A newly disclosed vulnerability in Anthropic’s Model Context Protocol (MCP) Inspector tool has sent shockwaves through the AI development community,…
In this Help Net Security interview, Alexander Clemm, Corp GRC Lead, Group CISO, and BCO at Riverty, shares how the…
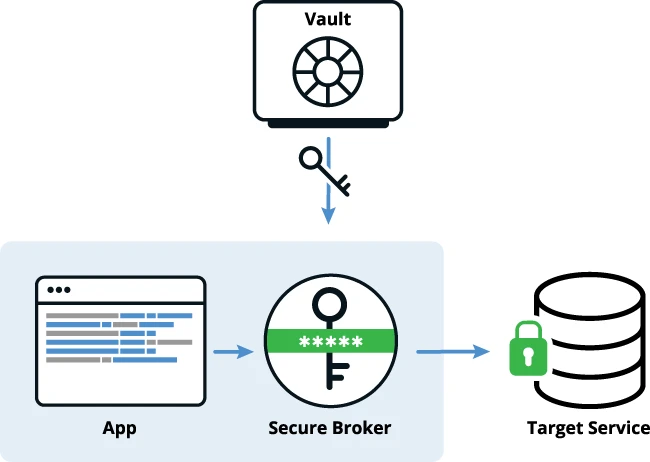
Secretless Broker is an open-source connection broker that eliminates the need for client applications to manage secrets when accessing target…
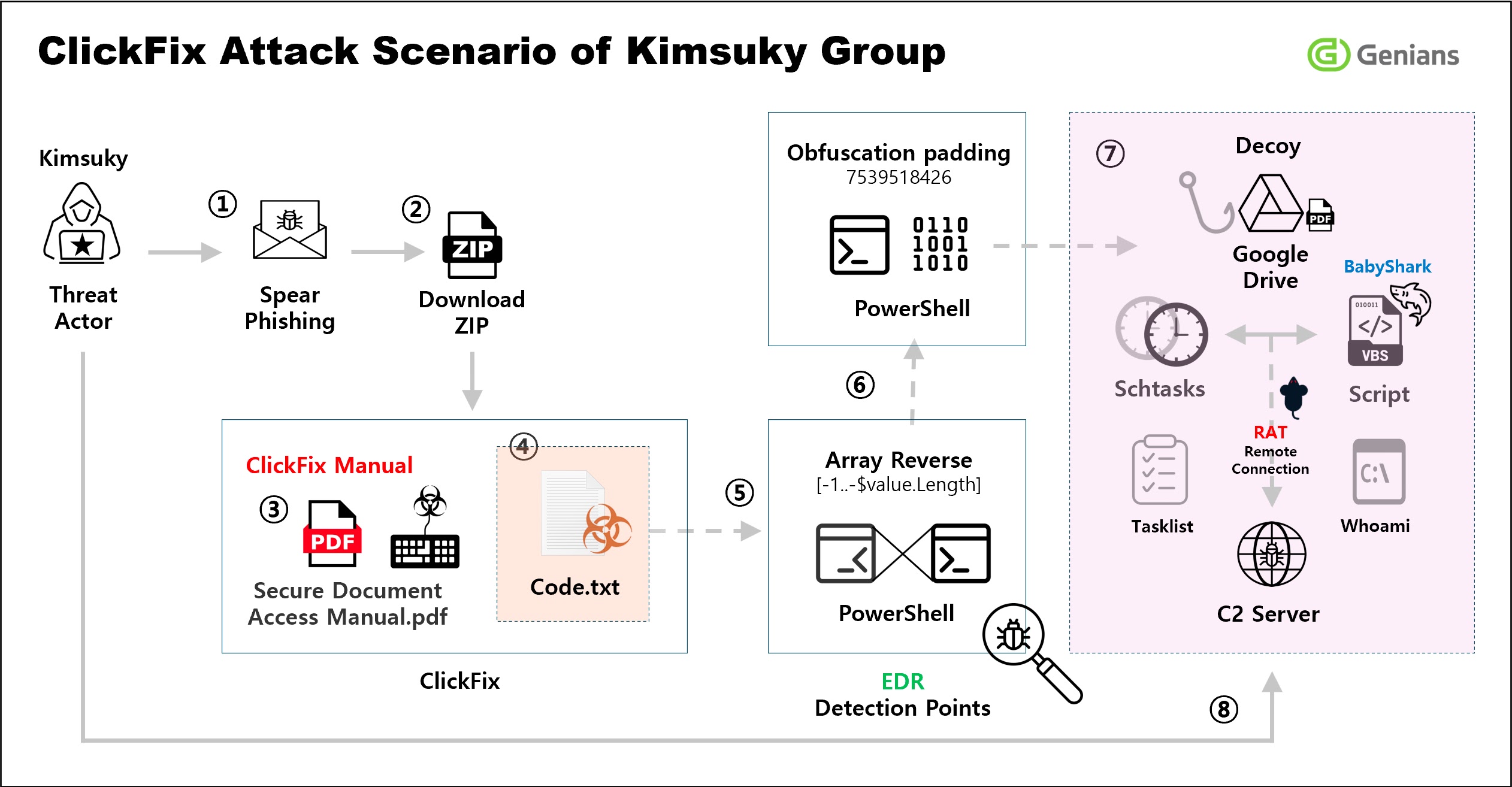
The notorious North Korean threat group Kimsuky has adopted a sophisticated social engineering tactic known as “ClickFix” to deceive users…
Not long ago, travelers worried about bad weather. Now, they’re worried the rental they booked doesn’t even exist. With AI-generated…
Qantas has confirmed that a cyber incident has been contained in one of its contact centres, impacting customer data. In…
A critical vulnerability that allows low-privileged attackers to decrypt Chrome’s AppBound Cookie Encryption, a security feature Google introduced in July…
European law enforcement agencies have successfully dismantled a sophisticated cryptocurrency investment fraud network that laundered EUR 460 million in illicit…
NIST maintains its cryptography standards and guidelines using a periodic review process. Currently, NIST seeks your feedback on all aspects…
Australian airline Qantas disclosed that it detected a cyberattack on Monday after threat actors gained access to a third-party platform…
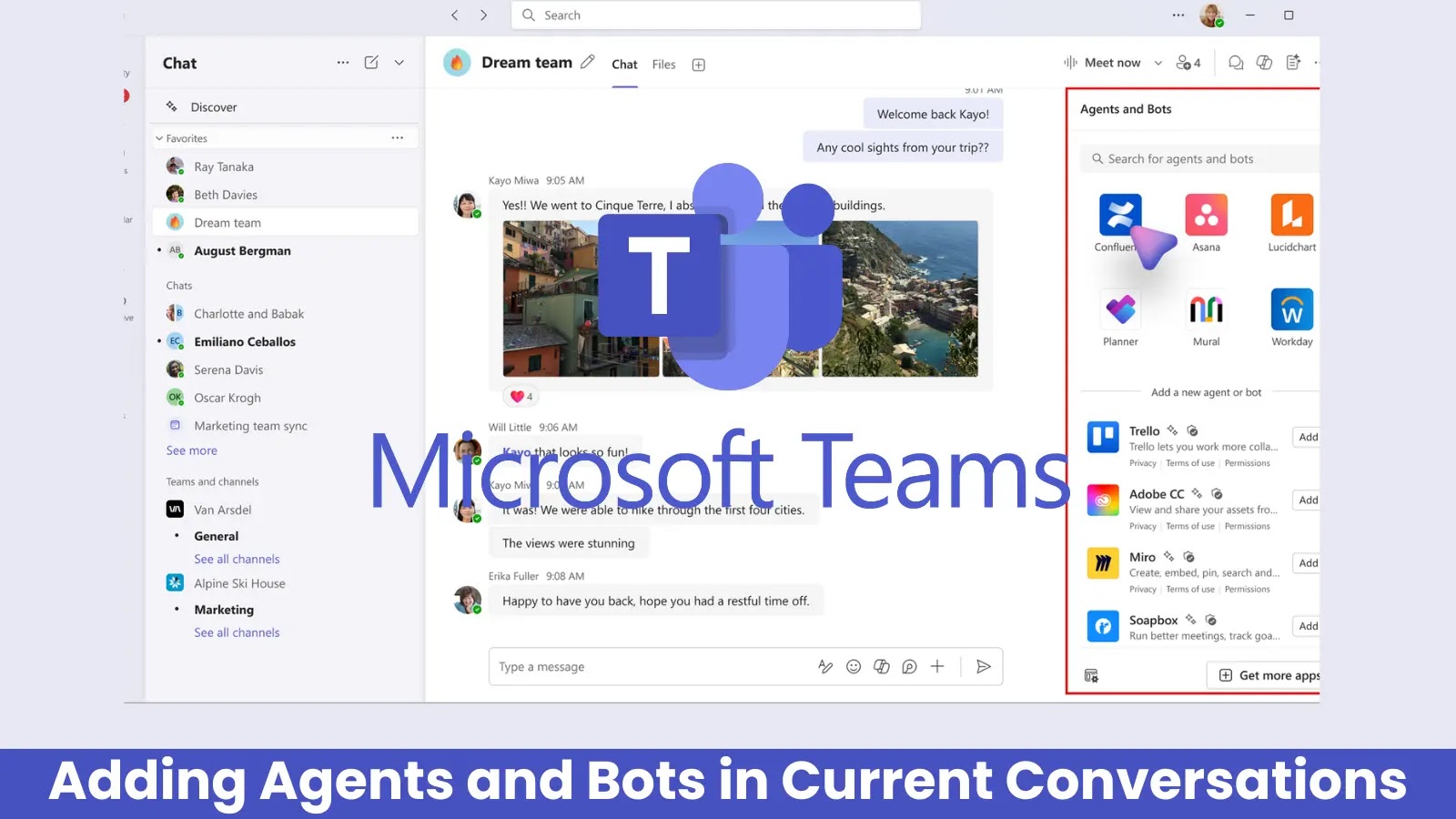
Microsoft is set to revolutionize user interaction with artificial intelligence agents and bots in Teams through a streamlined integration experience…
Linus Torvalds has released Linux kernel 6.16-rc4, marking another stable milestone in the development cycle despite what he describes as…