In this Help Net Security interview, Rob ter Linden, CISO at Signify, discusses priorities for CISOs working on IoT security,…
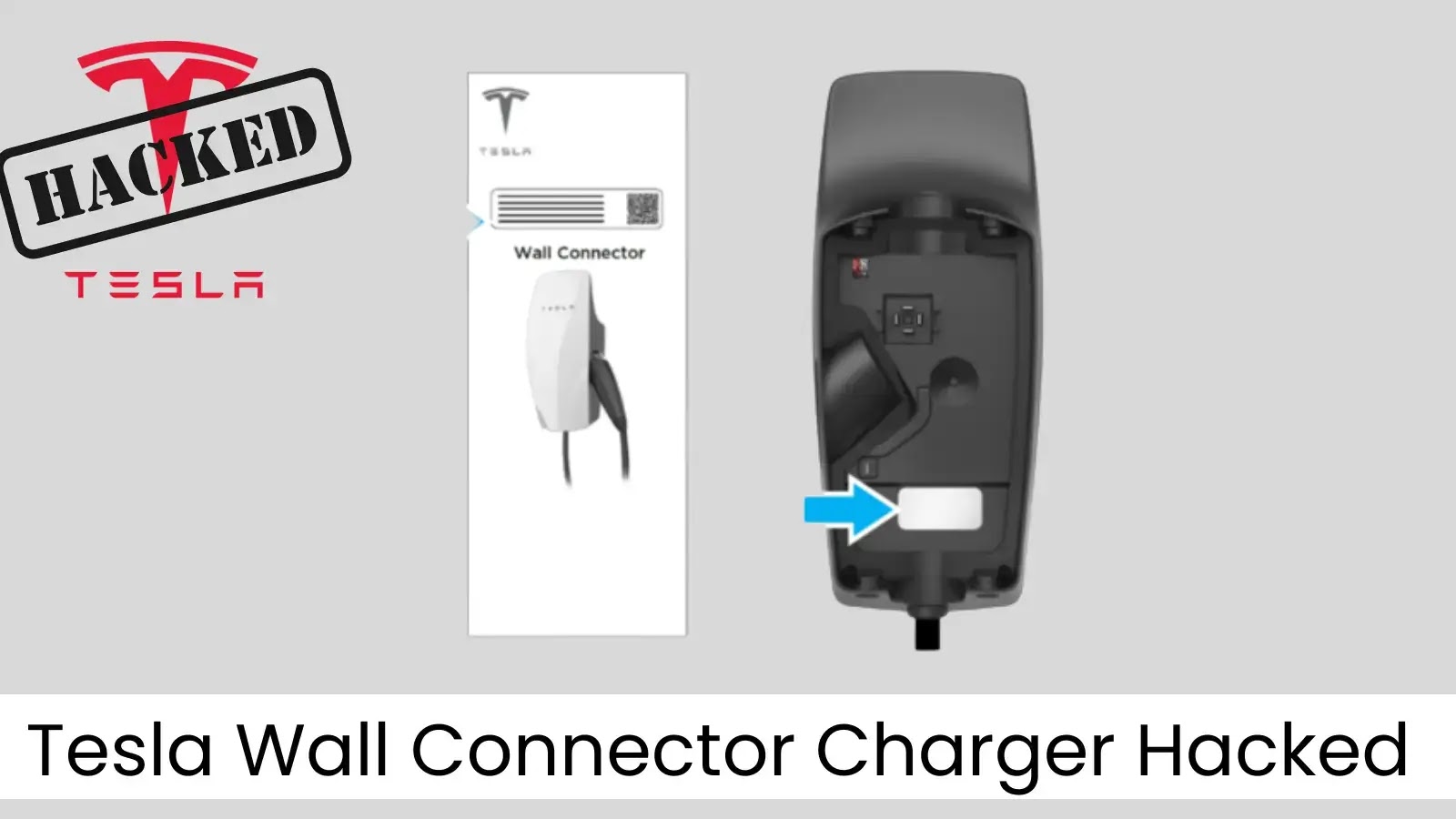
Security researchers from Synacktiv successfully hacked the Tesla Wall Connector through its charging port in just 18 minutes, exposing critical…
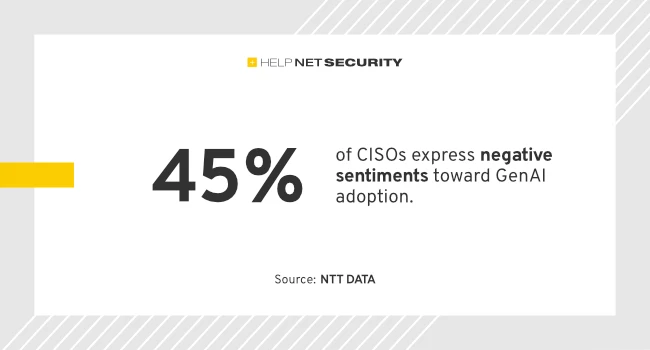
95% of C-suite leaders say that GenAI is driving a new level of innovation in their organizations, according to NTT…
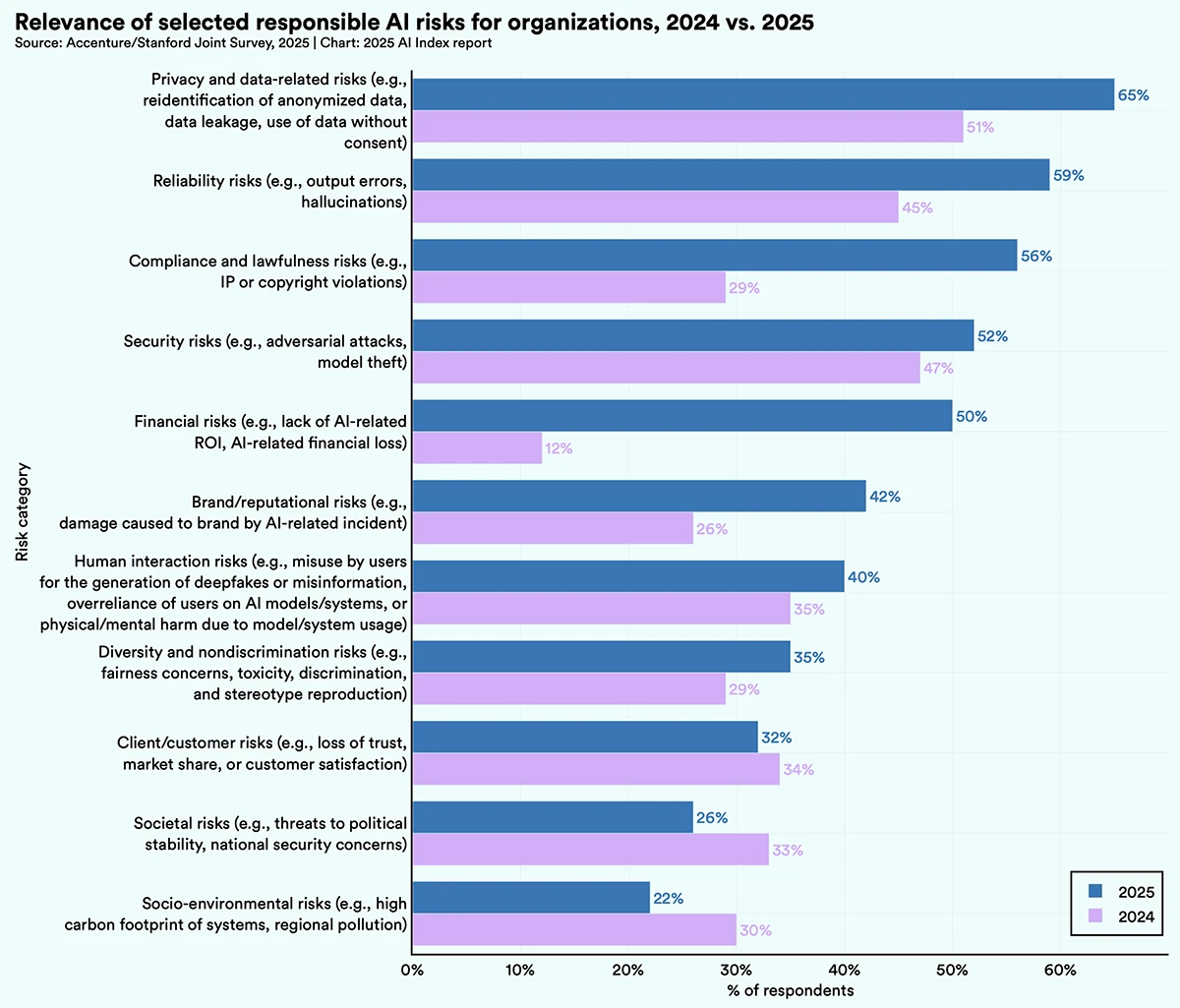
Stanford recently released its AI Index 2025, and it’s packed with insights on how AI is changing. For CISOs, it’s…
In today’s intensely interconnected digital economy, a data breach is no longer a contained technical anomaly but a profound and…
Here’s a look at the most interesting products from the past week, featuring releases from BigID, Dashlane, Sumsub, and Jumio….
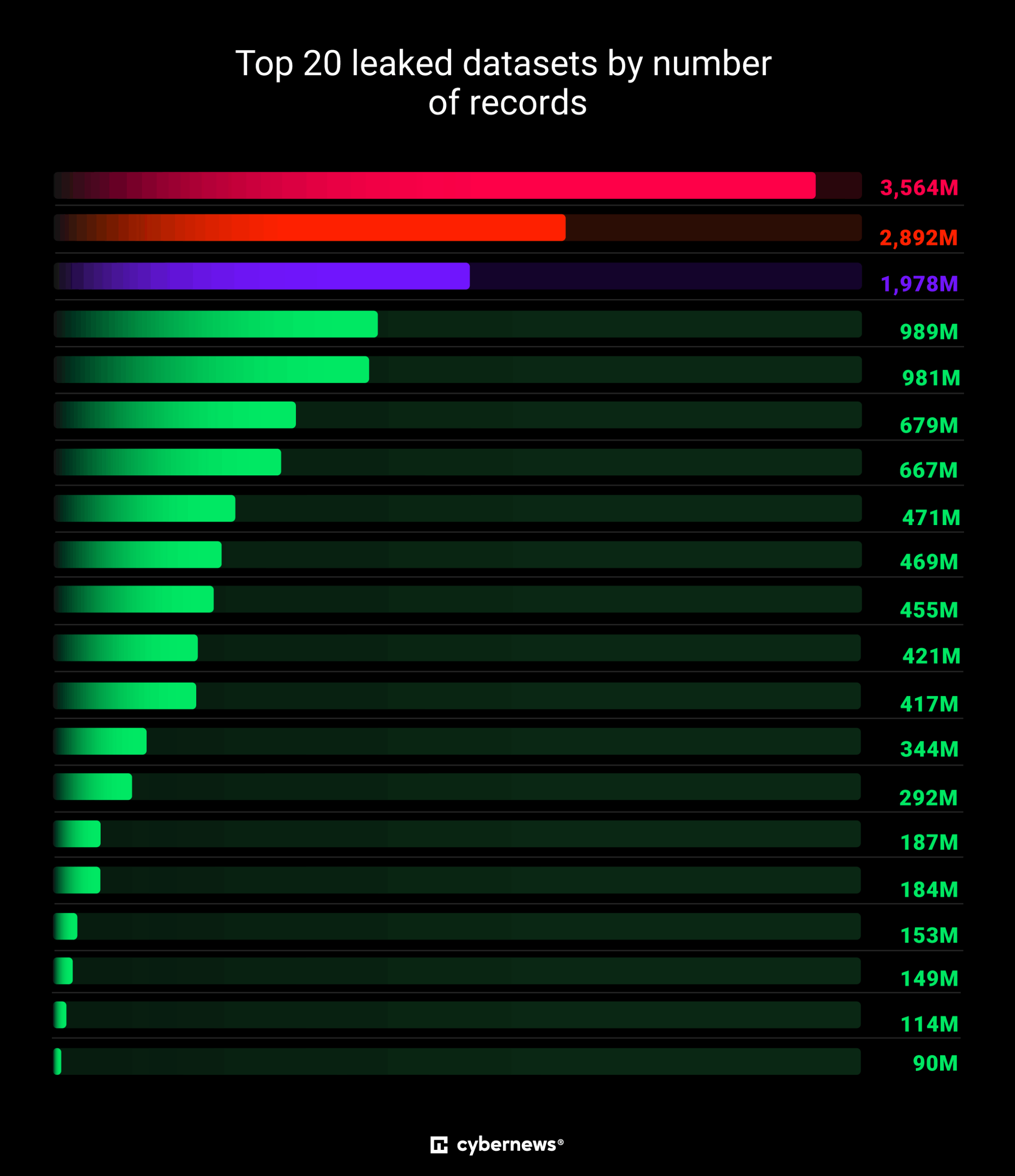
News broke today of a “mother of all breaches,” sparking wide media coverage filled with warnings and fear-mongering. However, it…
News broke today of a “mother of all breaches,” sparking wide media coverage filled with warnings and fear-mongering. However, it…
News broke today of a “mother of all breaches,” sparking wide media coverage filled with warnings and fear-mongering. However, it…
Researchers discovered the largest data breach ever, exposing 16 billion login credentials Pierluigi Paganini June 19, 2025 Researchers discovered the…
A new version of the Android malware “Godfather” creates isolated virtual environments on mobile devices to steal account data and transactions from…
The North Korean state-sponsored threat actor group, identified as TA444 (also known as BlueNoroff, Sapphire Sleet, and others), has unleashed…