While IT departments race to implement AI governance frameworks, many employees have already opened a backdoor for AI, according to…
Palo Alto Networks has disclosed a significant security vulnerability in its Autonomous Digital Experience Manager software that could allow attackers…
Here’s a look at the most interesting products from the past week, featuring releases from Barracuda Networks, Cynomi, Lepide, Tosibox,…
Investcorp to provide backing for Sababa Fund supported by Hayfin and Coller Sababa aims for expansion in the Middle East…
The initial public draft (IPD) of NIST Special Publication (SP) 800-234, High-Performance Computing (HPC) Security Overlay, is available for public comment…
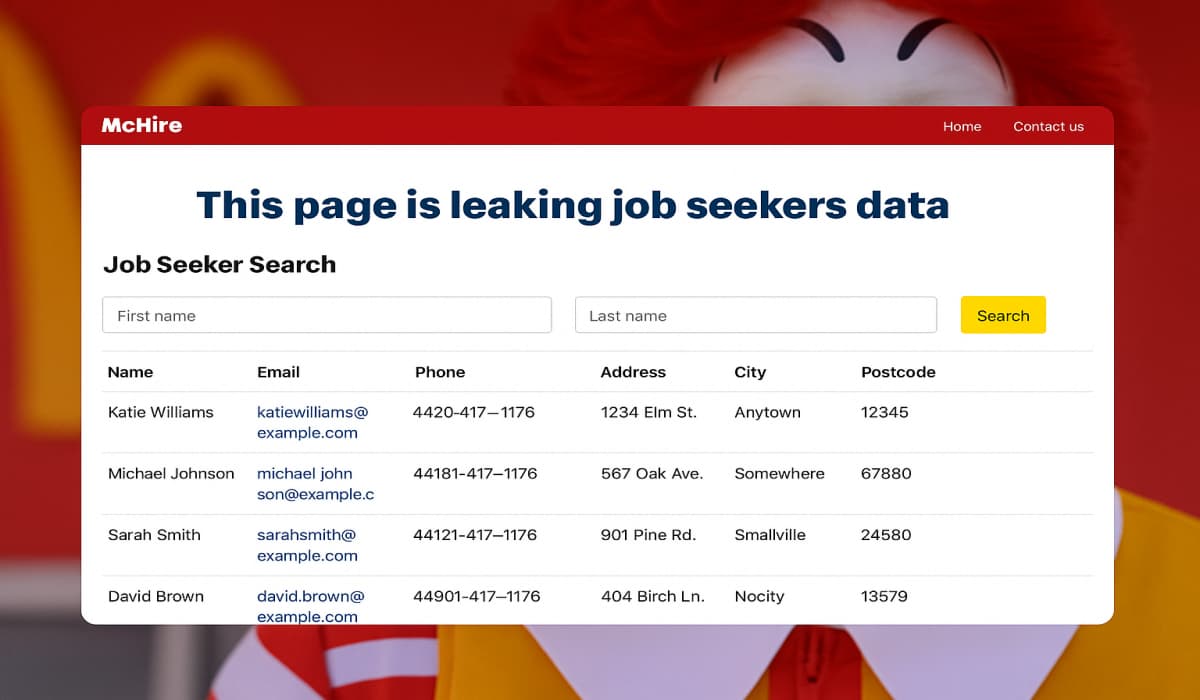
Major security flaw in McDonald’s AI hiring tool McHire exposed 64M job applications. Discover how an IDOR vulnerability and weak…
Major security flaw in McDonald’s McHire platform exposed 64M job applications. Discover how an IDOR vulnerability and weak default credentials…
CYFIRMA has discovered a sophisticated cyberattack campaign in which threat actors are using GitHub to host and disseminate malware masquerading…
A sophisticated new variant of the macOS.ZuRu malware has emerged, targeting macOS users through a weaponized version of the popular…
DHS’s risk-based approach reflects a broader shift in US law enforcement shaped by post-9/11 security priorities—one that elevates perceived intent…
Schneider Electric, a global leader in industrial technology and sustainability, has issued a critical security notification revealing multiple vulnerabilities in…
Four people under 21 have been arrested as part of a police investigation into cyberattacks that disrupted the operations of…