July 10, 2025 – Deepfake attacks aren’t just for recruitment and banking fraud; they’ve now reached the highest levels of…
In this Help Net Security interview, Gail Hodges, Executive Director at the OpenID Foundation, discusses how the Foundation ensures global…
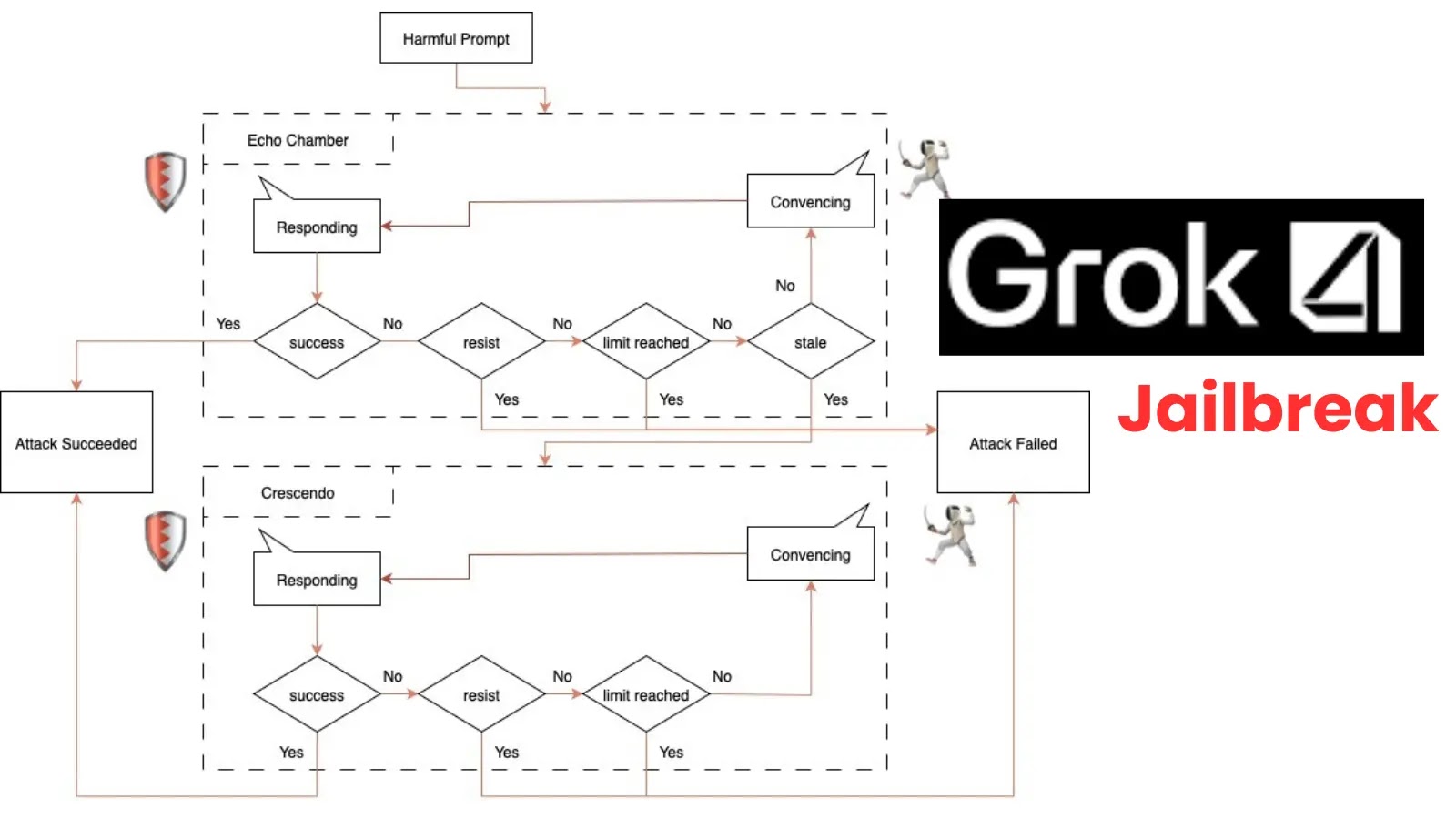
Grok-4 has been jailbroken using a new strategy that combines two different jailbreak methods to bypass artificial intelligence security measures….
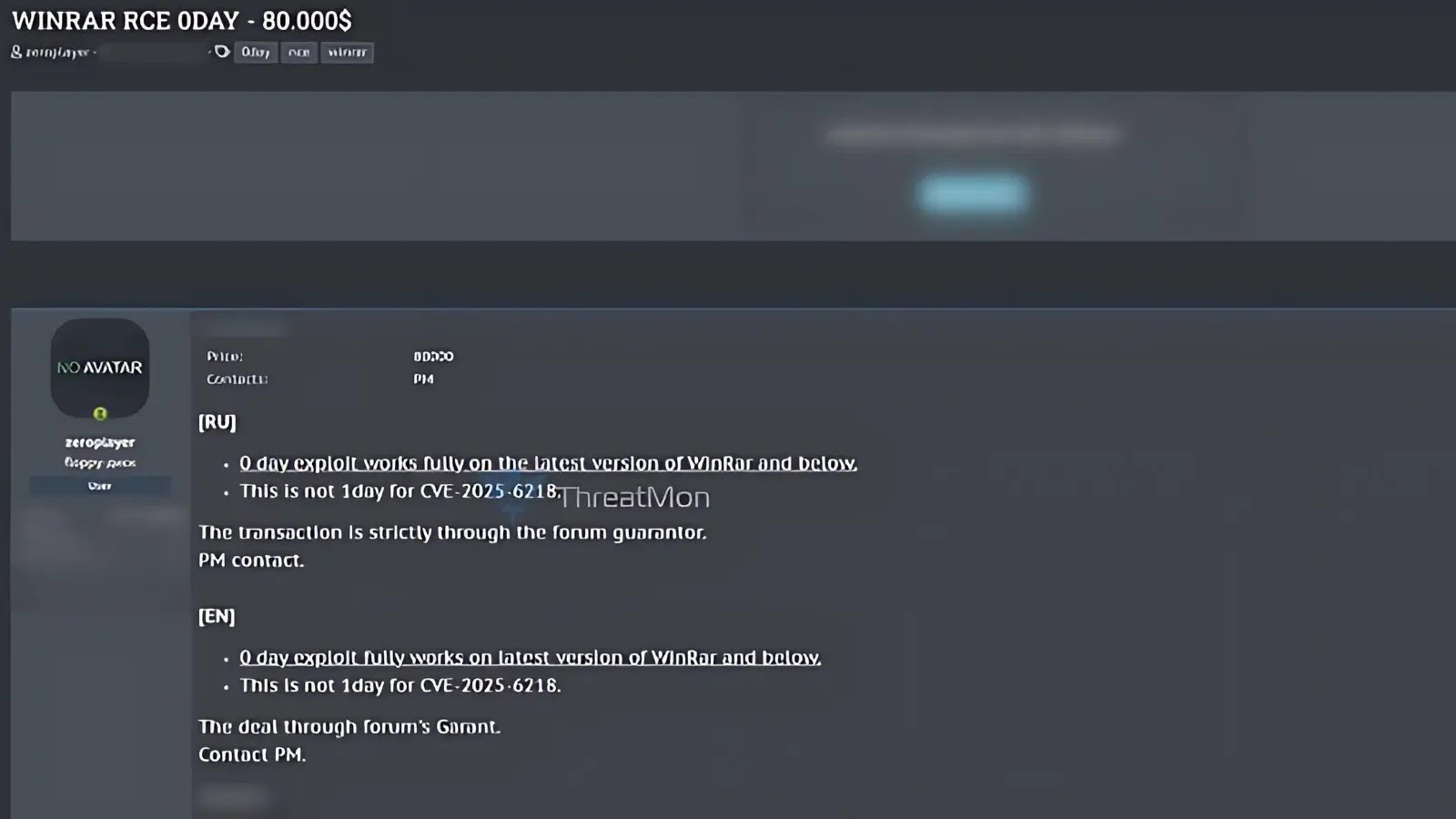
A sophisticated zero-day exploit targeting WinRAR, one of the world’s most popular file compression utilities, has surfaced on a dark…
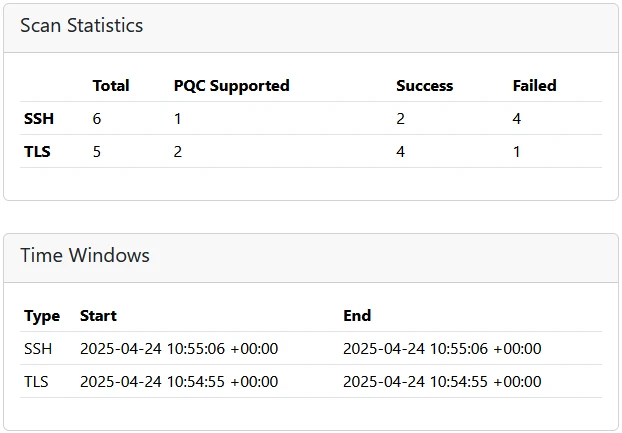
pqcscan is an open-source tool that lets users scan SSH and TLS servers to see which Post-Quantum Cryptography (PQC) algorithms…
Jul 14, 2025Ravie LakshmananMobile Security / Vulnerability Cybersecurity researchers have discovered a new hacking technique that exploits weaknesses in the…
Security researchers have successfully demonstrated a sophisticated jailbreak attack against Grok-4, X’s advanced AI language model, by combining two powerful…
60% of organizations rate their Microsoft 365 security as “established” or “advanced”, according to CoreView. Yet, 60% of those same…
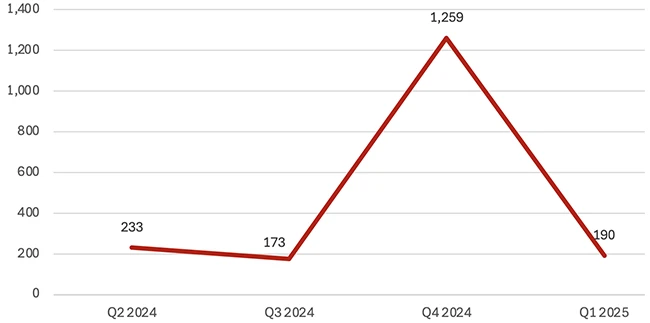
WatchGuard has released its latest Internet Security Report, covering malware, network, and endpoint threats spotted by its Threat Lab in…
A new report from Zendesk outlines a growing problem for companies rolling out AI tools: many aren’t ready to manage…
Companies must use advanced tools to detect and stamp out misinformation and deepfake content to help counter growing risks of…
NSW Police Force is recruiting a delivery director to lead a major transformation of its network infrastructure following a $50-million…