Jun 24, 2025Ravie LakshmananMalware / Threat Intelligence The Computer Emergency Response Team of Ukraine (CERT-UA) has warned of a new…
Under the Digital Markets Competition Regime, the Competition and Markets Authority (CMA) has proposed to designate Google with “strategic market…
The Open Web Application Security Project (OWASP) has announced the development of a comprehensive OWASP AI Testing Guide, marking a…
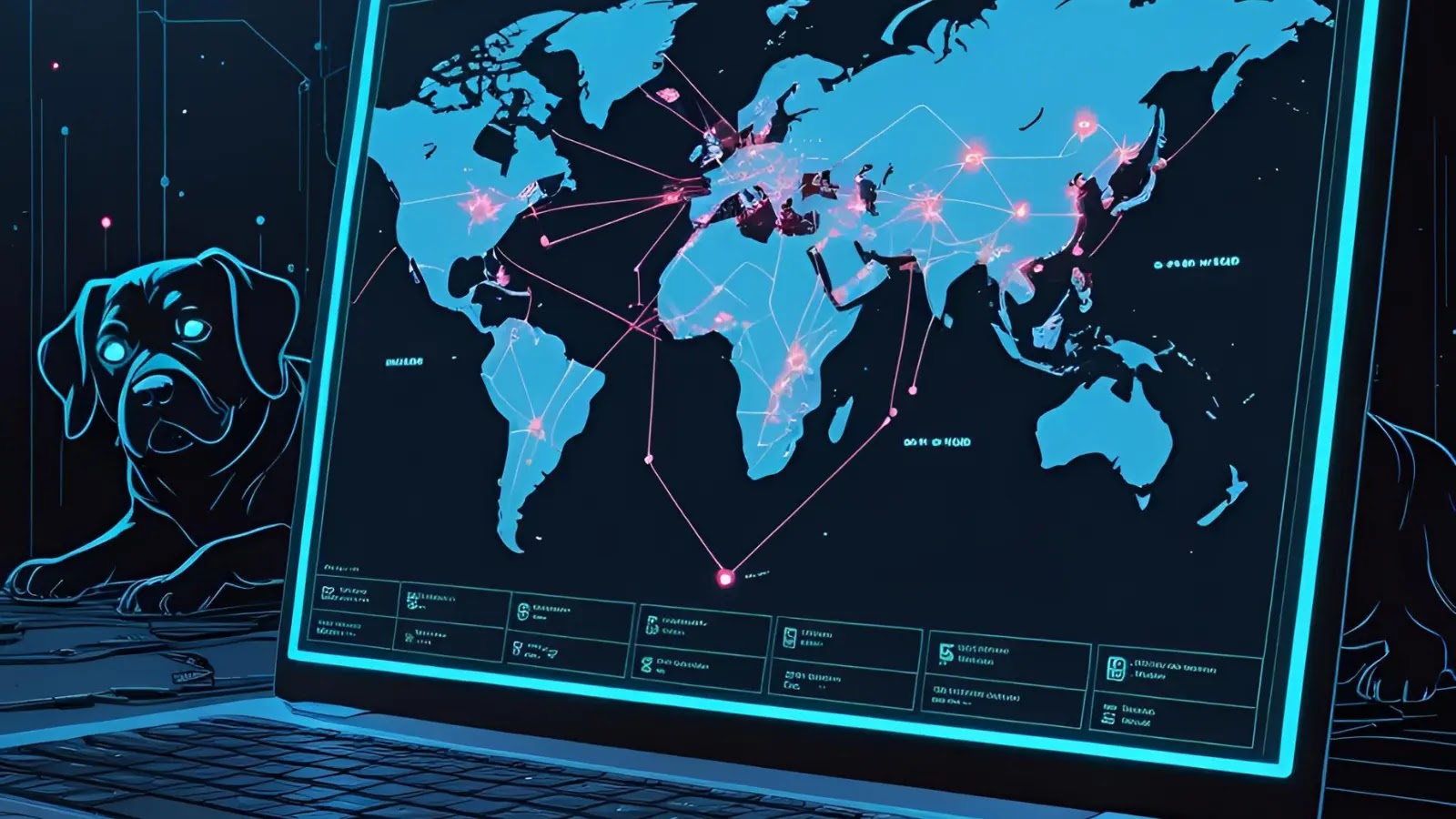
Security researchers at SecurityScorecard have uncovered a sprawling cyber-espionage campaign orchestrated by the LapDogs Operational Relay Box (ORB) Network, a…
Jun 24, 2025Ravie LakshmananData Protection / Mobile Security The U.S. House of Representatives has formally banned congressional staff members from…
U.S. warns of incoming cyber threats following Iran airstrikes Pierluigi Paganini June 24, 2025 U.S. warns of cyberattacks by pro-Iranian…
The Wordfence Threat Intelligence Team uncovered a sophisticated malware campaign during a routine site cleanup, revealing a family of malicious…
The Common Good Cyber Fund is a new effort to support cybersecurity that protects everyone, especially those most at risk…
Thank you for joining! Access your Pro+ Content below. 24 June 2025 Digital ID: cool or contentious? Share this item…
China-linked APT Salt Typhoon targets Canadian Telecom companies Pierluigi Paganini June 24, 2025 Canada and FBI warn of China-linked APT…
Organizations are adopting bug bounty programs more and more as part of a layered security strategy to address the skills…
Summary 1. A high-severity flaw (CVE-2025-6218) in WinRAR allows attackers to execute arbitrary code by exploiting how the software handles…