ChatGPT Deep Research, which is an AI research tool to automate research, is getting support for new connectors (integrations), including…
Critical Sudo bugs expose major Linux distros to local Root exploits Pierluigi Paganini July 04, 2025 Critical Sudo flaws let…
A newly disclosed pair of critical vulnerabilities in Sudo — the powerful Unix/Linux command-line tool that allows users to run…
One might not typically expect a childhood on a Texas farm to lead to a career that involve investigating cybercriminals…
Security researchers have discovered novel ways to identify and take advantage of Microsoft Azure Arc in business settings, which is…
A hacker is threatening to leak 106GB of data allegedly stolen from Spanish telecommunications company Telefónica in a breach that…
Cybercriminals are increasingly weaponizing legitimate software installer frameworks like Inno Setup to distribute malware, turning user-friendly tools into covert vehicles…
IT giant Ingram Micro is experiencing a global outage that is impacting its websites and internal systems, with customers concerned…
A critical vulnerability, tracked as CVE-2025-49826, has been discovered and addressed in the popular React-based web framework, Next.js. The flaw, present…
Every security practitioner knows that employees are the weakest link in an organization, butthis is no longer the case. SquareX’s…
A newly disclosed vulnerability, CVE-2025-46647, has been identified in the openid-connect plugin of Apache APISIX, a widely used open-source API gateway….
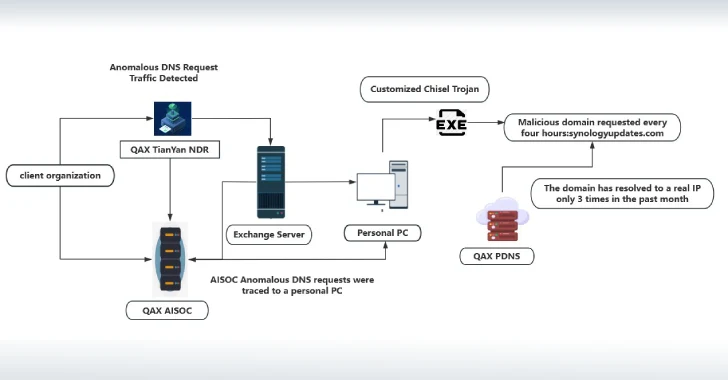
Jul 04, 2025Ravie LakshmananZero-Day / Cyber Espionage Cybersecurity researchers have shed light on a previously undocumented threat actor called NightEagle…