A high-severity security flaw has been disclosed in ServiceNow’s platform that, if successfully exploited, could result in data exposure and…
GreyNoise has discovered an undiscovered version of a scraper botnet with more than 3,600 distinct IP addresses worldwide, which is…
In a move set to redefine the way organizations manage data access and implement zero trust, Lepide launched Lepide Protect, an…
Security researchers revealed the dangers of GitHub Device Code Phishing—a technique that leverages the OAuth 2.0 Device Authorization Grant flow….
In this Help Net Security interview, David Warburton, Director at F5 Labs, discusses how the EU’s Post-Quantum Cryptography (PQC) roadmap…
A severe security vulnerability in McDonald’s AI-powered hiring system has exposed the personal information of potentially 64 million job applicants…
A shocking security vulnerability in McDonald’s AI-powered hiring system has exposed the personal information of millions of job applicants, after…
Shopping on a fake online store can lead to more than a bad purchase. It could mean losing money, having…
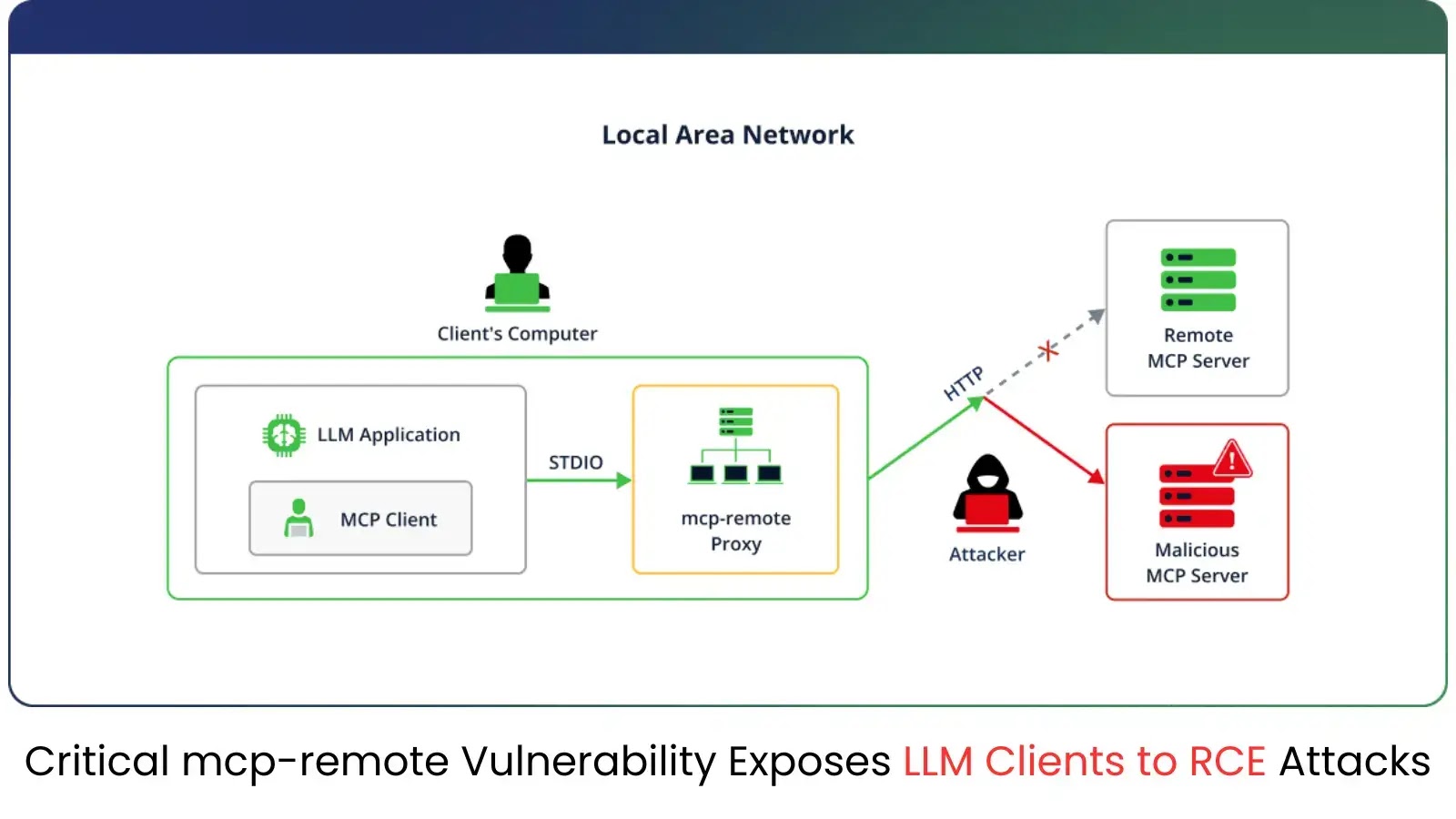
The JFrog Security Research team has discovered a critical security vulnerability in mcp-remote, a widely used tool that enables Large…
There has been a significant increase in the global trend of corporations planning to integrate cybersecurity under the CISO or…
Only 23% of organizations are confident that they have very high visibility of their software supply chain, according to LevelBlue’s…
Viva Energy has gone live with a greenfield HR and payroll system powered by Dayforce, enabling it to move off…