Jun 17, 2025Ravie LakshmananVulnerability / Enterprise Software Cybersecurity researchers have disclosed three security flaws in the popular Sitecore Experience Platform…
European organizations are facing a sophisticated cyber threat as the Sorillus Remote Access Trojan (RAT) emerges as a prominent weapon…
A newly disclosed vulnerability in BeyondTrust’s Remote Support (RS) and Privileged Remote Access (PRA) products has raised alarms across the…
Jun 17, 2025Ravie LakshmananThreat Intelligence / Identity Security The notorious cybercrime group known as Scattered Spider (aka UNC3944) that recently…
Meta has announced a significant expansion of WhatsApp’s monetization strategy with the introduction of advertising capabilities within the platform’s Updates…
A new wave of cybercrime is exploiting the very backbone of internet trust: search engines. Recent research by Netcraft has…
Lance Mungia, CEO of Waking Universe Films, is the director of “Third Eye Spies“, a 2019 film on Cybercrime Magazine’s Hackers…
For many organizations, Active Directory (AD) service accounts are quiet afterthoughts, persisting in the background long after their original purpose…
A critical authorization bypass vulnerability in ASUS Armoury Crate enables attackers to gain system-level privileges on Windows machines through a…
Threat actors are leveraging deceptive tactics to distribute a fileless variant of AsyncRAT, a notorious remote access Trojan. Discovered during…
Zoomcar Holdings, a peer-to-peer car-sharing company that connects car owners with renters, has revealed that its information systems were accessed…
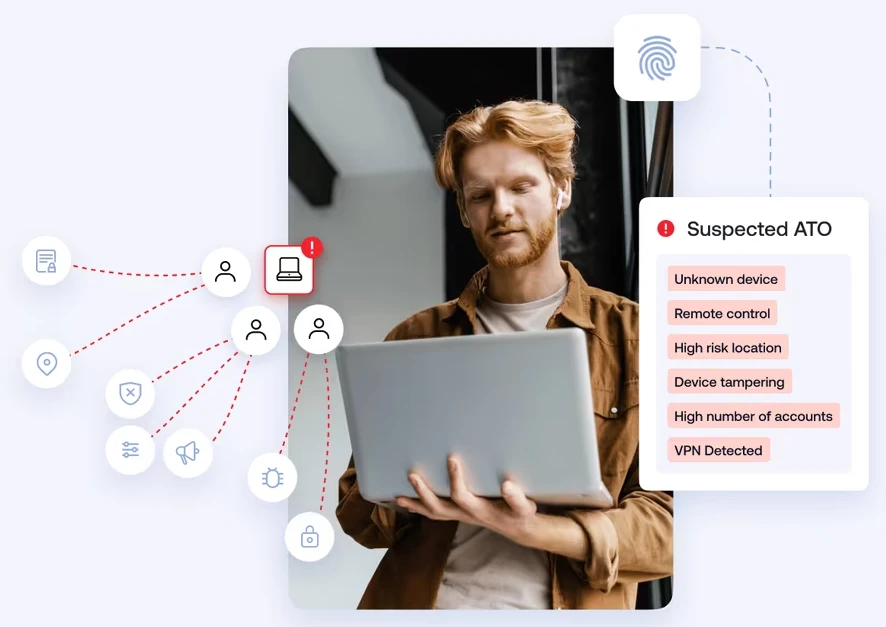
Sumsub is expanding its Fraud Prevention solution with advanced Device Intelligence, enhanced by the Fingerprint platform. Designed to identify threats before…