Sports fans and cybercriminals both look forward to major sporting events, but for very different reasons. Fake ticket sites, stolen…
Jul 08, 2025Ravie LakshmananCyber Attacks / Vulnerability The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Monday added four security…
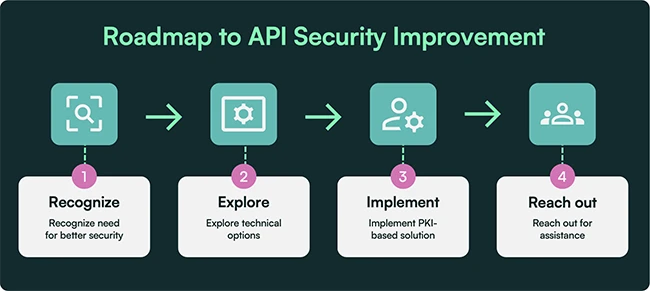
Most organizations are exposing sensitive data through APIs without security controls in place, and they may not even realize it,…
Analyst III-Threat Intel Verizon Data Services | India | Hybrid – View job details As an Analyst III-Threat Intel, you…
South Korean authorities ordered SK Telecom to strengthen data security and imposed a fine after the country’s biggest mobile carrier…
Western Australian organisations are changing roles within existing teams to require skills that support use-case driven approaches to AI and…
A Chinese national was arrested in Milan, Italy, last week for allegedly being linked to the state-sponsored Silk Typhoon hacking…
Researchers have released proof-of-concept (PoC) exploits for a critical Citrix NetScaler vulnerability, tracked as CVE-2025-5777 and dubbed CitrixBleed2, warning that the…
NSW government employers have been instructed not to use artificial intelligence to screen or make decisions about candidates applying for…
Online customers around the world are getting ready for huge discounts and unique offers as July 8, the much-anticipated Amazon…
TPG Telecom said that Macquarie-backed Vocus Group has secured the final approval for its $5.25 billion acquisition of TPG’s enterprise,…
The Parrot Security team has released Parrot Security OS 6.4, a robust update featuring community-driven enhancements and contributions. As the…