When it comes to investments in artificial intelligence (AI), the numbers are staggering. “Stargate”, a US initiative to build the…
In a significant disruption for millions of users worldwide, Microsoft Outlook has been experiencing a major outage since Wednesday, July…
The Qilin group emerged as the leading player in the ransomware ecosystem, which saw a notable rise in activity during…
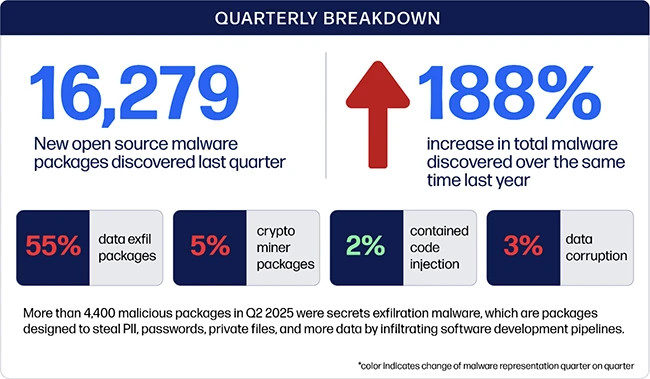
Sonatype has published its Q2 2025 Open Source Malware Index, identifying 16,279 malicious open source packages across major ecosystems such…
Within the bug bounty industry, duplicate submissions refer to when two or more researchers report the same issue or vulnerability….
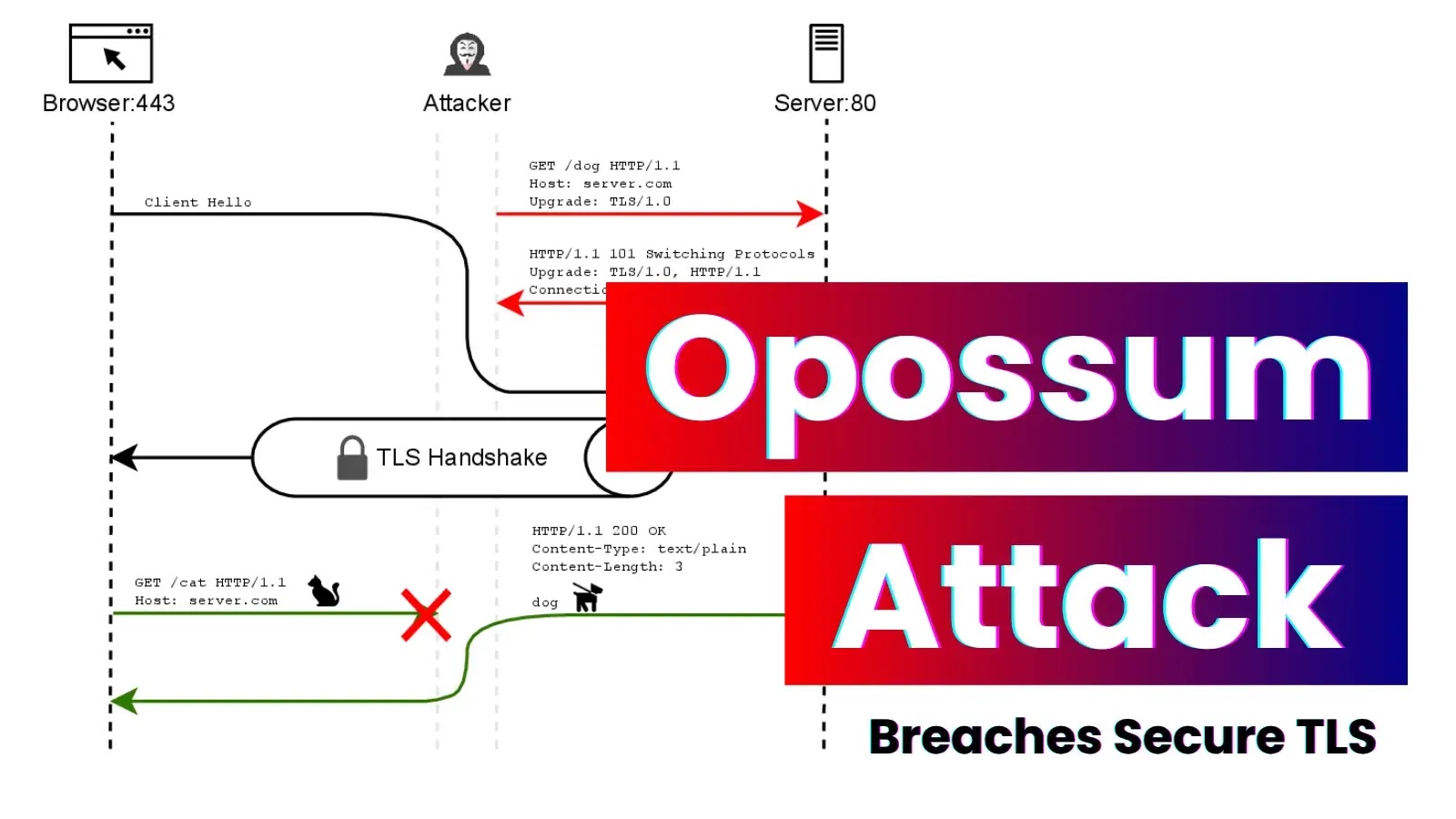
A newly discovered man-in-the-middle exploit dubbed “Opossum” has demonstrated the unsettling ability to compromise secure communications over Transport Layer Security…
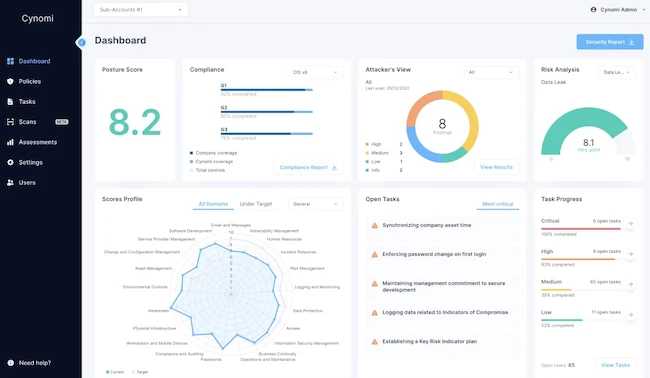
Cynomi has launched new business impact analysis (BIA) and business continuity planning (BCP) features. Designed to help cybersecurity professionals identify…
A high-severity security flaw has been disclosed in ServiceNow’s platform that, if successfully exploited, could result in data exposure and…
GreyNoise has discovered an undiscovered version of a scraper botnet with more than 3,600 distinct IP addresses worldwide, which is…
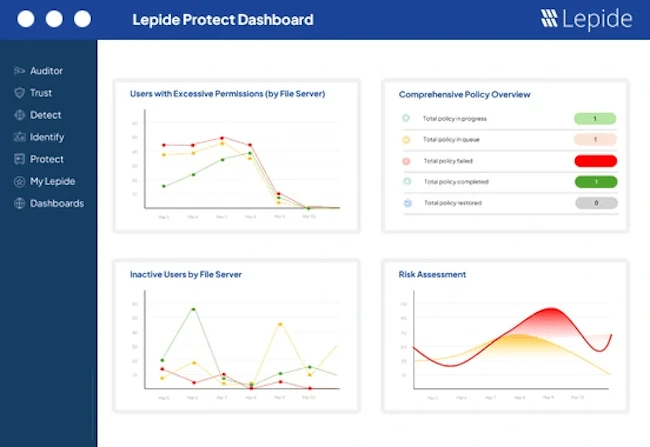
In a move set to redefine the way organizations manage data access and implement zero trust, Lepide launched Lepide Protect, an…
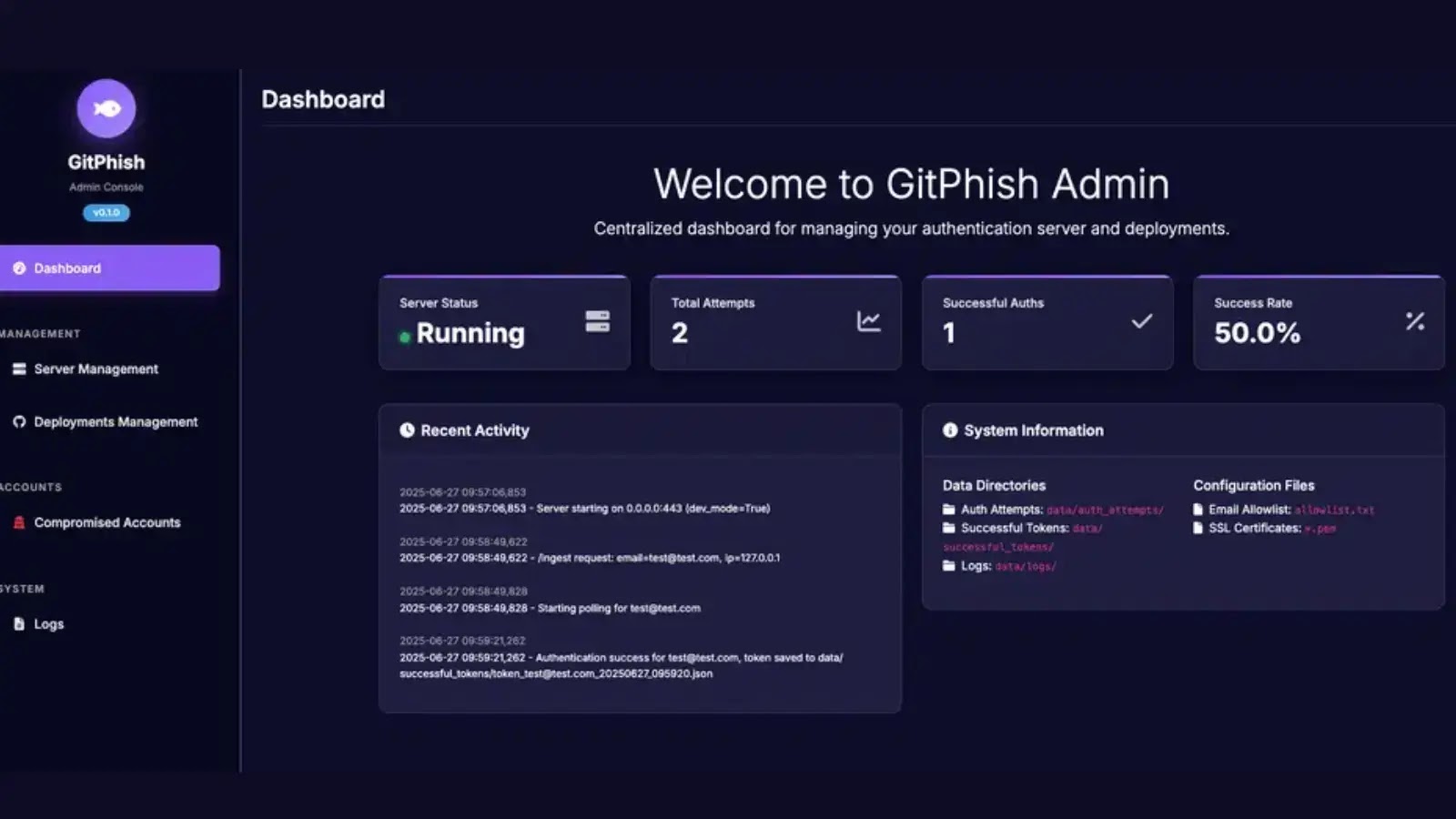
Security researchers revealed the dangers of GitHub Device Code Phishing—a technique that leverages the OAuth 2.0 Device Authorization Grant flow….
In this Help Net Security interview, David Warburton, Director at F5 Labs, discusses how the EU’s Post-Quantum Cryptography (PQC) roadmap…