A newly identified cyber threat linked to a China-based threat actor has emerged, targeting users across East and Southeast Asia…
China’s National Cybersecurity Notification Center has issued an urgent warning about critical vulnerabilities in ComfyUI, a widely used image-generation framework…
The infamous Anubis ransomware gang has listed Disneyland Paris as its latest victim. Hackread.com can confirm that the group posted…
In a Russia’s dairy supply chain, a suspected cyberattack has targeted the Mercury component of the national veterinary certification system,…
Insurance giant Aflac reported today that it was hit by a cyberattack on June 12 but was able to stop…
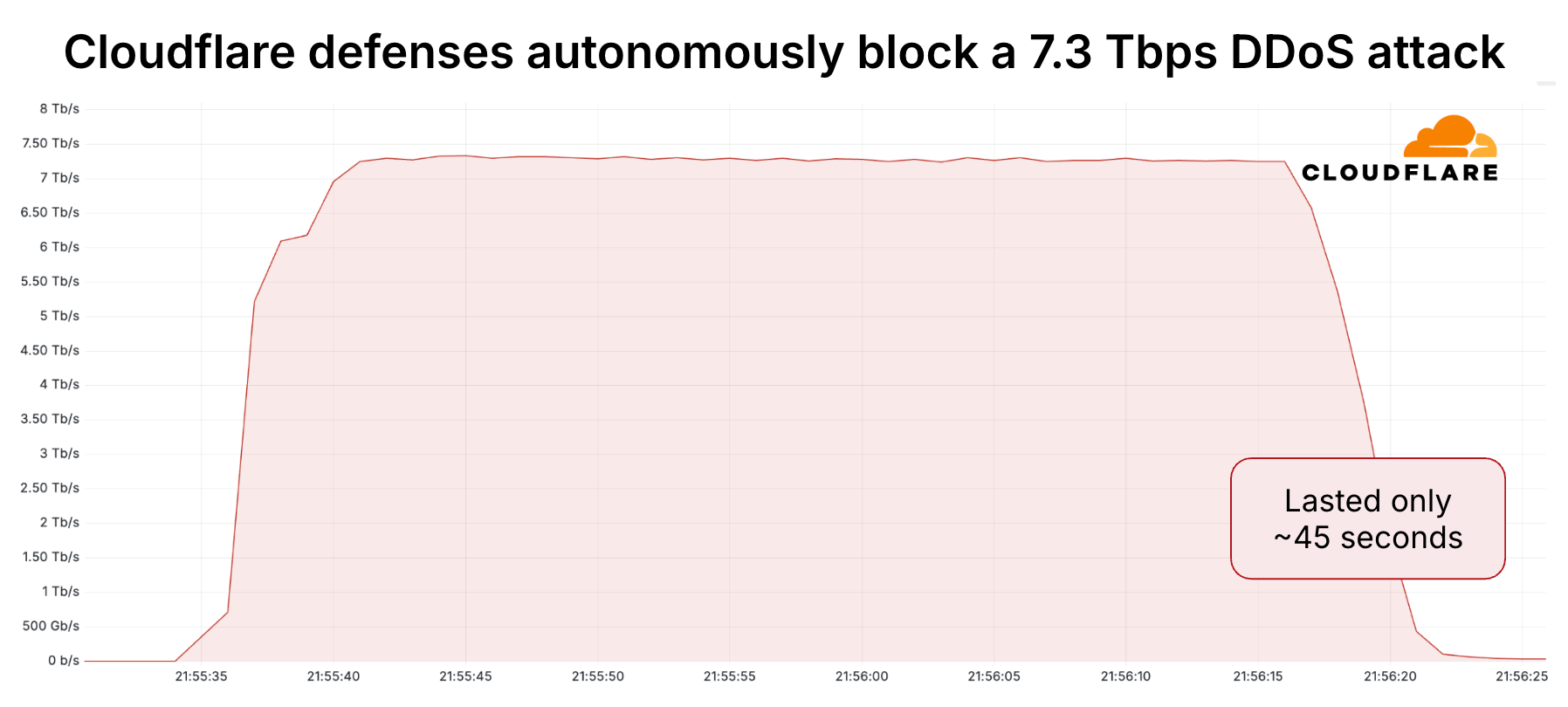
Cloudflare blocked record-breaking 7.3 Tbps DDoS attack against a hosting provider Pierluigi Paganini June 20, 2025 Cloudflare blocked a record-breaking…
Unit 42 researchers from Palo Alto Networks have identified a renewed wave of attacks by the Prometei botnet, specifically targeting…
A congressional crackdown on deepfakes continued this week with the introduction of a bipartisan Senate bill targeting financial scams that…
A malicious campaign tracked as Mocha Manakin has been identified employing the deceptive “paste-and-run” technique to trick unsuspecting users into…
A severe security vulnerability in the Insomnia API Client, a widely used tool by developers and security testers for interacting…
CyberArmor has uncovered a sophisticated phishing campaign exploiting Vercel, a widely used frontend hosting platform, to distribute a malicious variant…
The Taiwanese cryptocurrency exchange BitoPro claims the North Korean hacking group Lazarus is behind a cyberattack that led to the…