Security teams are optimistic about AI’s impact on their careers, but workloads remain high. Tines’ Voice of Security 2026 report…
Targeted victims: LockBit targeted thousands of victims worldwide in its heyday, including government services, private sector companies, and critical infrastructure…
Lessons from Clop It’s been one month since the Clop ransomware group began exploiting the MOVEit vulnerability (CVE-2023-34362 (VulnDB ID:…
Special thanks to Austin Worline for his contributions to this blog post. The Huntress Security Operations Center (SOC) frequently comes…
ExifTool Flaw Malicious Images Trigger Code Execution on macOS A newly discovered vulnerability is challenging the long-held belief that macOS…
In this post we’ll show you how to bypass CSP by using an often overlooked technique that can enable password…
A critical Cross-Site Scripting (XSS) vulnerability has been discovered in ZITADEL, a popular open-source identity and access management platform. Tracked…
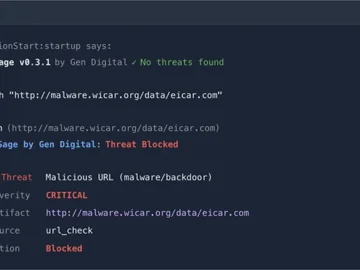
Autonomous AI agents running on developer workstations execute shell commands, fetch URLs, and write files with little or no inspection…
New research has found that Google Cloud API keys, typically designated as project identifiers for billing purposes, could be abused…
A Ghanaian national has pleaded guilty to his role in a large-scale cyber fraud scheme that used romance scams and…
Security researchers have identified a new Linux malware strain called ClipXDaemon, a stealthy threat designed to target cryptocurrency users by manipulating copied wallet…
Recorded Future is expanding its payment fraud prevention capabilities through a partnership with CYBERA, the industry leader in detecting and…