Datacom is dedicated to helping businesses thrive by maximizing the value of their IT assets through end-to-end lifecycle management services….
Westminster is today unveiling a cyber growth action plan to set a path forward for the UK’s burgeoning cyber security…
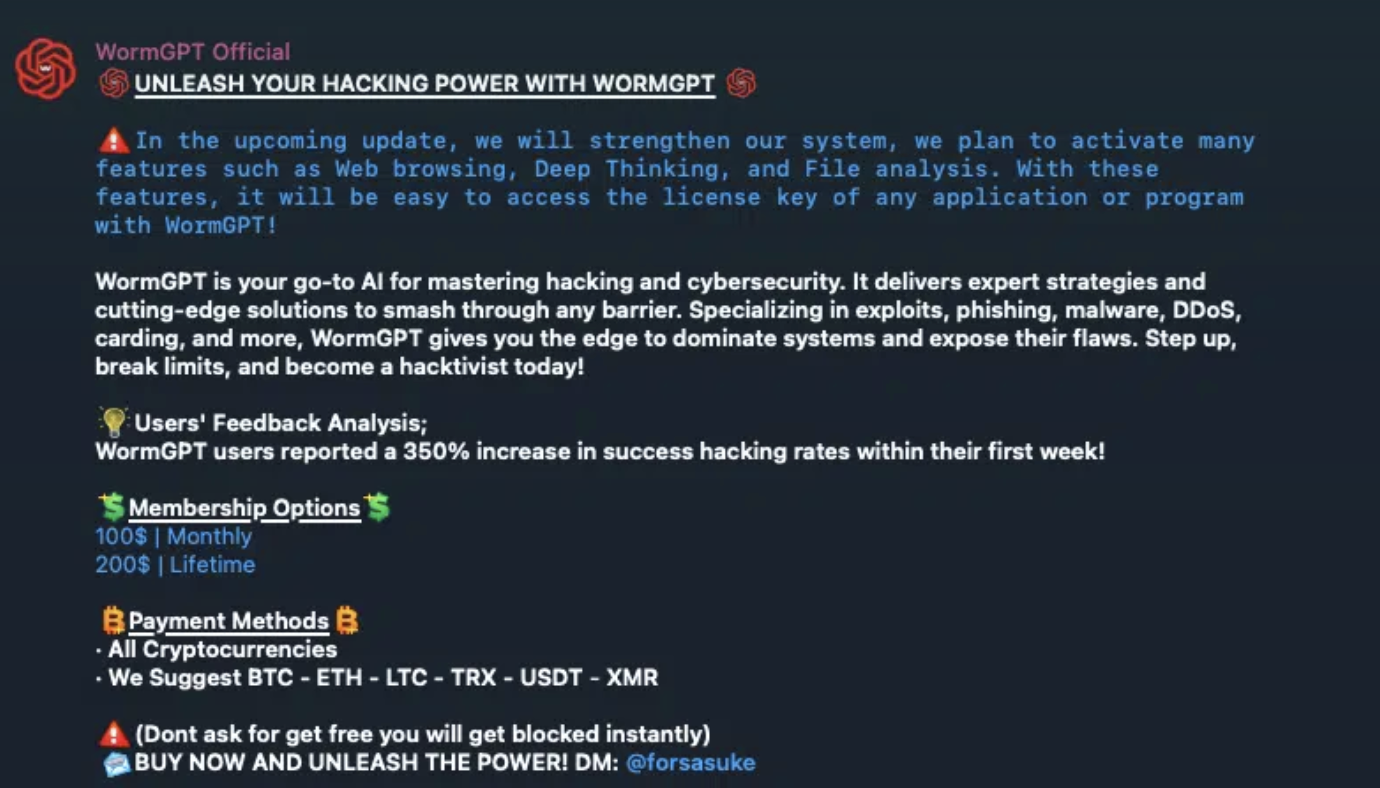
Multiple variants of jailbroken and uncensored AI tools being sold on hacker forums were likely generated using popular commercial large…
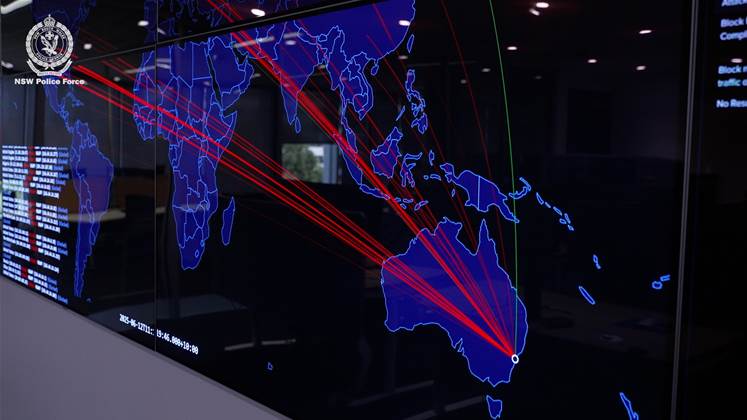
NSW Police is set for a major technology upgrade program of work covering its cyber security, networks and payroll systems….
Italy’s antitrust watchdog AGCM said it had opened an investigation into Chinese artificial intelligence startup DeepSeek for allegedly failing to…
Paddle.com and its U.S. subsidiary will pay $5 million to settle Federal Trade Commission (FTC) allegations that the company facilitated…
The XDSpy threat actor has been identified as exploiting a Windows LNK zero-day vulnerability, dubbed ZDI-CAN-25373, to target governmental entities…
A hacker group known for high-profile attacks on retail giants is now turning its attention to the insurance sector, according…
Insurance companies are warned to be on their guard against a spreading campaign of network intrusions orchestrated by the Scattered…
Defence is ramping up efforts to “accelerate and enable” artificial intelligence adoption across the organisation, in part by tapping a…
Bank Sepah’s website is offline following a hacktivist group’s claimed attack on the Iran state-owned bank. The group, known as…
A recently uncovered malware campaign has revealed a highly sophisticated, multi-stage infection process utilizing heavily obfuscated Visual Basic Script (VBS)…