Jun 19, 2025The Hacker NewsCybersecurity / Threat Hunting Most cyberattacks today don’t start with loud alarms or broken firewalls. They…
Malicious Minecraft mods distributed by the Stargazers DaaS target Minecraft gamers Pierluigi Paganini June 19, 2025 Java-based malware targets Minecraft…
A new detection method called Jitter-Trap that turns cybercriminals’ own evasion tactics against them, offering new hope in the battle…
Google Threat Intelligence Group (GTIG), in collaboration with external partners, has uncovered a sophisticated phishing campaign orchestrated by a Russia…
U.S. doughnut chain Krispy Kreme confirmed that attackers stole the personal information of over 160,000 individuals in a November 2024…
A sophisticated new variant of the Masslogger credential stealer has emerged, utilizing VBScript encoded (.VBE) files to deploy a multi-stage…
A sophisticated malware campaign dubbed SERPENTINE#CLOUD has emerged, leveraging Cloudflare Tunnel infrastructure to deliver Python-based malware to Windows systems across…
A critical security vulnerability affecting Cisco Meraki MX and Z Series devices could allow unauthenticated attackers to launch denial of…
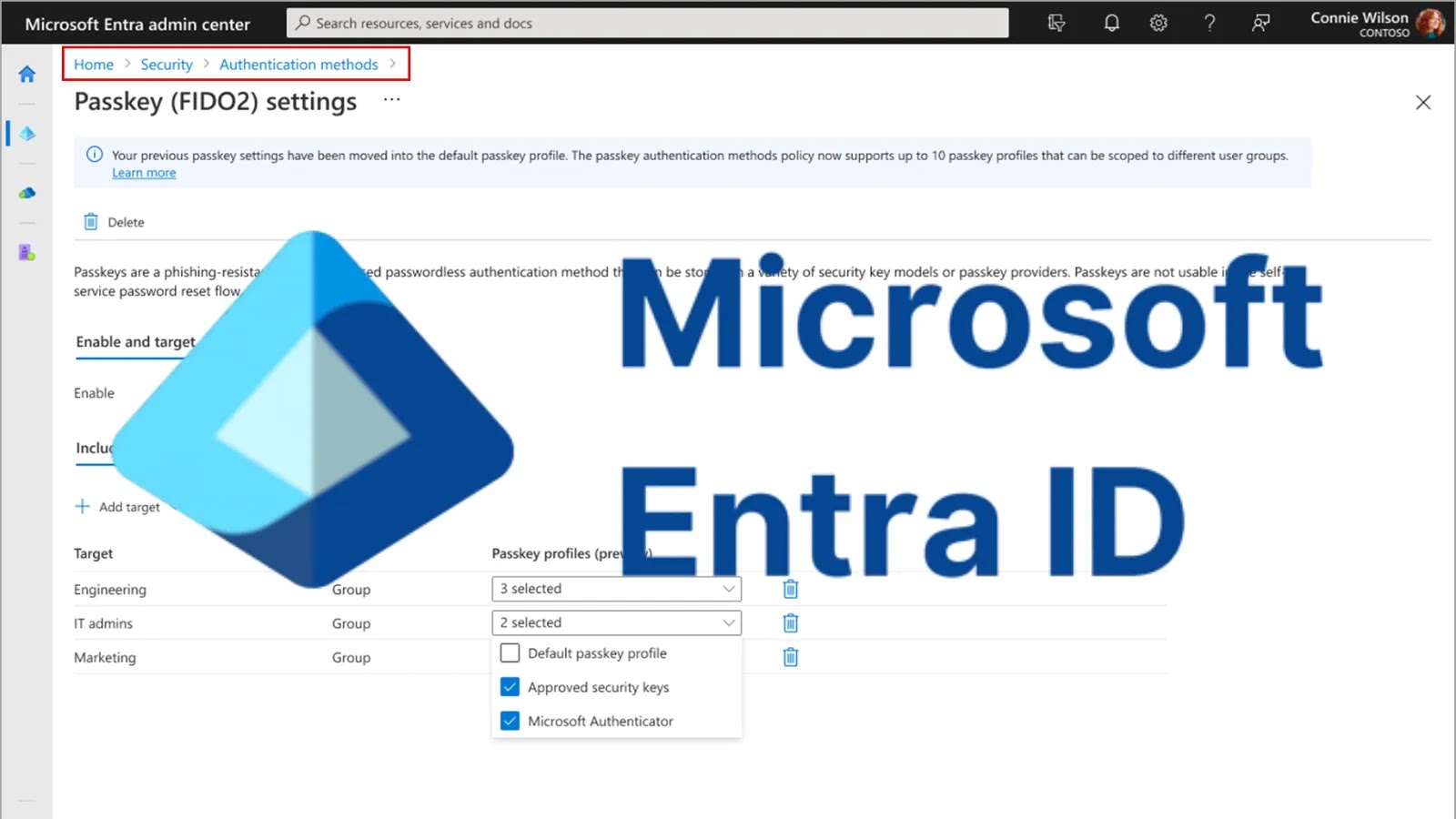
Microsoft has announced a significant update to its identity platform, Microsoft Entra ID, with the introduction of expanded passkey (FIDO2)…
Jun 19, 2025Ravie LakshmananEmail Security / Identity Protection Threat actors with suspected ties to Russia have been observed taking advantage…
Many tech professionals see integrating large language models (LLMs) as a simple process -just connect an API and let it…
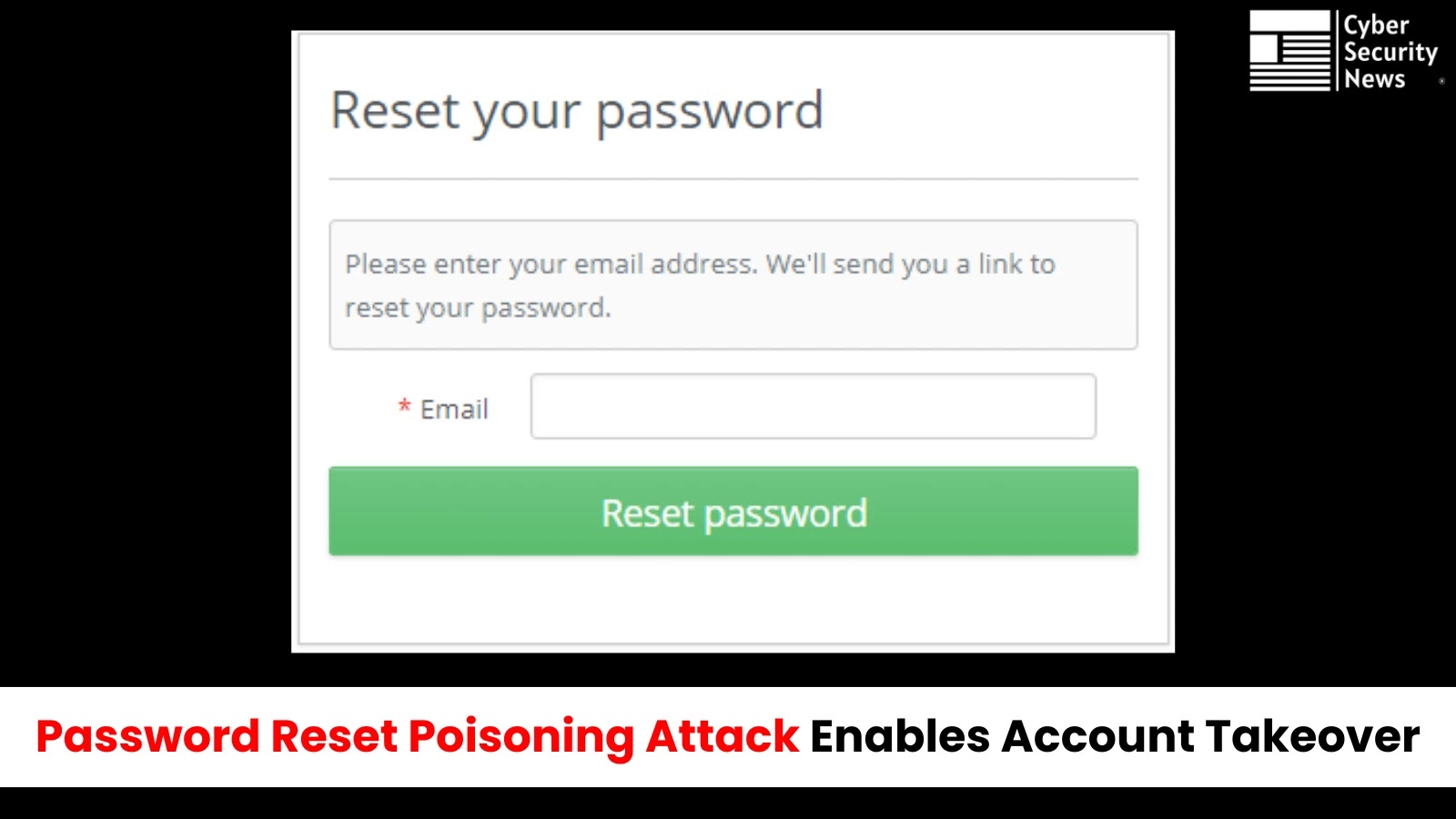
A critical vulnerability in password reset mechanisms has been discovered that allows attackers to completely take over user accounts by…