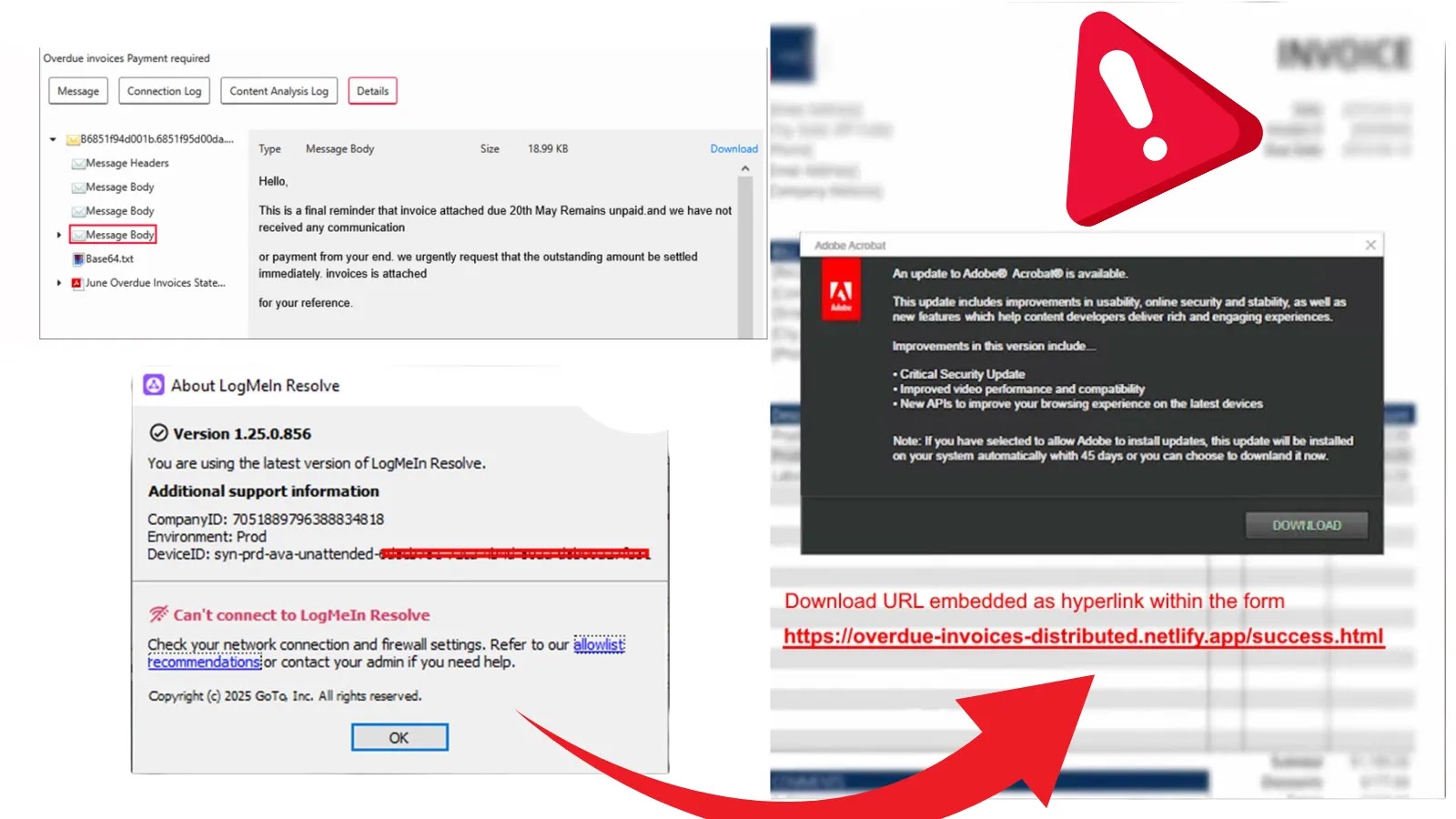
A sophisticated cyberattack campaign has been uncovered, leveraging LogMeIn Resolve remote access software to gain unauthorized control over user systems….
Cybersecurity professionals are facing a sophisticated new threat as Golden SAML attacks emerge as one of the most dangerous yet…
A newly disclosed vulnerability in Cisco’s AnyConnect VPN implementation for Meraki MX and Z Series devices poses a significant risk…
Cloud Software Group has released a security bulletin warning customers of two newly identified vulnerabilities, CVE-2025-5349 and CVE-2025-5777, affecting both…
The Australian Signals Directorate (ASD) has signed a $70-million deal with Amazon Web Services, bringing the cloud provider’s renegotiated government-wide…
Thai authorities have dismantled a sophisticated criminal enterprise operating from the eight-storey Antai Holiday Hotel in Pattaya, unearthing both a…
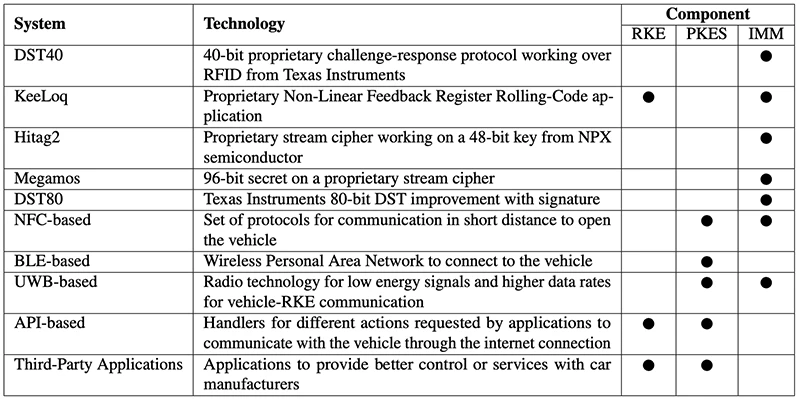
A recent study by researchers at the University of Padova reveals that despite the rise in car thefts involving Remote…
Jun 19, 2025Ravie LakshmananMobile Security / Passwordless Meta Platforms on Wednesday announced that it’s adding support for passkeys, the next-generation…
A member of the notorious Ryuk ransomware operation who specialized in gaining initial access to corporate networks has been extradited…
A newly disclosed vulnerability in Apache Traffic Server (ATS) has raised serious concerns among enterprise users and cloud providers, as…
In this Help Net Security interview, Silviu Asandei, Security Specialist and Security Governance at Sonar, discusses how AI code assistants…
A critical Server-Side Request Forgery (SSRF) vulnerability has been discovered in the @opennextjs/cloudflare package, posing a significant security threat to…