Australia’s internet watchdog and YouTube exchanged barbs after the regulator urged the government to reverse a planned exemption for the…
Demystifying Cyber Risk: How Qualys is Transforming Security Leadership Cybersecurity leadership is undergoing a profound transformation. No longer confined to…
Cybersecurity researchers at Kaspersky have reported a new spyware operation, dubbed SparkKitty, that has infected apps available on both the…
Jun 24, 2025Ravie LakshmananSocial Media / Privacy The United States Embassy in India has announced that applicants for F, M,…
Trezor is alerting users about a phishing campaign that abuses its automated support system to send deceptive emails from its…
British businesses are suffering significantly more damaging losses from ransomware attacks compared to the rest of the world, where things…
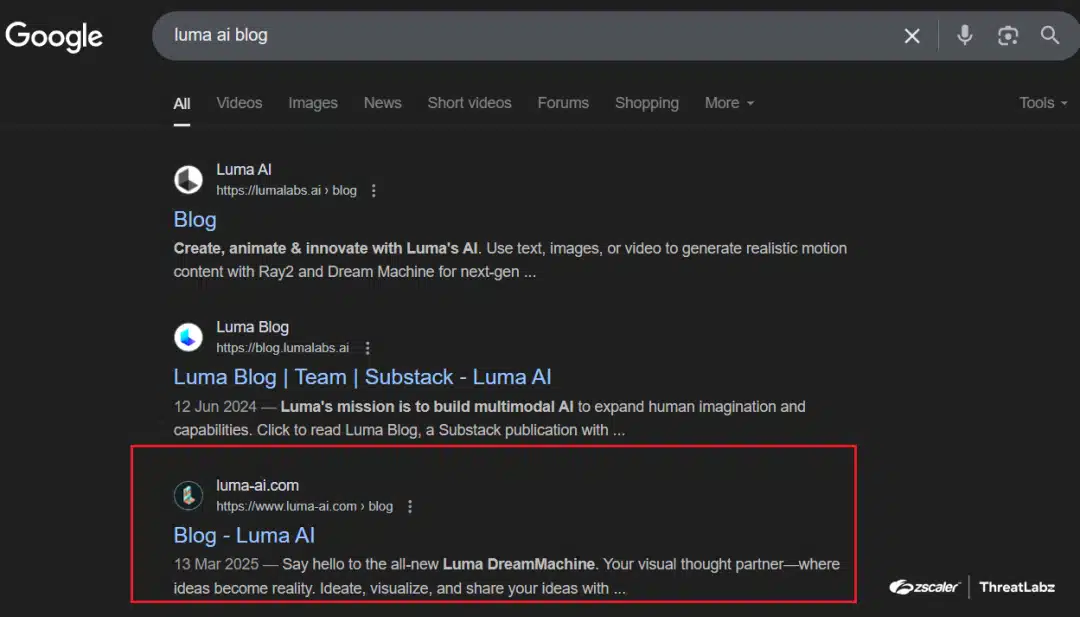
Threat actors are hijacking Google search results for popular AI platforms like ChatGPT and Luma AI to deliver malware, in…
Microsoft says Windows 10 home users who want to delay switching to Windows 11 can enroll in the Extended Security Updates…
The U.S. House banned WhatsApp on government devices due to security concerns Pierluigi Paganini June 24, 2025 The U.S. House…
Microsoft has released the June 2025 non-security preview update for Windows 10, version 22H2, with fixes for bugs preventing the…
A critical security vulnerability has been discovered in Zimbra Classic Web Client that enables attackers to execute arbitrary JavaScript code…
A notorious threat actor known as “xperttechy” is actively promoting a new version of the EagleSpy remote access Trojan (RAT),…