A guide to understanding and implementing Subresource Integrity (SRI) for enhanced web security. Subresource Integrity (SRI) is a security feature…
Nucor, North America’s largest steel producer and recycler, has confirmed that attackers behind a recent cybersecurity incident have also stolen…
There are multiple initiatives in the USA and European Union to regulate the Open-source AI use – from an ethics…
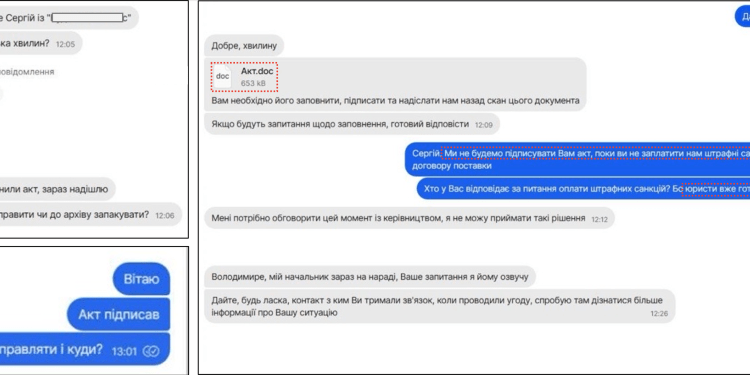
The Field Effect Analysis team has uncovered a targeted social engineering campaign orchestrated by the North Korean state-sponsored threat actor…
Globally, the cost of cybercrime was projected to reach $9.5 trillion in 2024 and $10.5 trillion in 2025, according to Cybersecurity Ventures…
It sure is a hard time to be a SOC analyst. Every day, they are expected to solve high-consequence problems…
Russia-linked hackers are back at it again, this time with upgraded tools and a stealthier playbook targeting Ukrainian government systems….
American steel giant Nucor confirms data breach in May attack Pierluigi Paganini June 23, 2025 American steel giant Nucor confirms…
Learn about Content Security Policy (CSP), its importance, how it works, and how it enhances web security. What is Content…
The highly anticipated IPFire 2.29 – Core Update 194 has officially landed, delivering a significant upgrade for users of the…
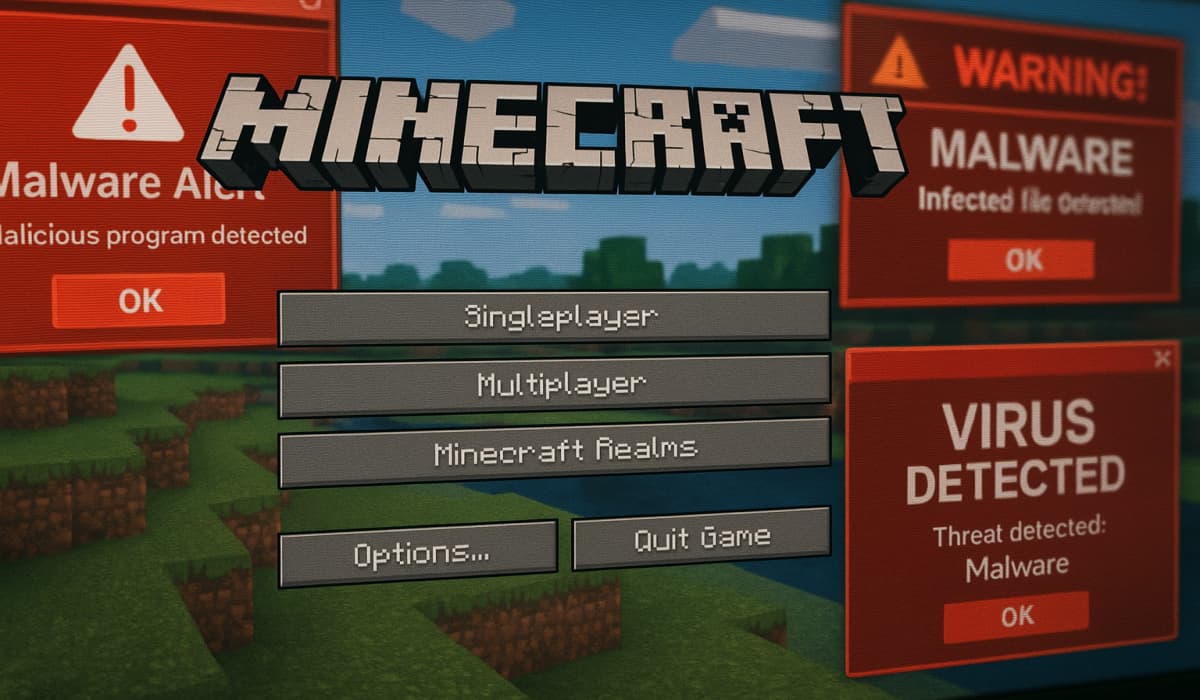
A new malware campaign has been targeting Minecraft players through fake mod downloads, according to recent findings from Check Point…
At last week’s Leti Innovation Days (LID) 2025 event in Grenoble, power consumption was on everyone’s mind. With artificial…