TAFE NSW is to spend $87 million on Microsoft cloud and digital services over the next three years under a…
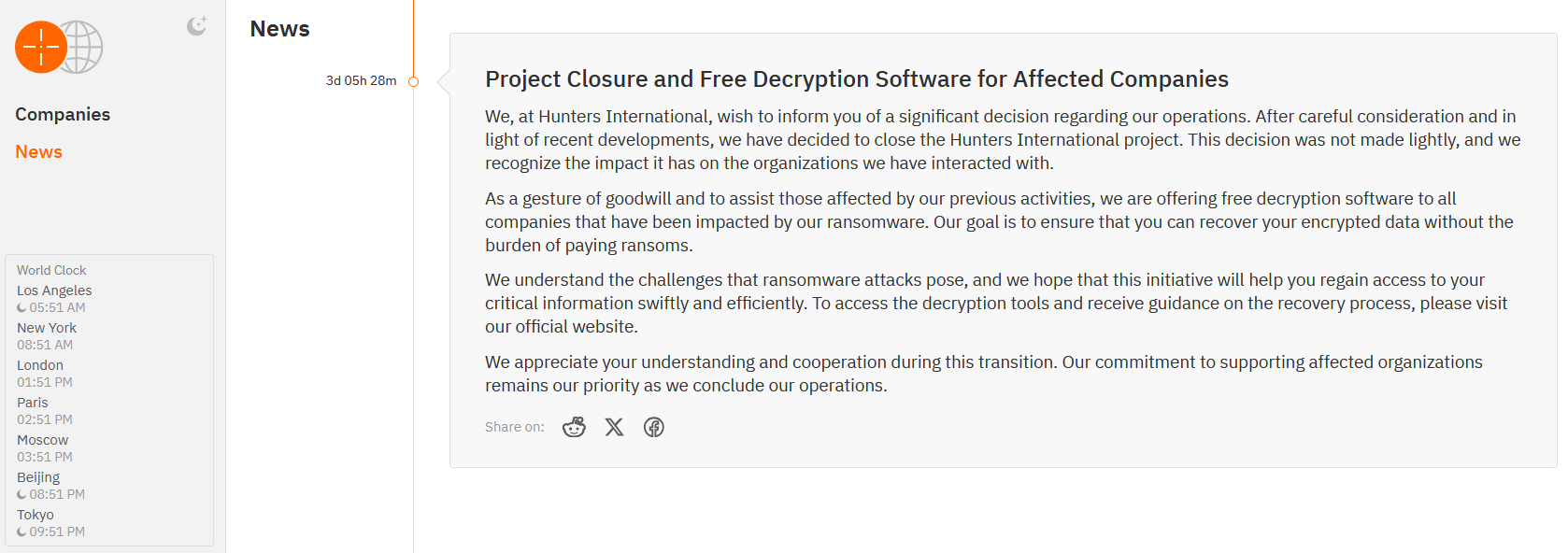
Hunters International ransomware gang shuts down and offers free decryption keys to all victims Pierluigi Paganini July 06, 2025 Hunters…
Security Affairs Malware newsletter includes a collection of the best articles and research on malware in the international landscape 10…
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Sudo local privilege escalation vulnerabilities…
Security Affairs newsletter Round 531 by Pierluigi Paganini – INTERNATIONAL EDITION Pierluigi Paganini July 06, 2025 A new round of…
More powerful XSS scanning, Integration Dalfox v2.12.0 has been released. It’s been about three months since the previous version, 2.11,…
I think, looking back, we might say that the first week of July 2025 was the start of AGI. Like,…
North Korea-linked threat actors spread macOS NimDoor malware via fake Zoom updates Pierluigi Paganini July 05, 2025 North Korea-linked hackers…
An ongoing outage at IT giant Ingram Micro is caused by a SafePay ransomware attack that led to the shutdown…
A sophisticated phishing campaign targeting UK citizens has emerged, masquerading as official communications from the Department for Work and Pensions…
A significant security vulnerability has been discovered in Lenovo’s preloaded Windows operating systems, where a writable file in the Windows…
Instagram has adopted an unprecedented approach to web security by implementing daily rotation of TLS certificates that maintain validity periods…