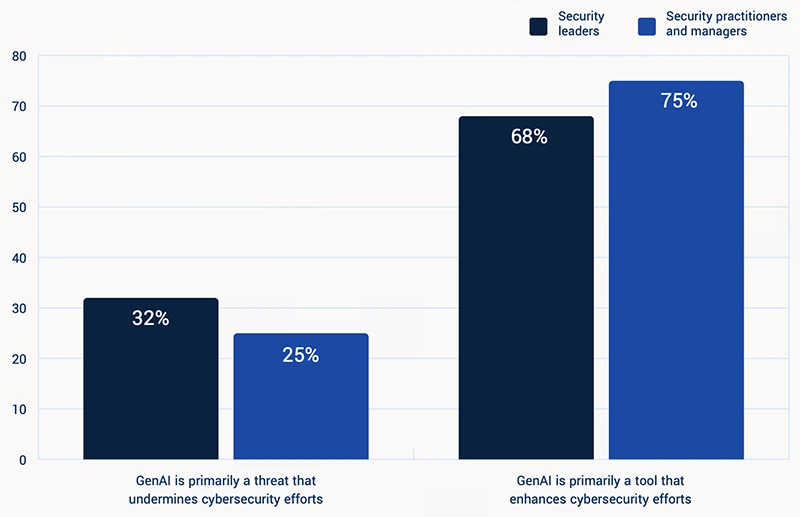
Even though GenAI threats are a top concern for both security teams and leadership, the current level of testing and…
A newly disclosed critical vulnerability in the Open VSX Registry, the open-source marketplace for Visual Studio Code (VS Code) extensions,…
Attackers are more inclined to “log in rather than break in,” using stolen credentials, legitimate tools, and native access to…
The Audit Office of New South Wales has published a report that presents its analysis of the NSW Cyber Security…
Here’s a look at the most interesting products from the past month, featuring releases from: Akamai, AttackIQ, Barracuda Networks, BigID,…
Check Point Research has identified the first documented case of malware embedding prompt injection to evade AI detection. The malware…
Despite soaring use of artificial intelligence in the workplace, most organisations remain critically unprepared to manage the risks, according to…
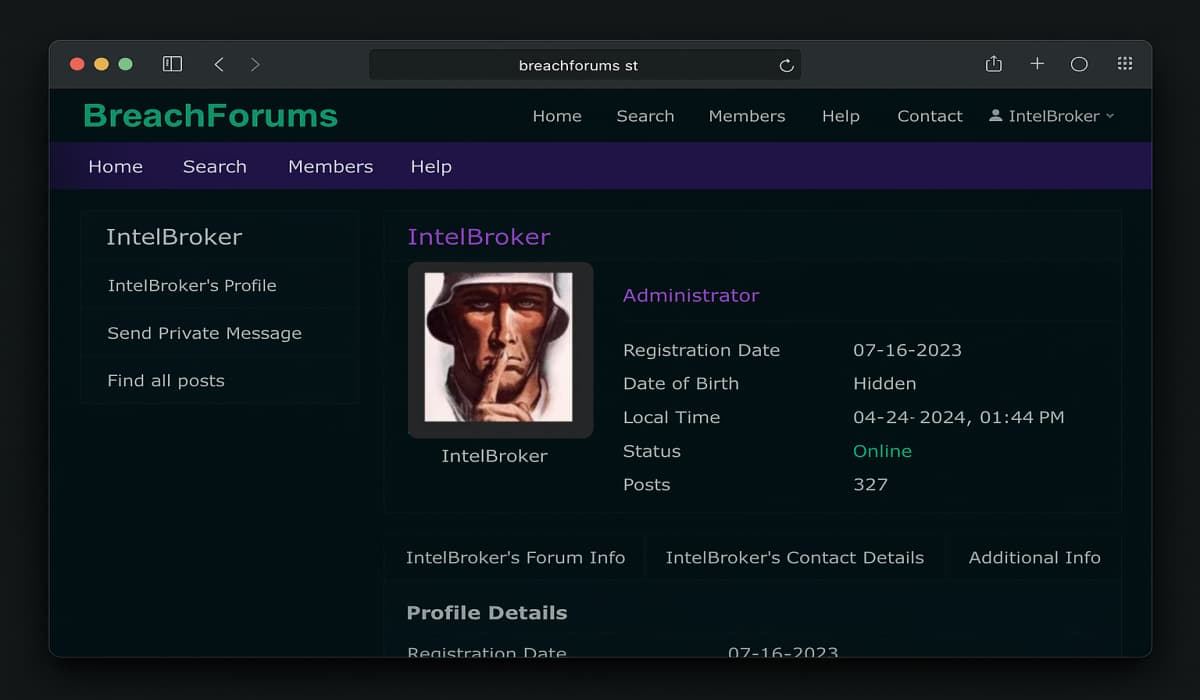
Authorities in the United States have charged a British national, Kai Logan West, widely known online as “IntelBroker“, with a…
Police are currently investigating 45 people in relation to potential crimes in the Post Office scandal, with seven so far…
The federal government has topped up its volume sourcing agreement with Microsoft by another $25 million through a fresh one-year…
The Federal Trade Commission (FTC) has approved $126,000,000 in refunds to be sent to 969,173 Fortnite players as part of…
Researchers at BallisKit have introduced a sophisticated scenario within their MacroPack Pro tool to obfuscate and weaponize .NET assemblies, significantly…