Ahold Delhaize, one of the world’s largest food retail chains, is notifying over 2.2 million individuals that their personal, financial,…
After nearly four decades as a symbol of frustration and failure for PC users worldwide, Microsoft is officially retiring the…
Jun 27, 2025Ravie LakshmananNetwork Security / Vulnerability Threat intelligence firm GreyNoise is warning of a “notable surge” in scanning activity…
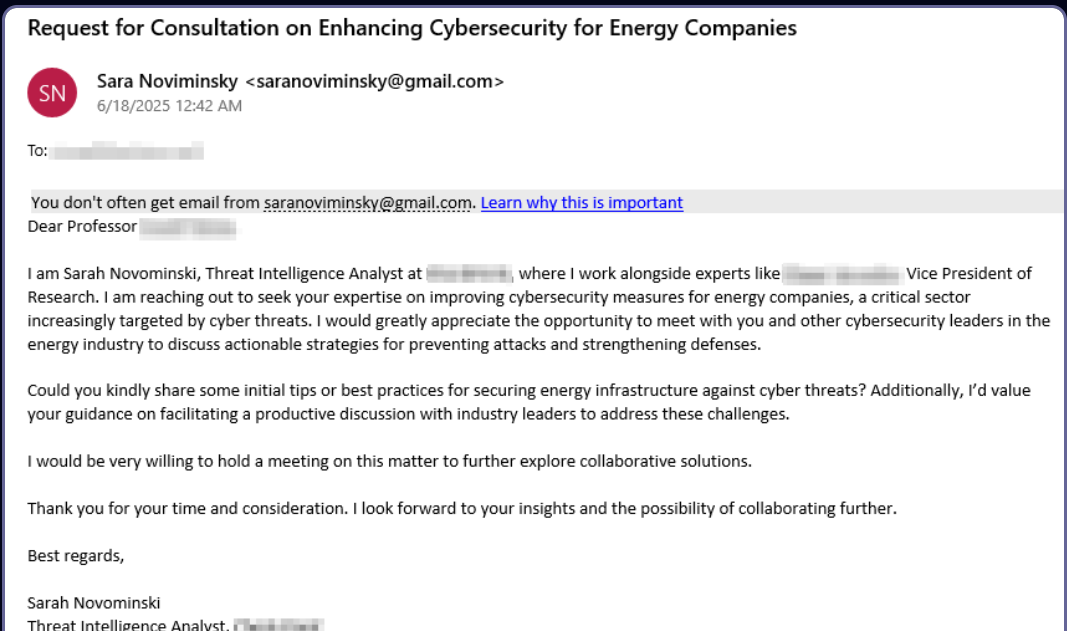
APT42 impersonates cyber professionals to phish Israeli academics and journalists Pierluigi Paganini June 27, 2025 Iran-linked APT42 targets Israeli experts…
Microsoft has released the KB5060829 preview cumulative update for Windows 11 24H2, which includes 38 changes, including improvements to the…
A critical security vulnerability has been discovered in multiple Mitsubishi Electric air conditioning systems, potentially allowing hackers to bypass authentication…
Cybersecurity researchers have detailed a new campaign dubbed OneClik that leverages Microsoft’s ClickOnce software deployment technology and bespoke Golang backdoors…
A 27-year-old former student of Western Sydney University has been charged with a string of cyber offences, following an extensive…
American grocery wholesale giant United Natural Foods (UNFI) reports that it has restored its core systems and brought online the…
A critical pre-authentication vulnerability (CVE-2025-6709) in MongoDB Server enables unauthenticated attackers to trigger denial-of-service (DoS) conditions by exploiting improper input…
In this Help Net Security interview, Michal Tresner, CEO of ThreatMark, discusses how cybercriminals are weaponizing AI, automation, and social…
Hawaiian Airlines, the tenth-largest commercial airline in the United States, is investigating a cyberattack that has disrupted access to some…