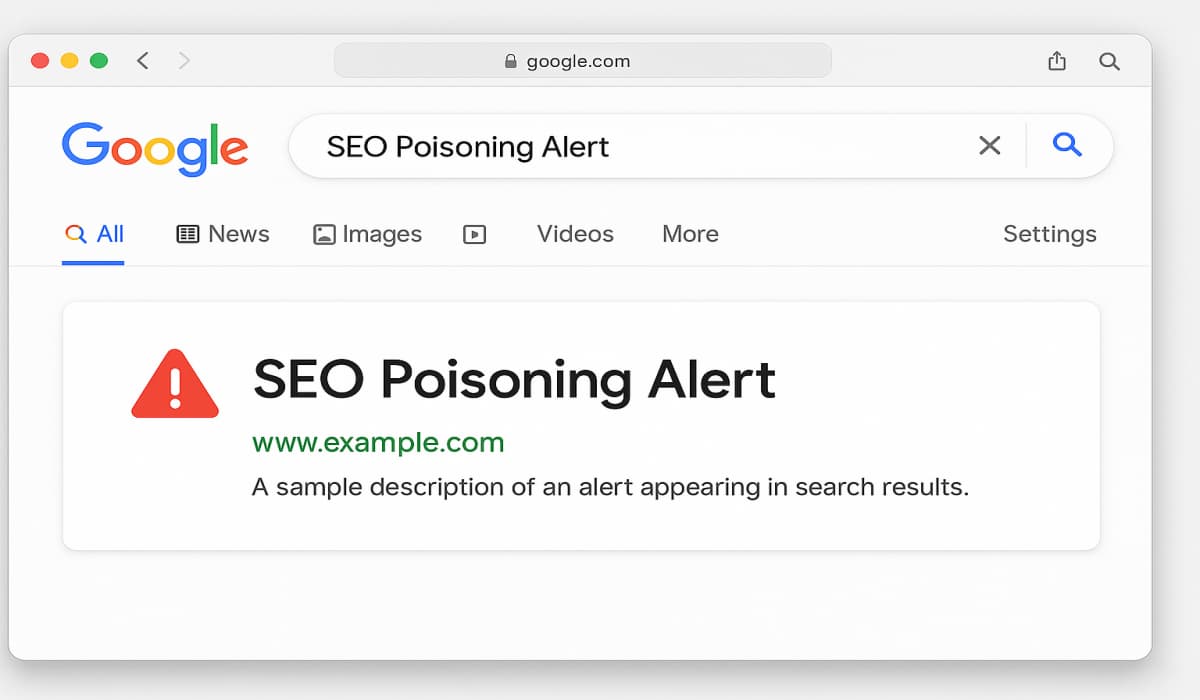
Cybersecurity researchers at Netcraft have discovered a series of new SEO poisoning related attacks exploiting Google’s search results to spread…
The United States should move toward a new model where “target rich, resource-poor” community organizations like hospitals, schools, utilities and…
The UK Information Commissioner’s Office (ICO) has fined genetic testing provider 23andMe £2.31 million ($3.12 million) over ‘serious security failings’…
Listen to the article 3 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
Veeam has released security updates today to fix several Veeam Backup & Replication (VBR) flaws, including a critical remote code…
Security researchers disclosed two critical vulnerabilities in sslh, a widely used protocol multiplexer that enables multiple services—such as SSH, HTTPS,…
Consider this: Berkshire Hathaway, Warren Buffett’s $700 billion conglomerate, operates one of the most influential investor websites on the planet,…
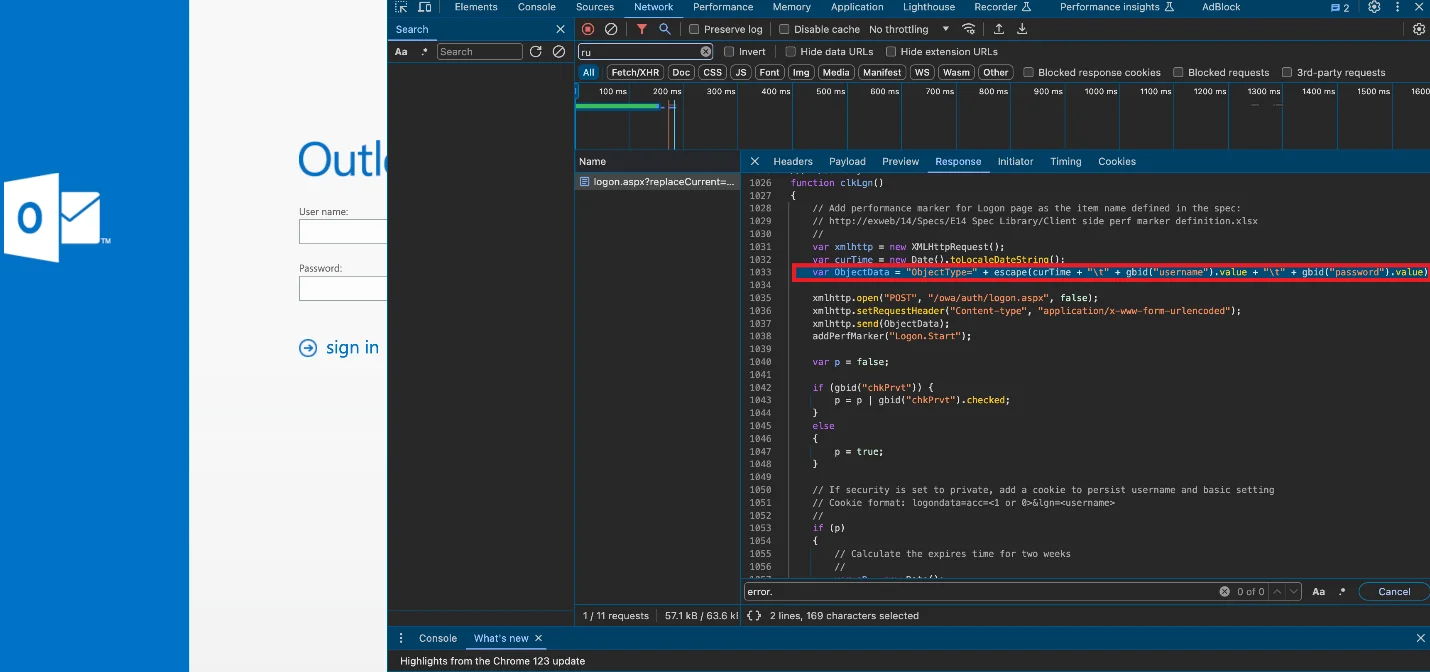
Unknown threat actors have compromised internet-accessible Microsoft Exchange Servers of government organizations and companies around the world, and have injected…
Ransomware has become a highly coordinated and pervasive threat, and traditional defenses are increasingly struggling to neutralize it. Today’s ransomware…
Artificial intelligence (AI) is being used in tennis on and off the court, as players and spectators are served the…
Hackers are exploiting a critical vulnerability in Zyxel’s Internet Key Exchange packet decoder, GreyNoise researchers warned on Monday. The vulnerability,…
A chain of Sitecore Experience Platform (XP) vulnerabilities allows attackers to perform remote code execution (RCE) without authentication to breach…