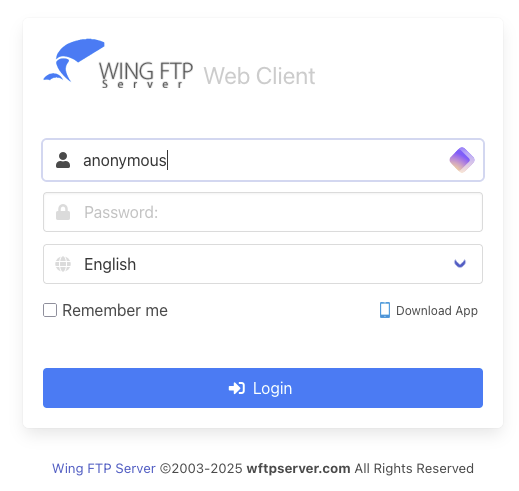
While performing a penetration test for one of our Continuous Penetration Testing customers, we’ve found a Wing FTP server instance…
Listen to the article 5 min This audio is auto-generated. Please let us know if you have feedback. The Department…
The Pi Network community eagerly celebrated Pi2Day, an event traditionally associated with platform updates, feature launches, and significant milestones. However,…
U.S. authorities unsealed indictments, seized financial accounts and made an arrest in the latest attempt to crack down on North…
The Berlin Commissioner for Data Protection has formally requested Google and Apple to remove the DeepSeek AI application from the application…
DragonForce Ransomware has emerged as a formidable player in the Ransomware-as-a-Service (RaaS) landscape since its debut in December 2023. Initially…
Cybercriminals have launched a sophisticated campaign exploiting Facebook’s advertising platform to distribute malware and steal cryptocurrency wallet credentials, targeting users…
Agents with the Federal Bureau of Investigation (FBI) briefed Capitol Hill staff recently on hardening the security of their mobile…
The rise of sophisticated digital tools and artificial intelligence has revolutionized many aspects of business and finance, but it has…
Spanish authorities have arrested five individuals in Madrid and the Canary Islands, suspected of laundering $540 million (€460 million) from illegal…
A sophisticated new phishing campaign has emerged, leveraging obsolete Windows file formats and advanced evasion techniques to distribute the notorious…
This week on the Lock and Code podcast… There’s a unique counter response to romance scammers. Her name is Becky…