Defence is set to spend at least $100 million annually on Microsoft Azure services until 2030. Under a new five-year…
Alphabet’s Google has proposed fresh changes to its search results in an attempt to fend off growing criticism from rivals,…
The head of the US government’s Intelligence Advanced Research Projects Activity (IARPA) is leaving the unit this month to take…
Email is still the backbone of how businesses communicate, with more than 300 billion messages sent every day. But this…
Microsoft has confirmed it will lay off nearly 4 percent of its workforce as the tech giant looks to rein…
China-linked group Houken hit French organizations using zero-days Pierluigi Paganini July 03, 2025 China-linked group Houken hit French govt, telecom,…
xAI is preparing the rollout of Grok 4, which replaces Grok 3 as the new state-of-the-art model. Ahead of the rollout,…
Two high-severity vulnerabilities in Anthropic’s Model Context Protocol (MCP) Filesystem Server enable attackers to escape sandbox restrictions and execute arbitrary…
Let’s Encrypt, a leading certificate authority (CA) known for providing free SSL/TLS certificates since 2015, has issued its first-ever certificate…
The Spanish police have dismantled a large-scale investment fraud operation that caused cumulative damages exceeding $11.8 million (€10 million). During…
Critical vulnerabilities in Apache Tomcat and Apache Camel are being actively exploited by cybercriminals worldwide, with security researchers documenting over…
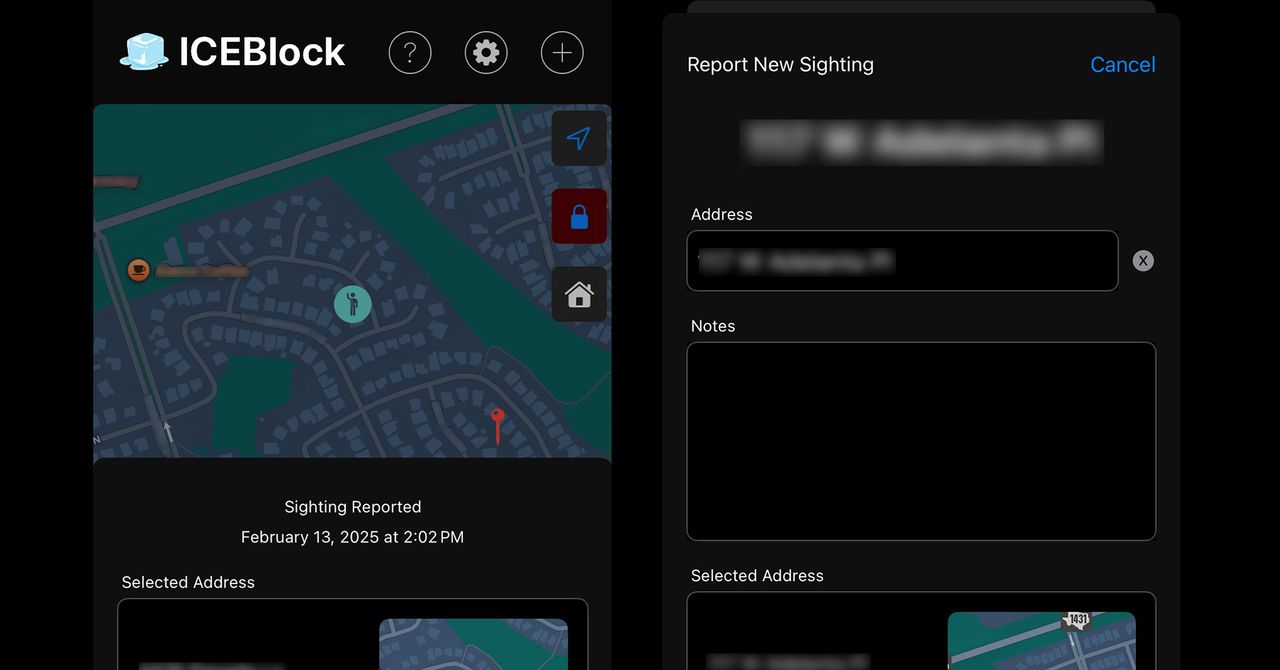
A spokesperson using ICE’s general press email referred WIRED to a statement issued by acting director Todd M. Lyons on…