A comprehensive follow-up analysis to the FortiGuard Incident Response Team’s (FGIR) investigation titled “Intrusion into Middle East Critical National Infrastructure”…
Scattered Spider, the teenaged hacking collective behind recent cyber attacks on UK retailers Marks and Spencer (M&S) and Co-op, appears…
Hackers associated with “Scattered Spider” tactics have expanded their targeting to the aviation and transportation industries after previously attacking insurance…
Belgian-Dutch supermarket operator Ahold Delhaize has revealed that the personal data of over two million individuals was compromised in a…
A critical and closely watched vulnerability in Citrix NetScaler has reached the early stages of active exploitation, according to a…
Jun 27, 2025Ravie LakshmananThreat Hunting / Vulnerability Threat hunters have discovered a network of more than 1,000 compromised small office…
When Chris Loake joined Hiscox in November 2023 as the company’s group information officer, the insurance firm had already begun…
Three out of four companies have building management systems vulnerable to hacking or cyberattack, according to a new research paper…
Starting June 9, 2025, Russian internet service providers (ISPs) began throttling access to websites and services protected by Cloudflare, making…
If you try to access Pornhub, one of the world’s biggest websites, from any of 17 US states, you’ll be…
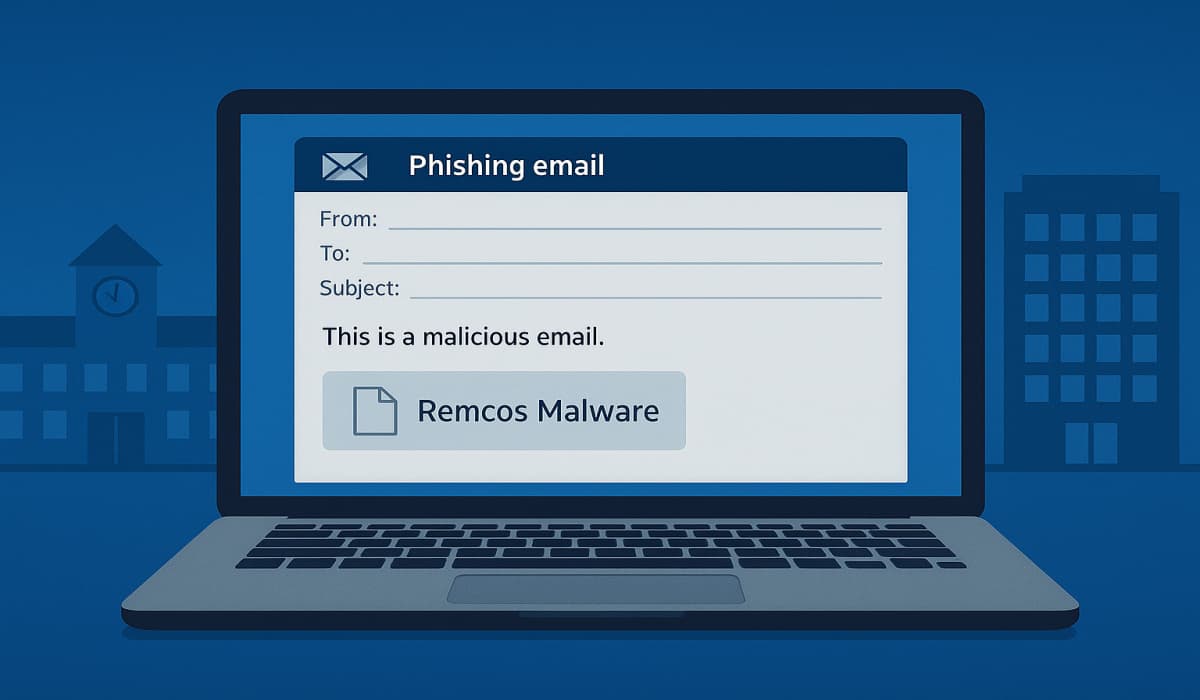
Forcepoint’s X-Labs reveals Remcos malware using new tricky phishing emails from compromised accounts and advanced evasion techniques like path bypass…
On my daily rounds, I encountered a phishing attempt that used a not completely unusual, yet clever delivery method. What…