A critical security vulnerability has been discovered and patched in Tenable’s Nessus vulnerability scanner for Windows, potentially allowing non-administrative users…
The cybersecurity landscape faces a renewed threat as TA829, a sophisticated threat actor group, has emerged with enhanced tactics, techniques,…
Microsoft has confirmed a significant issue affecting its Intune security baseline update process, causing concern among IT administrators worldwide. The…
U.S. CISA adds TeleMessage TM SGNL flaws to its Known Exploited Vulnerabilities catalog Pierluigi Paganini July 02, 2025 U.S. Cybersecurity…
A newly disclosed security advisory from Tenable reveals serious vulnerabilities in the Nessus vulnerability scanner that could enable attackers to…
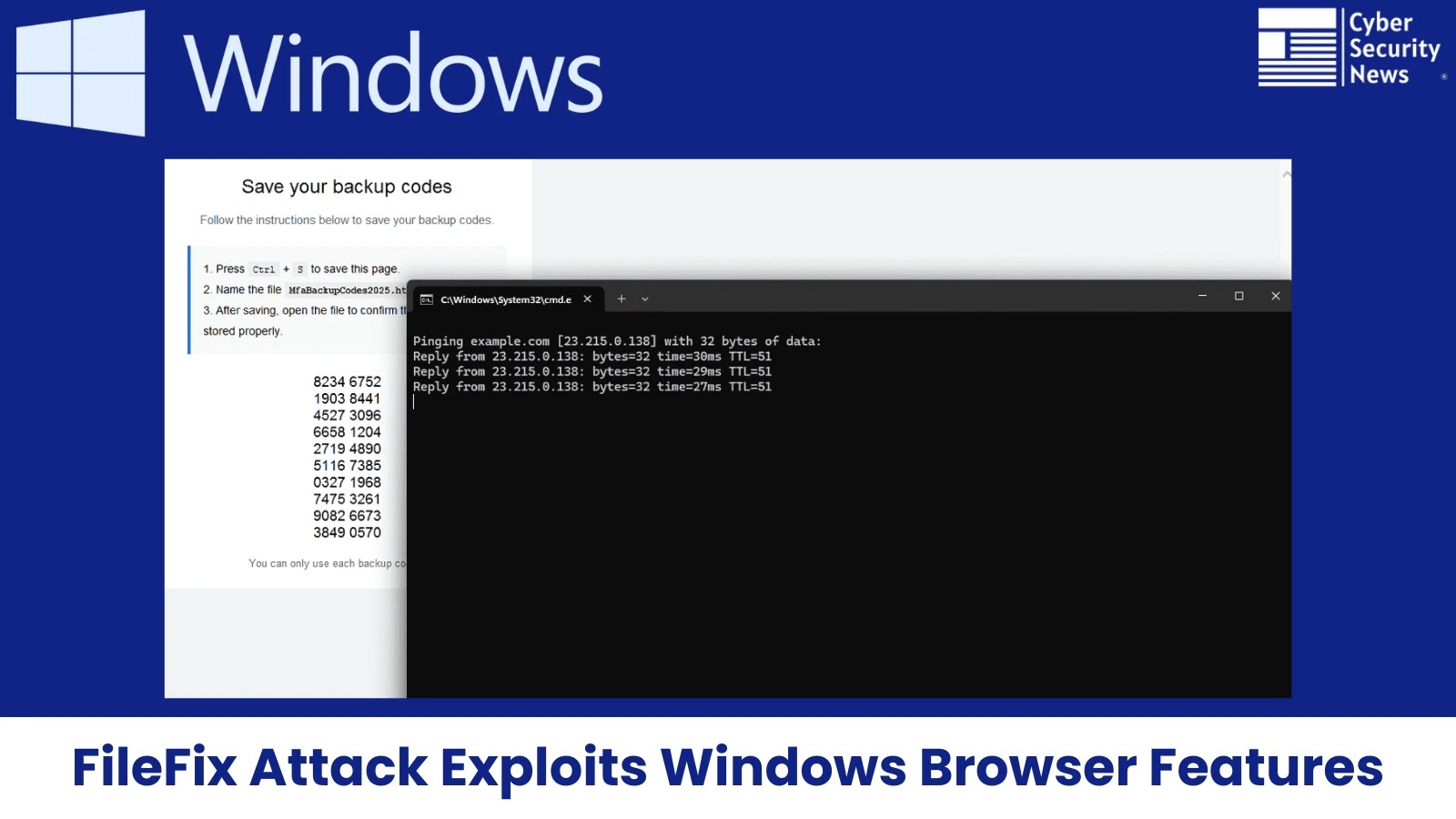
A newly identified attack vector, dubbed the “FileFix Attack,” has surfaced, exploiting a subtle yet critical loophole in how modern…
A sophisticated new variation of cyberattacks emerged in July 2025, exploiting a critical vulnerability in how Chrome and Microsoft Edge…
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) has imposed sweeping sanctions on Aeza Group, a Russia-based…
The Apricorn Aegis Secure Key 3NXC is a 256-bit AES XTS hardware-encrypted flash drive with a USB-C connector. It is…
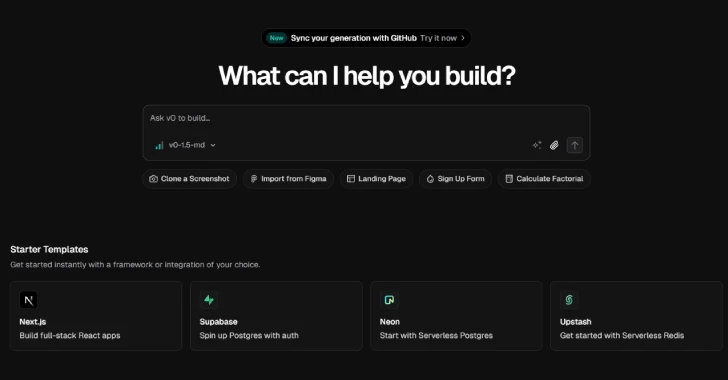
Jul 02, 2025Ravie LakshmananAI Security / Phishing Unknown threat actors have been observed weaponizing v0, a generative artificial intelligence (AI)…
By Salleh Kodri, SE Regional Manager, Cyble ASEAN is going full throttle on digital growth. From cross-border e-commerce and AI deployments…
A critical security flaw in the popular Forminator WordPress plugin has put more than 600,000 websites worldwide at risk of remote takeover,…