A former intern at the UK’s intelligence agency GCHQ has been sentenced to seven and a half years in prison…
When CISOs think about risk, they usually think about cloud platforms, laptops, and data centers. But live events like conferences,…
Five key technology system “incidents” at the Australian Securities Exchange (ASX) in the past decade has prompted a fresh inquiry…
Multiple critical security vulnerabilities affecting Apache Tomcat web servers, including two high-severity flaws enabling denial-of-service (DoS) attacks and one moderate-severity…
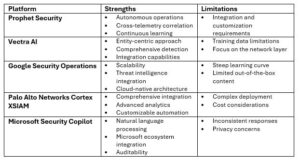
As threats evolve in sophistication and frequency while cyber skills gaps persist, Security Operations Centres (SOCs) are increasingly turning to…
The Apache Software Foundation has released critical security updates to address four newly discovered vulnerabilities in Apache Tomcat, one of…
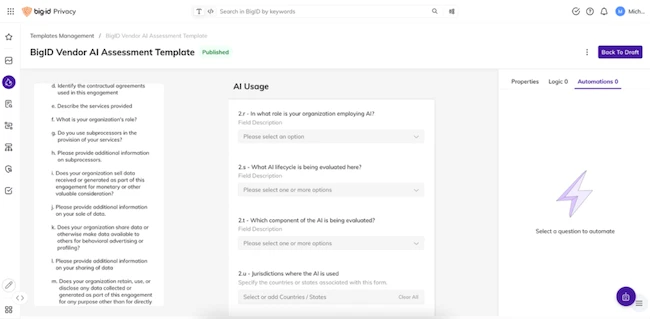
BigID launched Vendor AI Assessment, a solution designed to help organizations identify, evaluate, and manage the risks introduced by third-party…
Jun 17, 2025Ravie LakshmananPrivacy / Data Protection Meta Platforms on Monday announced that it’s bringing advertising to WhatsApp, but emphasized…
CBA is looking to support its security engineers as well as 1200-plus “security champions” embedded across the bank with generative…
A sudden and highly coordinated wave of cyberattacks has struck Zyxel firewall and VPN devices worldwide, as hackers exploit a…
In this Help Net Security interview, Paolo del Mundo, Director of Application and Cloud Security at The Motley Fool, discusses…
Canada’s WestJet Airlines is investigating a cyber security incident that has disrupted access to its mobile app and some internal…