A critical security flaw has been uncovered in Kibana, the popular data visualization platform for the Elastic Stack, exposing organizations…
Jun 25, 2025Ravie LakshmananMalware / Open Source Cybersecurity researchers have uncovered a fresh batch of malicious npm packages linked to…
Prometei botnet activity has surged since March 2025 Pierluigi Paganini June 25, 2025 Prometei botnet activity has surged since March…
A critical security vulnerability has been discovered in TeamViewer Remote Management for Windows, exposing systems to potential privilege escalation attacks….
Cybersecurity researchers have discovered a highly advanced malware campaign targeting WordPress websites, capable of stealing credit card details, user logins,…
The Cybersecurity and Infrastructure Security Agency (CISA) has released eight new Industrial Control Systems (ICS) advisories on June 24, 2025,…
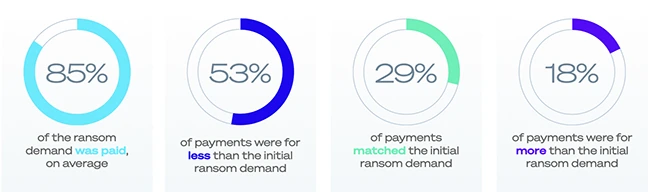
Nearly 50% of companies paid the ransom to recover their data, the second-highest rate in six years, according to Sophos….
NVIDIA has issued an urgent security update for its open-source Megatron-LM framework, following the discovery of two critical vulnerabilities that…
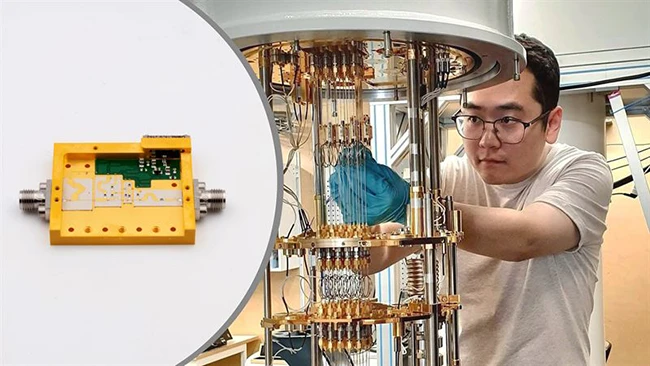
Quantum computers are built to handle problems that are far too complex for today’s machines. They could lead to major…
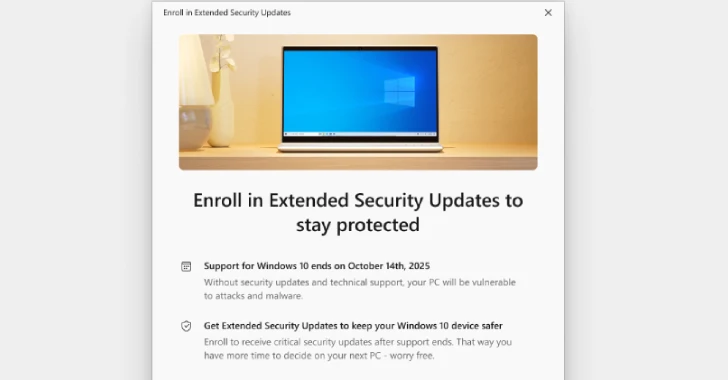
Jun 25, 2025Ravie LakshmananEndpoint Security / IT Management Microsoft on Tuesday announced that it’s extending Windows 10 Extended Security Updates…
A newly discovered exploit, dubbed “FileFix,” is raising alarms in the cybersecurity community for its innovative use of Windows File…
In this Help Net Security interview, Rinki Sethi, Chief Security Officer at Upwind, discusses how runtime platforms help CISOs shift…