A newly disclosed critical vulnerability in Wing FTP Server threatens thousands of organizations worldwide, enabling attackers to achieve full server takeover through unauthenticated remote…
A few months ago, Microsoft introduced Copilot Tuning, offering its customers a way to use low-code tooling in Microsoft Copilot…
A hacktivist collective known as Keymous+ has emerged as a significant threat actor in the global cybersecurity landscape, claiming responsibility…
Rodríguez and his collective received digital security training from Amate, another LGBTIQ+ organization that advocates nationally. Since May, Amate has…
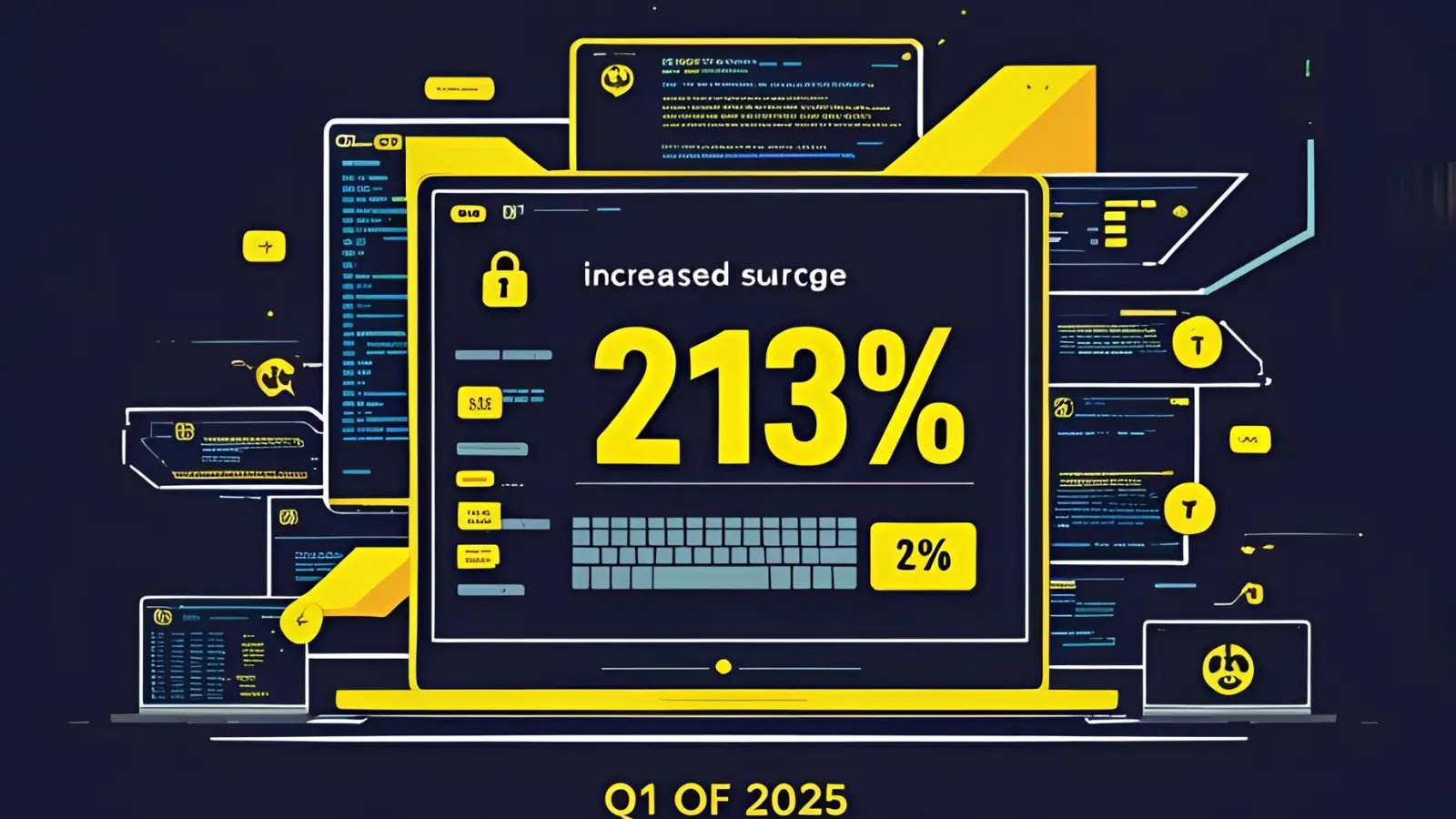
Ransomware assaults on businesses around the world have increased by 213% in the first quarter of 2025, with 2,314 victims…
A severe vulnerability in Cisco Unified Communications Manager (Unified CM) systems could allow remote attackers to gain root-level access to…
A shadowy group known as Keymous+ has emerged as a formidable force in the cyber landscape, claiming responsibility for over…
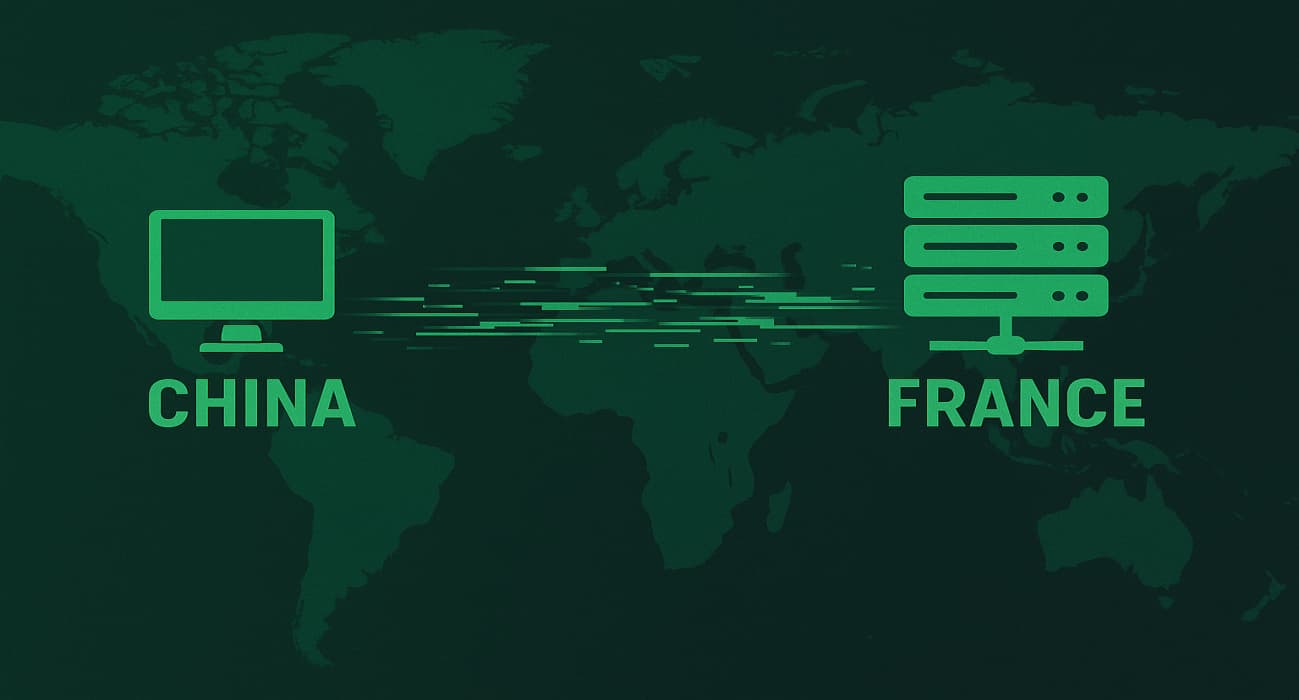
In a report published by ANSSI on July 1, 2025, the French cybersecurity agency revealed a highly skilled cybercrime group,…
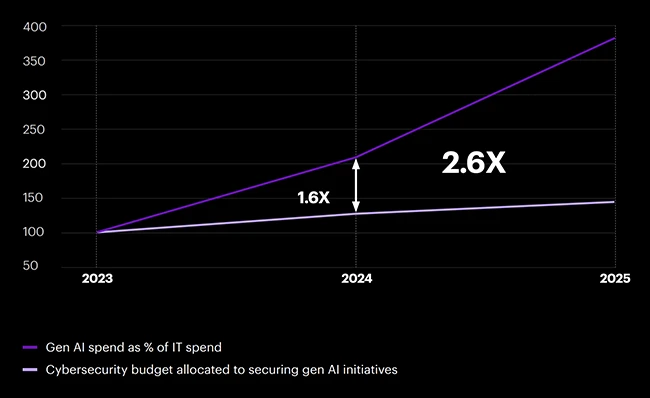
As AI reshapes business, 90% of organizations are not adequately prepared to secure their AI-driven future, according to a new…
Kelly Benefits data breach has impacted 550,000 people, and the situation continues to worsen as the investigation progresses Pierluigi Paganini…
The US government has taken another significant step towards strengthening cloud security with the release of CISA’s Binding Operational Directive…
A newly disclosed vulnerability in Apache Seata, a popular open-source distributed transaction solution, has raised security concerns for organizations relying…