Victorian electricity distributor Powercor is incorporating multiple AI agents into processes to improve access to information and the work of…
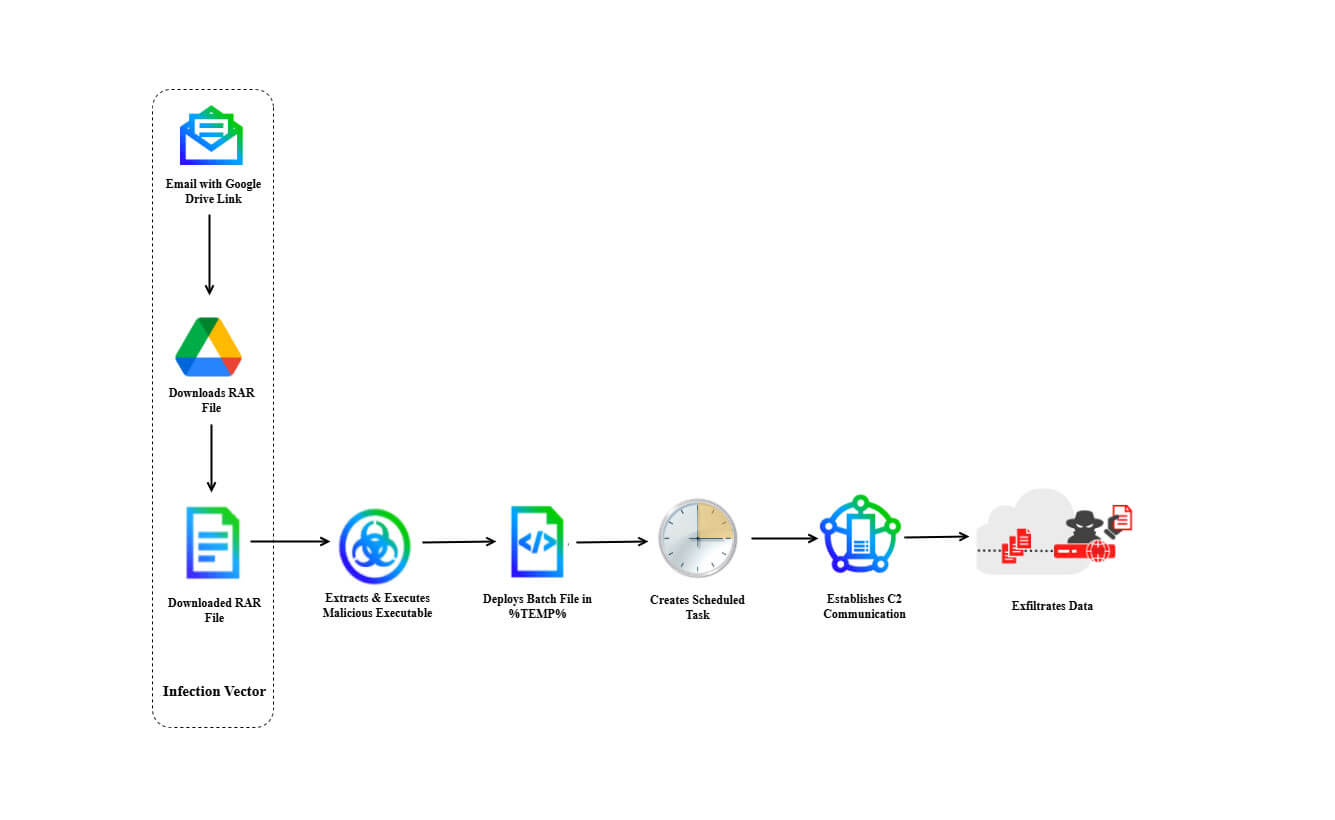
DoNot APT is expanding scope targeting European foreign ministries Pierluigi Paganini July 10, 2025 DoNot APT, likely an India-linked cyberespionage…
A new report is exposing the scale and maturity of deepfake-enabled cybercrime. As generative AI tools become more powerful, affordable,…
Microsoft saved more than US$500 million ($765 million) in its call centres alone last year by using artificial intelligence, Bloomberg…
Microsoft is rolling out a new backup system in September for its Authenticator app on iOS, removing the requirement to…
Nvidia-backed Perplexity AI has launched Comet, a new web browser with AI-powered search capabilities, as the startup looks to challenge…
Telstra plans to lay off 550 employees as part of an ongoing overhaul of its enterprise business and structural changes…
Microsoft has confirmed a widespread issue in Windows Server Update Services (WSUS) that prevents organizations from syncing with Microsoft Update…
Microsoft is setting up a co-investment program with Defence that will see the department receive financial support for unspecified “cloud…
Australian airline Qantas has confirmed that 5.7 million people have been impacted by a recent data breach, in which threat…
If you want a job at McDonald’s today, there’s a good chance you’ll have to talk to Olivia. Olivia is…
Google is sharing more information on how Chrome operates when Android mobile users enable Advanced Protection, highlighting strong security improvements….