The U.S. Department of Homeland Security (DHS) warned over the weekend of escalating cyberattack risks by Iran-backed hacking groups and…
Ukrainian government agencies have fallen victim to a sophisticated cyberattack campaign orchestrated by the UAC-0001 group, also known as APT28,…
Cybersecurity researchers have uncovered a sophisticated spearphishing campaign orchestrated by the North Korean threat group Kimsuky, leveraging GitHub as a…
Newark, United States, June 23rd, 2025, CyberNewsWire The OpenSSL Corporation and the OpenSSL Foundation are issuing a final call for…
Jun 23, 2025Ravie LakshmananLLM Security / AI Security Cybersecurity researchers are calling attention to a new jailbreaking method called Echo…
A summary of common security vulnerabilities in GraphQL and their mitigation strategies. GraphQL provides superior flexibility and efficiency compared to…
Dive Brief: Most businesses are expanding their AI portfolios as leaders try to capture the technology’s benefits, according to a…
The Canadian Centre for Cyber Security and the FBI confirm that the Chinese state-sponsored ‘Salt Typhoon’ hacking group is also targeting Canadian telecommunication…
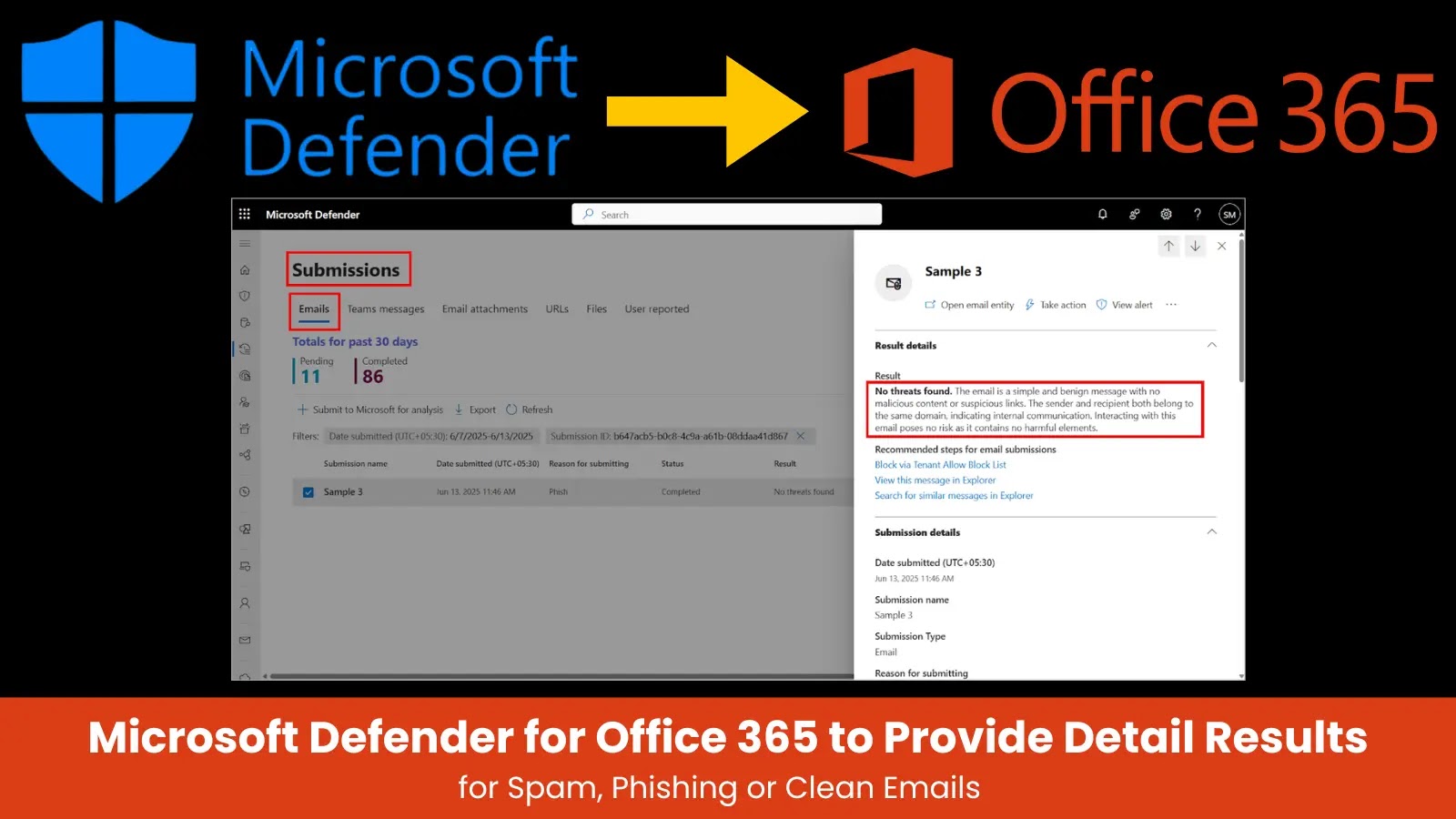
Summary 1. Microsoft Defender for Office 365 is introducing large language model (LLM) technology to provide clear, human-readable explanations for…
McLaren Health Care, a prominent healthcare provider based at One McLaren Parkway, Grand Blanc, MI, has disclosed a data breach…
In this article, I’ll explain Server-Sent Events (SSE), one of the technologies for implementing real-time data communication in web applications….
Four REvil ransomware members arrested in January 2022 were released by Russia on time served after they pleaded guilty to…