Cybersecurity researchers have discovered a groundbreaking new malware strain that represents the first documented attempt to weaponize prompt injection attacks…
Kanister is an open-source tool that lets domain experts define how to manage application data using blueprints that are easy…
French authorities have dismantled a major cybercrime operation, arresting five hackers who operated BreachForum, one of the world’s largest marketplaces…
60% of enterprise SaaS and AI applications operate outside IT’s visibility, according to CloudEagle.ai. This surge in invisible IT is…
Adelaide University – the result of a merger of the University of Adelaide and the University of South Australia – has…
Don’t get me wrong—Cursor is genuinely awesome. It’s probably the best AI-native code editor ever built, with incredibly thoughtful integrations…
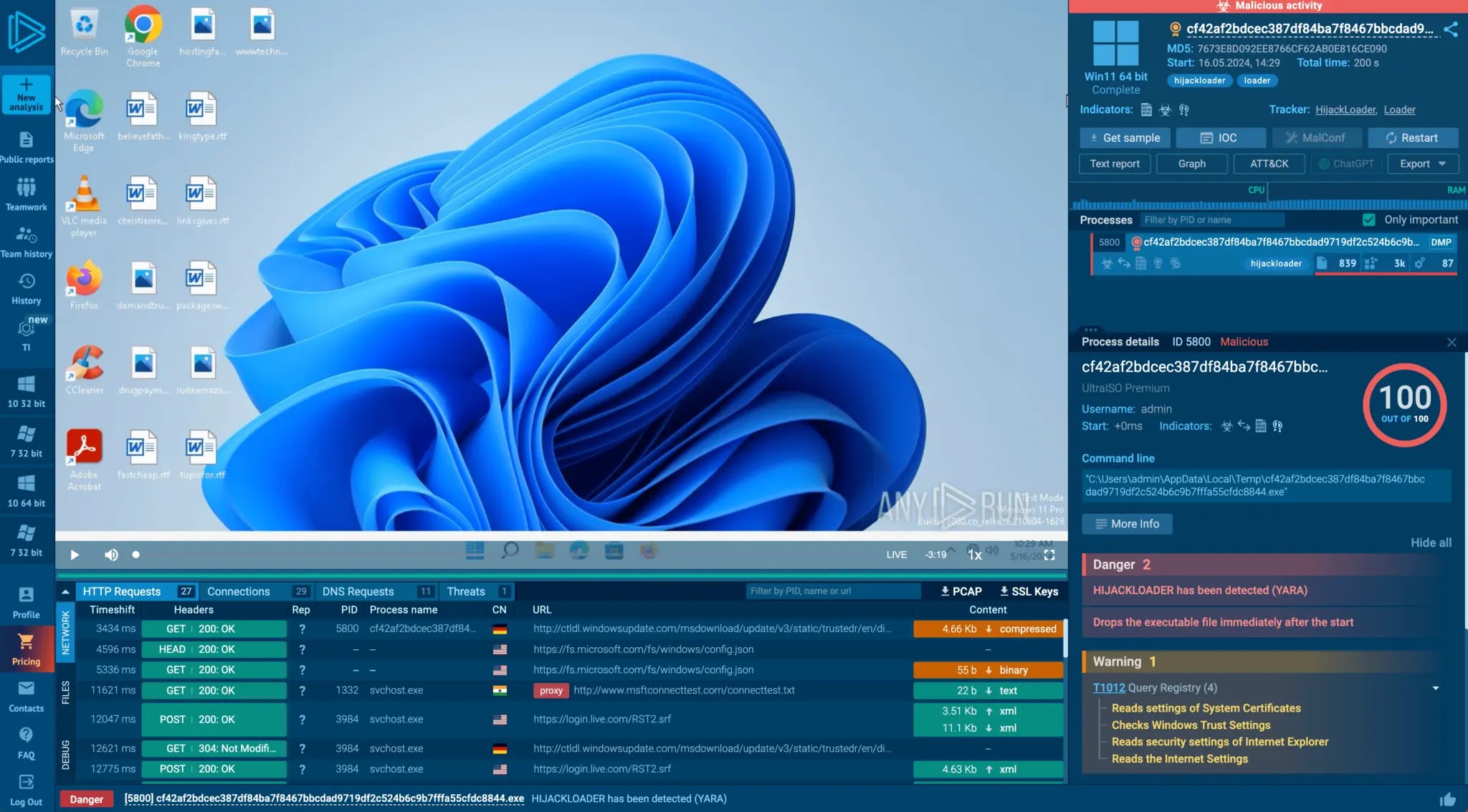
Security researchers at ANY.RUN have uncovered a new malware campaign delivering the BRAODO Stealer, which relies on public GitHub repositories…
Mozilla has released Firefox 140, addressing multiple critical security vulnerabilities, including a high-impact use-after-free vulnerability that could lead to code…
The director of security strategy for Asia Pacific and Japan at Akamai Technologies says the end of the financial year…
A significant security vulnerability has been identified in Realtek’s RTL8762E SDK v1.4.0 that allows attackers to exploit the Bluetooth Low…
Cybersecurity company Sophos has released its sixth annual State of Ransomware report, a vendor-agnostic survey of IT and cybersecurity leaders…
A 27-year-old former student of Western Sydney University has been charged over a series of cyberattacks that impacted the educational…