The Cybersecurity and Infrastructure Security Agency (CISA) issued an urgent alert regarding active exploitation of a critical Linux kernel vulnerability,…
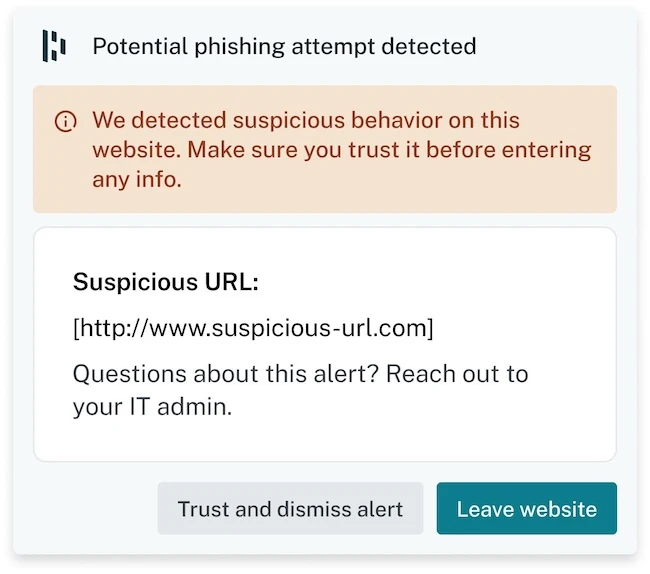
Dashlane introduced AI phishing alerts, an advancement to the Dashlane Omnix platform that protects enterprises and users against threats targeting…
Jun 18, 2025Ravie LakshmananVulnerability / Data Protection Veeam has rolled out patches to contain a critical security flaw impacting its…
Two critical vulnerabilities have been discovered in Citrix NetScaler ADC (formerly Citrix ADC) and NetScaler Gateway (formerly Citrix Gateway), potentially…
As applications become more distributed, traditional monitoring and security tools are failing to keep pace. This article explores how eBPF,…
The roll-out of generative AI and agents will reduce Amazon’s total corporate workforce in the next few years, Andy Jassy,…
Veeam, a leading provider of data protection and backup solutions, disclosed three critical vulnerabilities affecting its widely deployed backup software….
This article showcases free, open-source security tools that support your organization’s teams in red teaming, threat hunting, incident response, vulnerability…
Schneider Electric is reengineering its supply chain and supporting customers to operate more efficiently and sustainably. By focusing on the…
Despite widespread anticipation about AI’s positive impact on workforce productivity, most employees feel they were overpromised on its potential, according…
In partnership with Schneider, Datacom helps customers drive sustainable change using EcoStruxure IT Expert. This platform provides full visibility of…
The world has shifted. Threat actors spend less time exploiting vulnerabilities and more time logging in using stolen credentials. This…