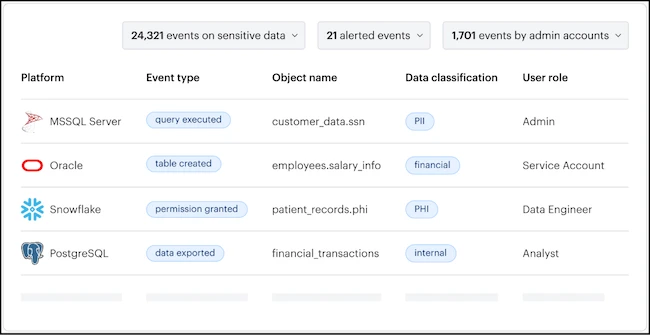
Varonis released Next-Gen Database Activity Monitoring (DAM), a new approach to database security that deploys quickly and overcomes the challenges…
Seychelles Commercial Bank Reported Cybersecurity Incident Pierluigi Paganini July 29, 2025 Seychelles Commercial Bank on Friday said it had recently…
CISA has issued an urgent warning regarding two critical injection vulnerabilities in Cisco’s Identity Services Engine (ISE) that threat actors…
Cybersecurity experts have pointed to an increase in sophisticated threat actor activity following the July 27 2025 Belgian Grand Prix…
Booz Allen Hamilton announced Vellox Reverser, an AI-enabled cloud product that protects organizations from malware as cyberattacks grow increasingly insidious….
U.S. Senator Maggie Hassan has raised concerns over the alleged use of SpaceX’s Starlink satellite internet service by transnational criminal networks…
Cybersecurity researchers have uncovered a sophisticated web shell attack targeting Microsoft Internet Information Services (IIS) servers, allowing threat actors to…
The Cybersecurity and Infrastructure Security Agency (CISA) has added a critical PaperCut vulnerability to its Known Exploited Vulnerabilities (KEV) catalog,…
Cyber Incident Responder Accenture | Ireland | Hybrid – View job details As a Cyber Incident Responder, you will identify…
A critical macOS vulnerability enables attackers to bypass Transparency, Consent, and Control (TCC) protections and steal sensitive user data, including…
GitHub experienced a significant global outage on July 28-29, 2025, disrupting core services used by millions of developers worldwide. The…
We have reached a stage where ransomware isn’t simply a cybercrime issue: it is now clearly a business disruptor, a…