Calgary-based WestJet Airlines, Canada’s second-largest carrier, is grappling with the fallout from a significant cybersecurity incident that has disrupted access…
Listen to the article 3 min This audio is auto-generated. Please let us know if you have feedback. Dive Brief:…
Authorities across Europe toppled Archetyp Market, the longest-standing online drug marketplace, and arrested its lead administrator, Europol announced Monday. The…
Email accounts of several Washington Post journalists were compromised in a cyberattack believed to have been carried out by a…
International law enforcement agencies have successfully dismantled one of the world’s largest darknet marketplaces, “Archetyp Market,” in a coordinated operation…
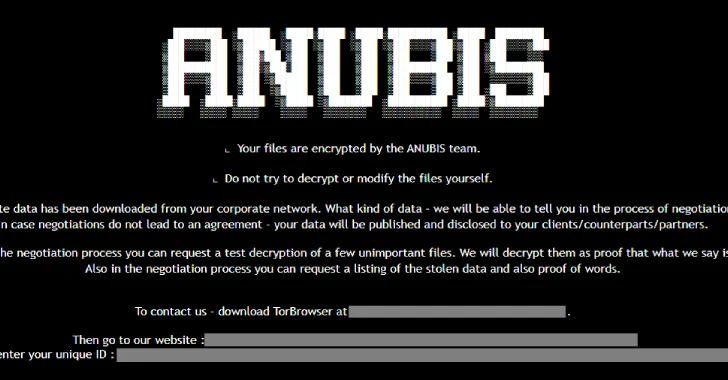
The BERT ransomware group, first detected in April 2025 but active since mid-March, has expanded its reach from targeting Windows…
Jun 16, 2025Ravie LakshmananMalware / Ransomware An emerging ransomware strain has been discovered incorporating capabilities to encrypt files as well…
Zoomcar Holdings (Zoomcar) has disclosed that unauthorized accessed its system led to a data breach impacting 8.4 million users. The…
A former GCHQ intern has been sentenced to seven-and-a-half years in prison after copying top secret data files onto his…
A targeted cyberattack has struck The Washington Post, compromising the email accounts of several of its journalists and raising new…
European law enforcement agencies have dismantled Archetyp Market, a long-running dark web platform used primarily for drug sales, following a…
Vulnerabilities affecting the SinoTrack GPS tracking platform may allow attackers to keep tabs on vehicles’ location and even perform actions…