Security researchers have disclosed two significant vulnerabilities in PHP, the popular server-side scripting language, that could allow attackers to launch…
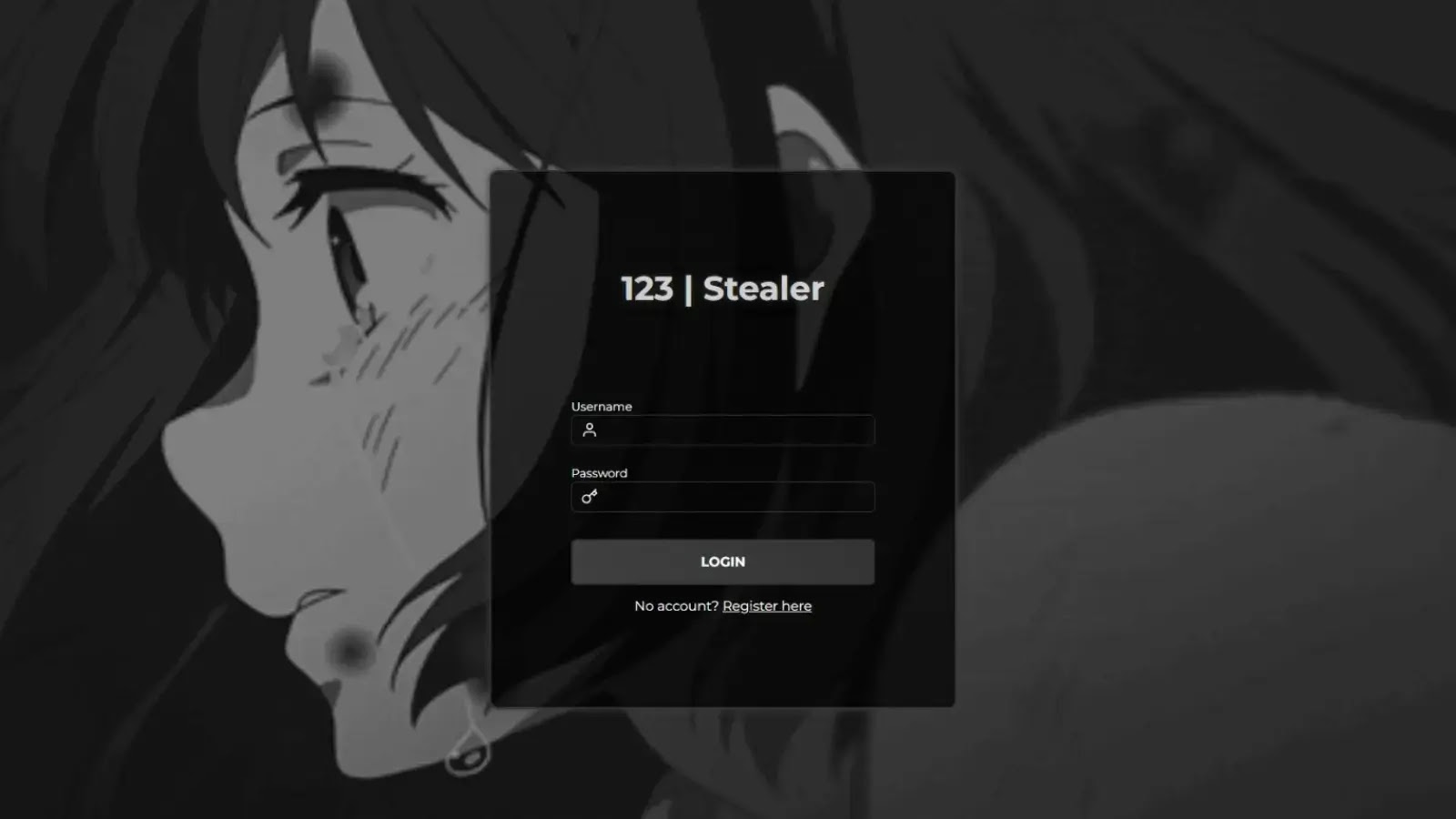
A new credential-stealing malware, dubbed “123 | Stealer,” has surfaced on underground cybercrime forums, with the threat actor known as #koneko offering…
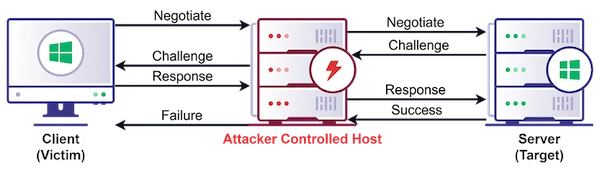
NTLM relay attacks are the easiest way for an attacker to compromise domain-joined hosts. While many security practitioners think NTLM…
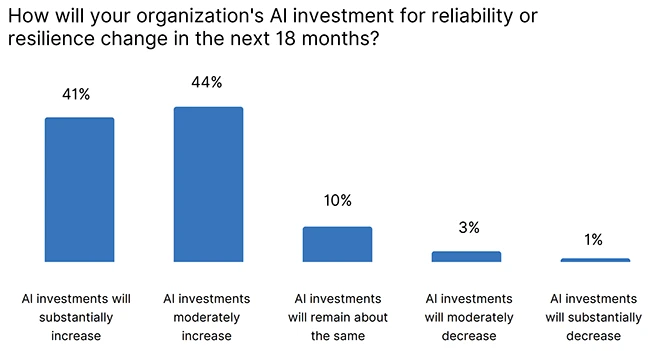
To ensure resilience across the internet stack, organizations need to protect and manage four key areas: reachability, availability, reliability, and…
As major productivity solution providers continue to adjust their plan offerings, many organisations are grappling with sudden shrinking plan options,…
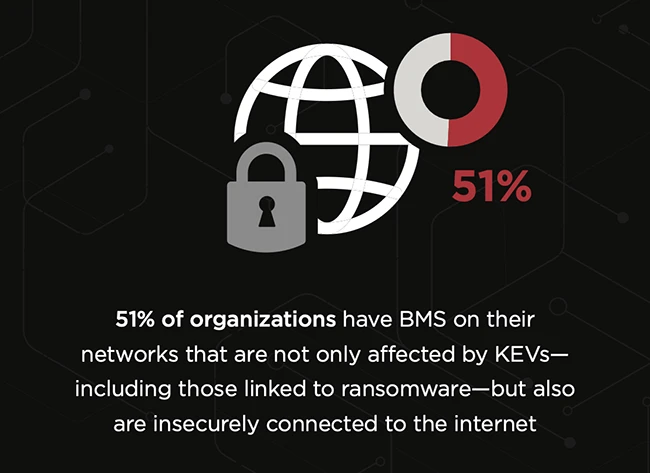
75% of organizations have building management systems (BMS) affected by known exploited vulnerabilities (KEVs), according to Claroty. Threats to building…
A sophisticated new botnet family has emerged in the cybersecurity landscape, demonstrating unprecedented innovation in malware design and attack methodologies….
Here’s a look at the most interesting products from the past week, featuring releases from DigitalOcean, Scamnetic, StealthCores, and Tracer…
Microsoft Azure’s role-based access control system has been found to contain critical security vulnerabilities that could expose enterprise networks to…
Table of Contents The feeling If you’re like me, you’ve had this strange, uneasy feeling about the job market1 for…
I think we’re all in microcults now. Fractal microcults. Infinitely small ones. Cults of one. Not everyone, of course, but…
A few new code references in the ChatGPT web app and Android point to an Operator-like tool in GPT’s chain…