The United States has become a popular target for hacktivist groups in the escalating Israel-Iran conflict, following U.S. attacks on…
Jun 25, 2025Ravie LakshmananData Privacy / Vulnerability Cybersecurity researchers have detailed two now-patched security flaws in SAP Graphical User Interface…
Imagine being on a road trip without GPS—just a vague set of directions scribbled on a napkin and the occasional…
Mozilla has officially released Firefox 140, marking a significant update that addresses multiple security vulnerabilities, including a critical code execution…
Hundreds of data brokers haven’t registered with state consumer protection agencies, according to The Electronic Frontier Foundation (EFF) and Privacy Rights…
A critical vulnerability in Realtek’s Bluetooth Low Energy (BLE) implementation enables attackers to launch denial-of-service (DoS) attacks during device pairing….
UAE-based cybersecurity experts are urging companies to boost password security to stay ahead of emerging threats in every aspect of operations,…
OpenRouter, a startup helping software developers manage the growing number of AI models, has raised $40 million in venture capital….
If you invite guest users into your Entra ID tenant, you may be opening yourself up to a surprising risk….
The Chrome team has announced the rollout of a critical security update for its popular web browser, Chrome, addressing 11…
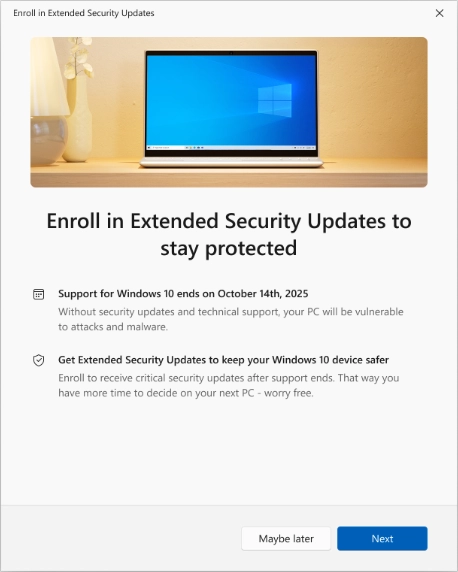
Users who want to stick with Windows 10 beyond its planned end-of-support date but still receive security updates, can enroll…
If you invite guest users into your Entra ID tenant, you may be opening yourself up to a surprising risk….