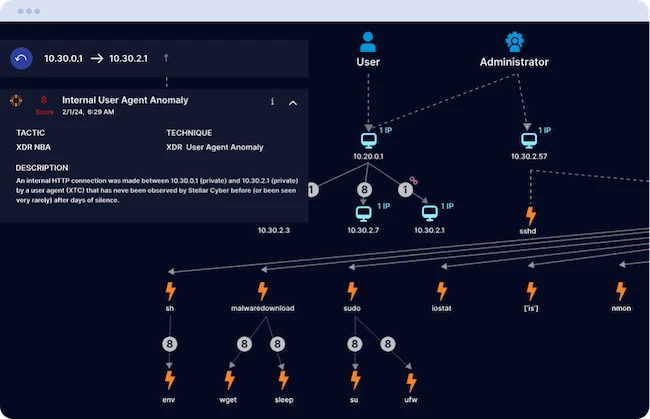
Stellar Cyber released version 6.0.0 of its award-winning open and unified SecOps Platform, introducing new AI-driven capabilities and workflow enhancements…
When news broke that an AI agent named XBOW was leading the HackerOne bug bounty leaderboards, it quickly raised several…
A Pune-based automobile parts manufacturer fell victim to a sophisticated man-in-the-middle (MITM) cyber attack, resulting in a loss of ₹2.35…
Microsoft has provided comprehensive guidance on resolving one of Windows users’ most frustrating issues: the dreaded “The process cannot access…
2024 was an important year for cryptocurrency markets, both in terms of growth, user adoption, investment, and technological progress. However,…
LinkedIn’s Skills on the Rise report says, AI literacy will continue to be the skill that “professionals are prioritizing and…
Embedded SIMs (eSIMs), officially known as Kigen eUICC, are transforming connectivity by allowing users to switch operators without physically swapping…
In an era characterized by escalating cybersecurity threats, rapidly evolving technological landscapes, and heightened regulatory demands, organizations face significant pressure…