Huawei’s artificial intelligence research division has rejected claims that a version of its Pangu Pro large language model has copied…
In 2016, my friend Daniel Miessler wrote a book called “The Real Internet of Things.” It’s a quick little read…
Cybercriminals continue to use kernel-level malware as a preferred weapon against Windows systems amid a terrifying increase in cyberthreats. Operating…
The International Criminal Court (ICC) recently announced it was hit by a sophisticated cyberattack. The attack, detected late last week,…
nib Group has built a set of AI-powered workflows to support a complex data migration program following its acquisition of…
Cybercriminals continue to use kernel-level malware as a preferred weapon against Windows systems amid a terrifying increase in cyberthreats. Operating…
Telecom giant AT&T has agreed to a $177 million settlement to resolve two major lawsuits stemming from widespread data breaches…
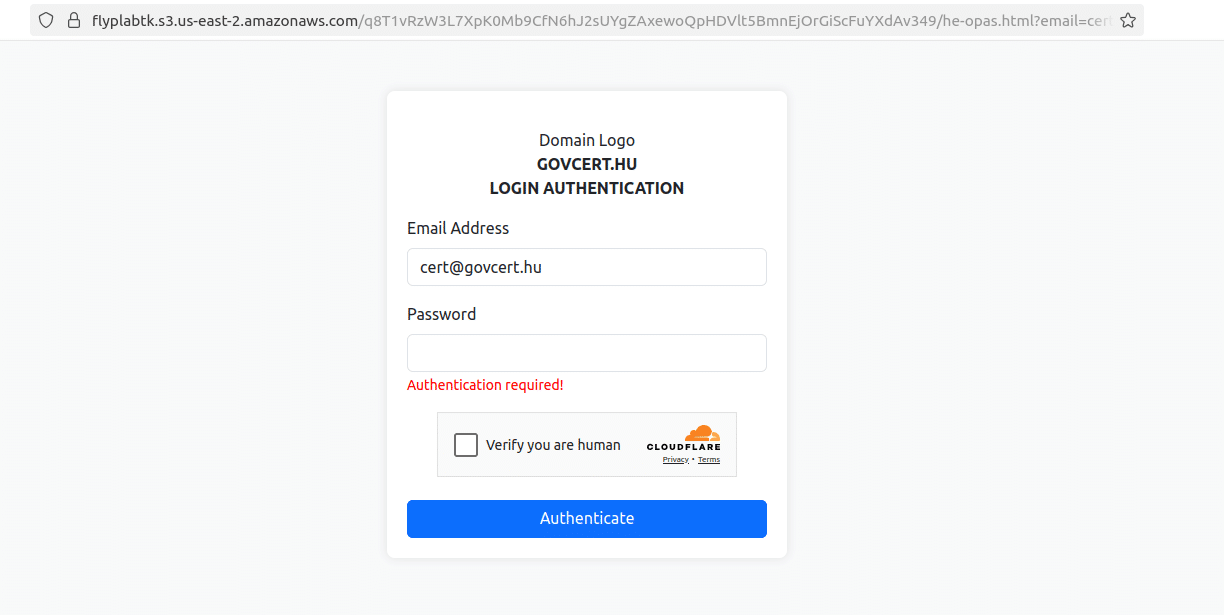
Cyble threat intelligence researchers identified a phishing campaign aimed at Hungarian government targets that further investigation revealed was connected to…
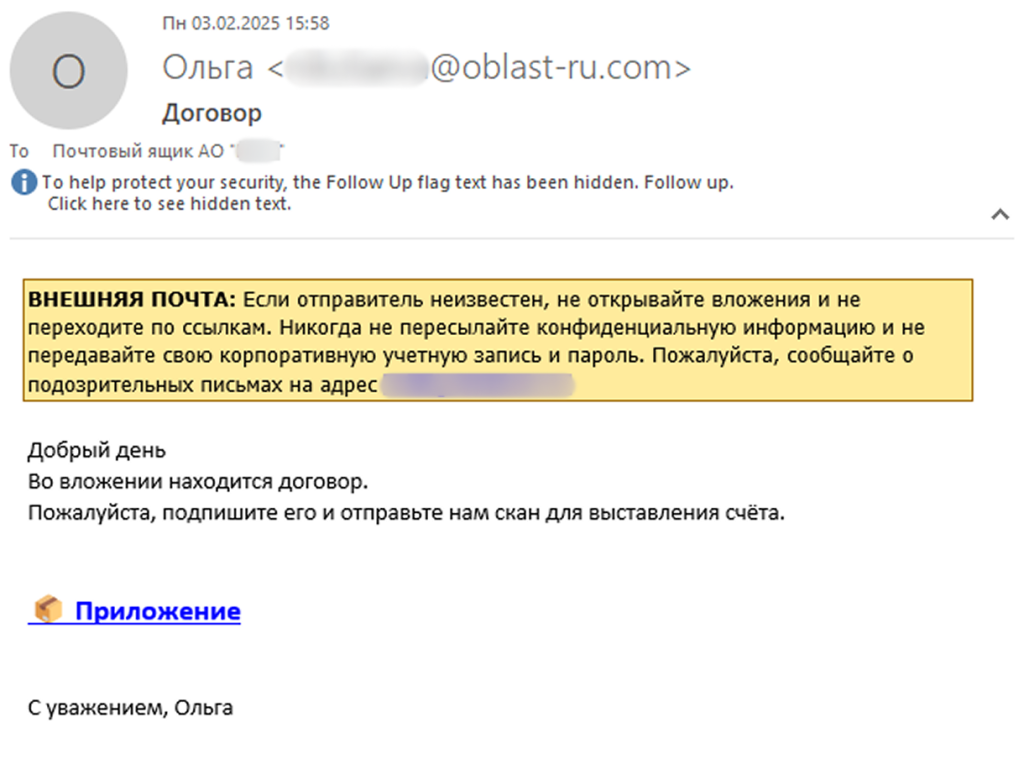
New Batavia spyware targets Russian industrial enterprises Pierluigi Paganini July 07, 2025 Since March 2025, fake contract emails have been…
Hackers stole nearly $140 million from six banks in Brazil by using an employee’s credentials from C&M, a company that offers financial…
Dr.Web Security Space for mobile devices reported that malware activity on Android devices increased significantly in the second quarter of…
The makers of Call of Duty: World War 2 took the PC version of the game offline over the weekend…