The .COM top-level domain continues to dominate the cybercriminal landscape as the primary vehicle for hosting credential phishing websites, maintaining…
A sophisticated phishing campaign, initially spotlighted by Mexican journalist Ignacio Gómez Villaseñor, has evolved into a sprawling global threat, as…
Grafana Labs has addressed four Chromium vulnerabilities in critical security updates for the Grafana Image Renderer plugin and Synthetic Monitoring…
Citrix has issued an urgent advisory warning customers of widespread authentication failures following recent updates to NetScaler builds 14.1.47.46 and…
In May 2025, the U.S. government sanctioned a Chinese national for operating a cloud provider linked to the majority of…
NSFOCUS Fuying Lab’s Global Threat Hunting System has discovered a new botnet family called “hpingbot” that has been quickly expanding…
A mobile ad fraud operation dubbed IconAds that consisted of 352 Android apps has been disrupted, according to a new…
Multiple critical infrastructure sectors were hit last year during an attack spree in France via a trio of zero-day vulnerabilities…
Microsoft is investigating an ongoing incident causing intermittent issues for users attempting to access SharePoint Online sites. Part of the…
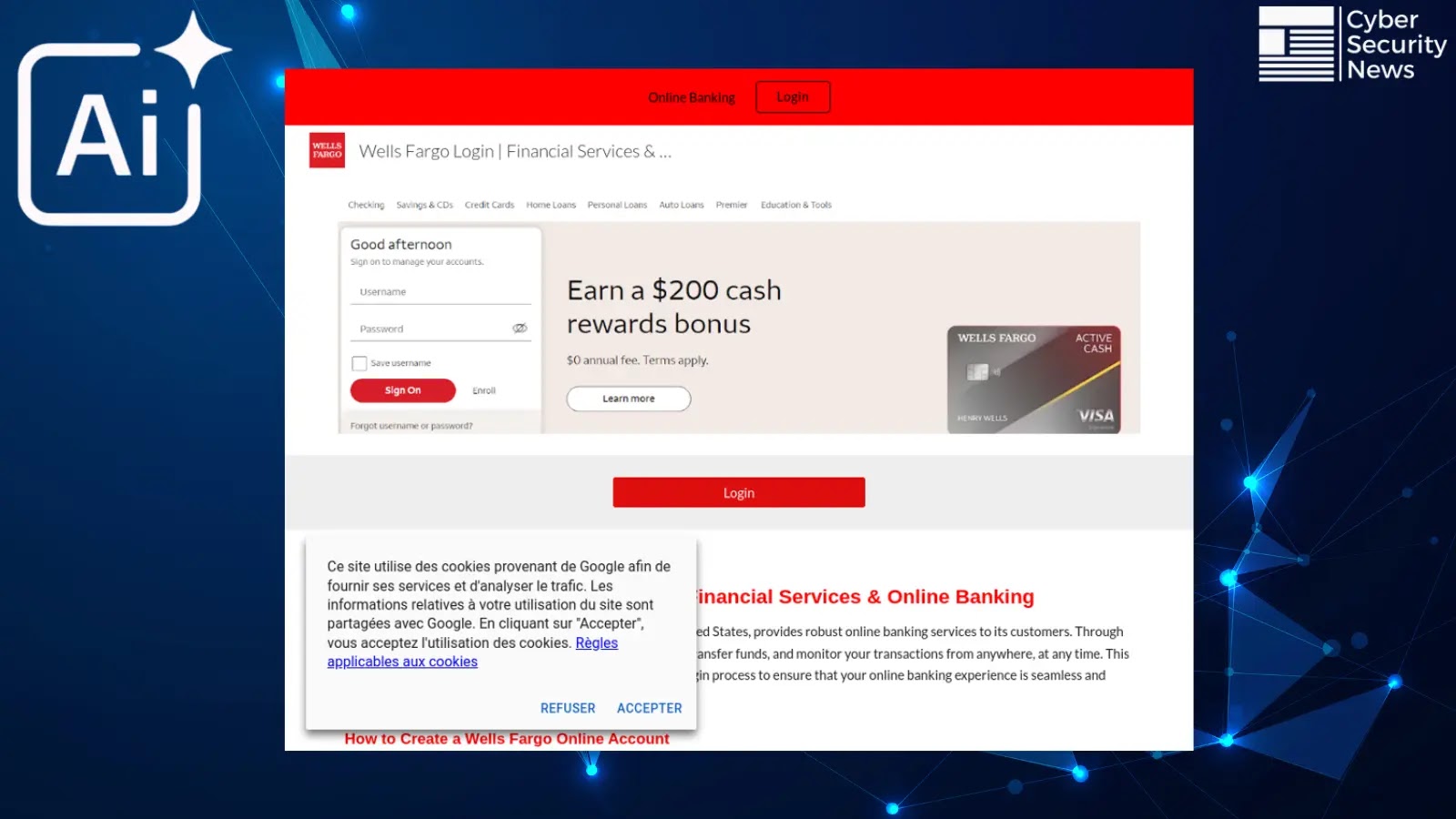
The popular artificial intelligence tools, including GPT models and Perplexity AI, are inadvertently directing users to phishing websites instead of…
Threat actors have dramatically increased their exploitation of the cybersecurity sector, which is a disturbing development. Spain’s country code TLD,…
Age verification is becoming more common across websites and online services. But many current methods require users to share personal…