Some schemes might sound unbelievable, but they’re easier to fall for than you think. Here’s how to avoid getting played…
Cybersecurity researchers have discovered a sophisticated attack technique that exploits Microsoft Azure Arc deployments to gain persistent access to enterprise…
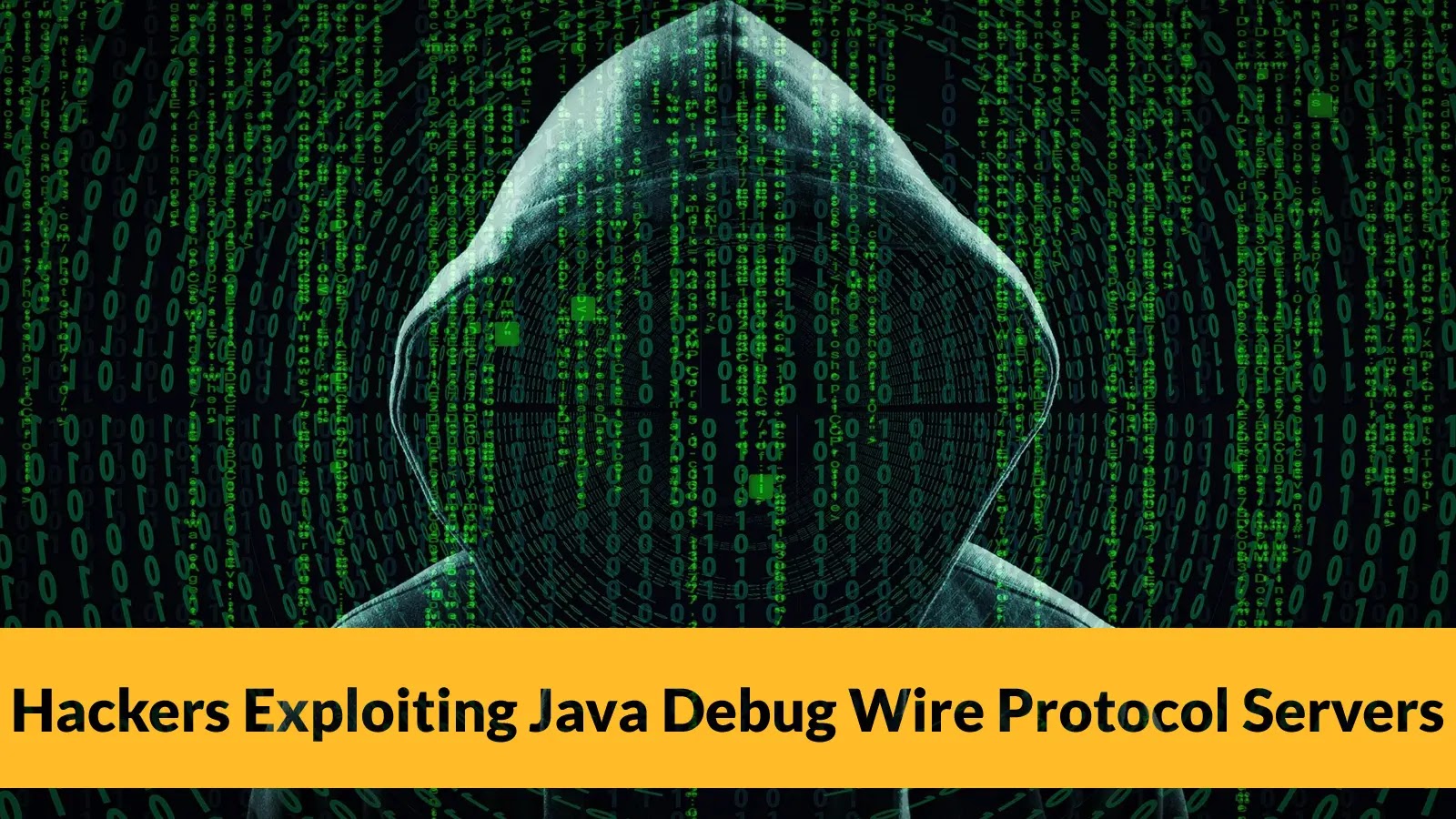
Threat actors are weaponizing exposed Java Debug Wire Protocol (JDWP) interfaces to obtain code execution capabilities and deploy cryptocurrency miners…
Cracking the code of a successful cybersecurity career starts here. Hear from ESET’s Robert Lipovsky as he reveals how to…
Jul 05, 2025Ravie LakshmananNational Security / Privacy Taiwan’s National Security Bureau (NSB) has warned that China-developed applications like RedNote (aka…
A new wave of cyberattacks is targeting organizations that inadvertently expose Java Debug Wire Protocol (JDWP) servers to the internet,…
Key Takeaways1. Next.js versions 15.1.0-15.1.8 have a cache poisoning bug causing DoS attacks through blank page delivery.2. Needs affected Next.js…
Google says Veo 3, which is the company’s state-of-the-art video generator, is now shipping to everyone using the Gemini app…
ChatGPT Deep Research, which is an AI research tool to automate research, is getting support for new connectors (integrations), including…
Critical Sudo bugs expose major Linux distros to local Root exploits Pierluigi Paganini July 04, 2025 Critical Sudo flaws let…
A newly disclosed pair of critical vulnerabilities in Sudo — the powerful Unix/Linux command-line tool that allows users to run…
One might not typically expect a childhood on a Texas farm to lead to a career that involve investigating cybercriminals…