The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical security advisory warning that multiple vulnerabilities in Emerson ValveLink…
Four individuals suspected of having been involved in the ransomware attacks that hit UK-based retailers earlier this year have been…
Deepfake attacks aren’t just for recruitment and banking fraud; they’ve now reached the highest levels of government. News emerged this…
Jul 10, 2025Ravie LakshmananVulnerability / Hardware Security Semiconductor company AMD is warning of a new set of vulnerabilities affecting a…
The UK’s National Crime Agency (NCA) arrested four people suspected of being involved in cyberattacks on major retailers in the…
The cybersecurity landscape witnessed a dramatic shift in June 2025 as the Qilin ransomware group emerged as the dominant threat…
UK law enforcement authorities have made significant progress in their investigation into cyber attacks targeting some of Britain’s most prominent…
Perhaps the biggest near-term AI opportunity is reducing cybercrime costs, according to think tank Cato Institute. With serious attacks unfolding almost…
McDonald’s has outsourced the initial stages of its hiring process to an AI chatbot which seems to have been built…
Jul 10, 2025Ravie LakshmananEndpoint Security / Vulnerability Cybersecurity researchers have discovered new artifacts associated with an Apple macOS malware called…
In this podcast, we talk to Rainer Kaese, senior manager for business development for hard disk drives (HDDs) for Toshiba…
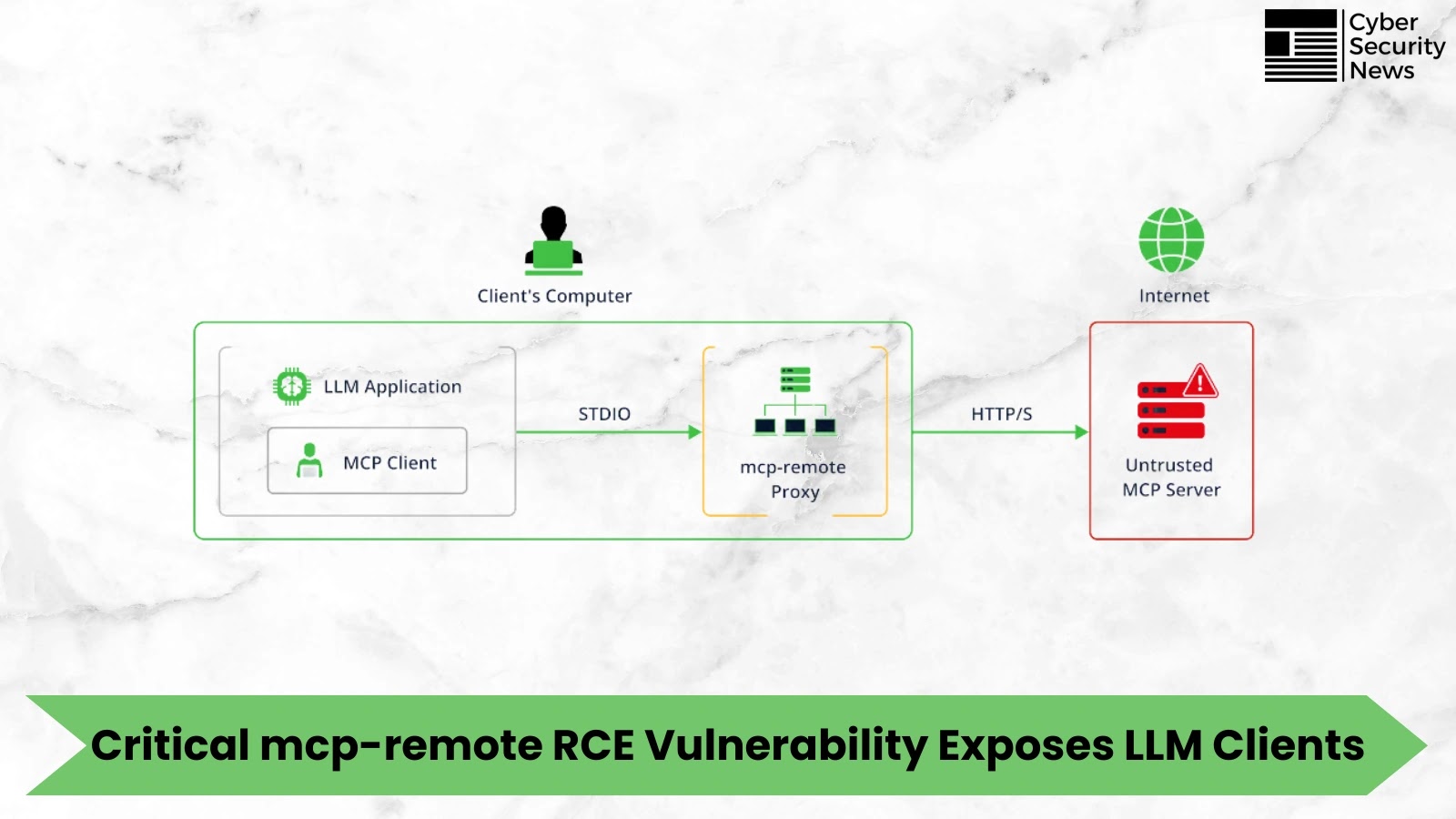
A critical vulnerability CVE-2025-6514 with a CVSS score of 9.6 affecting the mcp-remote project allows attackers to achieve arbitrary operating…